The conclusion of last month’s post noted “There was a noticeable absence of government-directed Internet disruptions in April. That is not to say that there were none, but those that did occur were not significant enough to be observed through publicly available tools.” This trend, which had also been observed over the prior few months, continued into May. (Unfortunately, this is not the case for June, but that will be covered in next month’s post.)
In May, a power outage in Venezuela once again disrupted Internet connectivity across the country, and a cyclone impacted connectivity in Bhutan. Fiber and submarine cable cuts (and repairs) caused Internet disruptions across multiple countries, as did unspecified network issues.
Power Outage
On May 5, a Tweet from Internet monitoring firm Netblocks confirmed that a power outage in Venezuela had disrupted Internet connectivity across multiple states within the country. Unfortunately, such power outages are a relatively common occurrence in Venezuela, and frequently impact Internet connectivity across the country. The Oracle Internet Intelligence and CAIDA IODA country-level graphs below show that the primary impact was to the active probing and traffic metrics, but the BGP metric also saw a brief nominal drop. The aggregated state-level CAIDA graph below illustrates the impact on active probing measurements to endpoints within the listed Venezuelan states – a multi-hour Internet disruption was measured in each of them.

Oracle Internet Intelligence Country Statistics graph for Venezuela, May 5 
CAIDA IODA graph for Venezuela, May 5 
CAIDA IODA graph for multiple Venezuelan states, May 5
Weather
Internet connectivity was disrupted in Bhutan on May 20 & 21 because of damage to Bhutan Telecom infrastructure caused by Cyclone Amphan. As shown in both the Oracle and CAIDA graphs below, the disruption began around 12:00 GMT on May 20 and lasted for approximately 24 hours, though a brief restoration of connectivity occurred between 17:40-19:40 GMT. The infrastructure damage did not cause a complete country-wide outage, but the graphs show that all three measured metrics were impacted.

Oracle Internet Intelligence Country Statistics graph for Bhutan, May 20-21 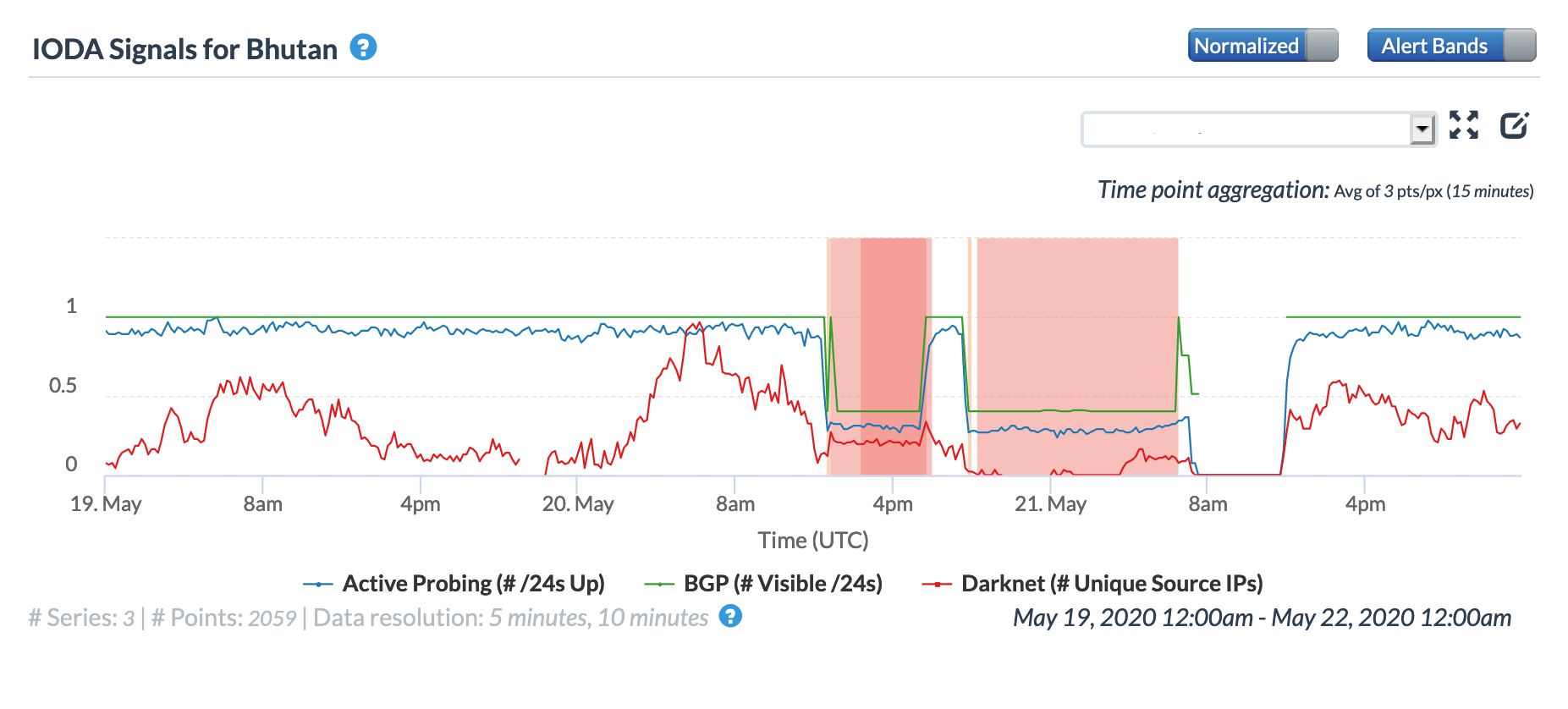
CAIDA IODA graph for Bhutan, May 20-21
The impact was more significant, however, at a network level. The CAIDA graphs below for AS18024 (Bhutan Telecom) and AS17660 (DrukNet/Bhutan Telecom) show complete outages for all three measured metrics.
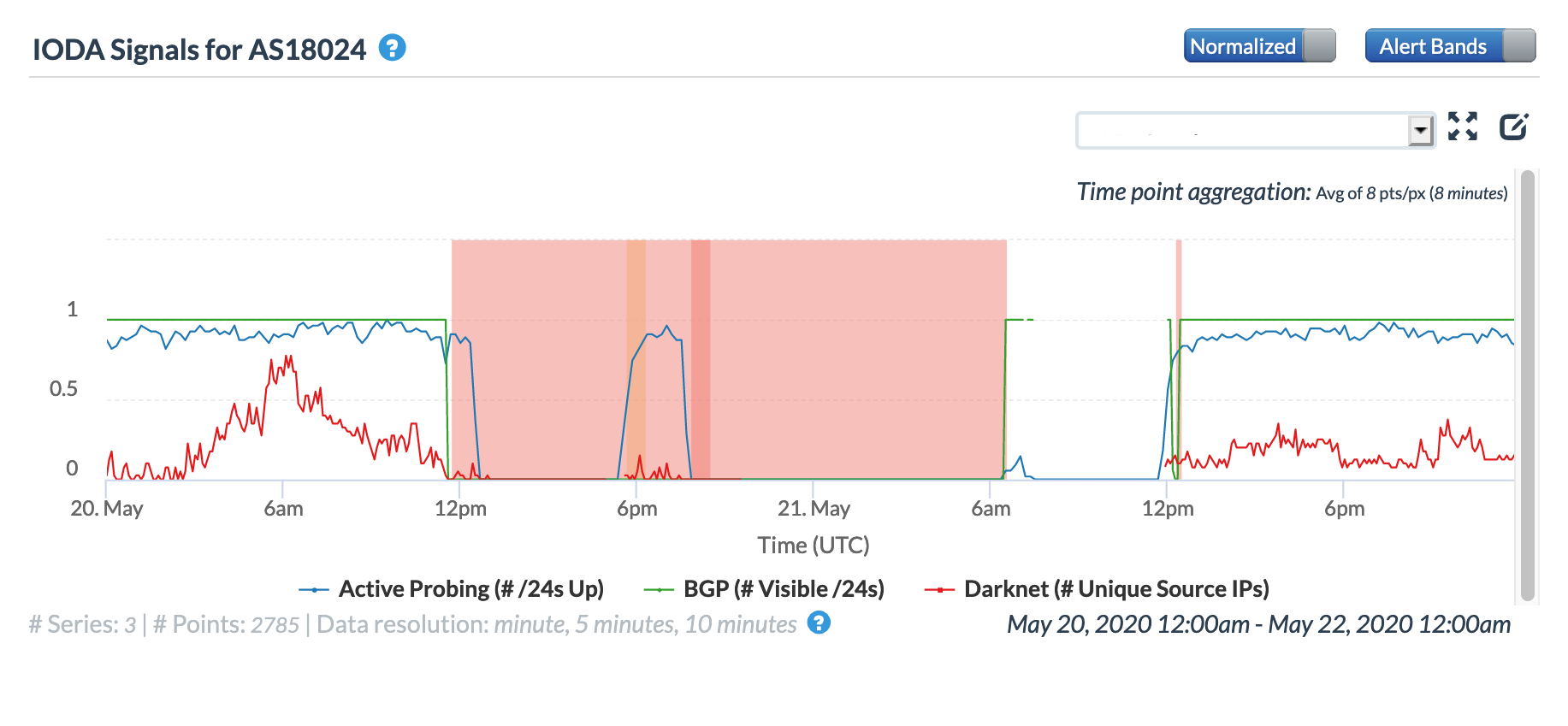
CAIDA IODA graph for AS18024 (Bhutan Telecom), May 20-21 
CAIDA IODA graph for AS17660 (DrukNet/Bhutan Telecom), May 20-21
Fiber/Cable Cut
Fiber optic cables cut by vandals disrupted Internet connectivity for tens of thousands of users in France on May 5 & 6. The cables that were damaged impacted connectivity for both home and business subscribers, as well as cloud provider Scaleway. The Oracle graphs below show the impact on traceroute measurements to endpoints within three French network providers. In each case, traceroutes through the network’s primary upstream provider drop to near zero, but begin reaching the target network through an alternate upstream almost immediately. Nominal increases in latency are also evident, but for these network providers, redundant connectivity meant that the overall impact was nominal.

Oracle Internet Intelligence Traffic Shifts graph for AS2094 (Renater), May 5-6 
Oracle Internet Intelligence Traffic Shifts graph for AS31178 (Celeonet SAS), May 5-6 
Oracle Internet Intelligence Traffic Shifts graph for AS34949 (IDLINE SAS), May 5-6
According to a Twitter thread from Venezuelan journalist Fran Monroy Moret, repairs to a submarine cable resulted in a multi-hour Internet disruption across multiple network providers in Venezuela on May 17. Multiple submarine cables land in Venezuela, but the thread does not mention which cable was being repaired. However, references to CenturyLink within the thread could indicate that the cable in question is either the Americas-II or the South American Crossing (SAC), as CenturyLink is listed among the owners of both.
The Twitter thread suggested that the disruption would last eight hours, from 02:00 – 10:00 local time (06:00 – 14:00 GMT). At a country level, the eight hour-disruption is most evident in the BGP metric across both the Oracle and CAIDA graphs, as the impact to the active probing and traffic-related metrics appeared to be briefer in duration. Local network provider Movistar (AS6306) also experienced a disruption for the full repair duration, as shown in the graphs below. However, local providers Inter (AS21826) and Net Uno (AS11562) appeared to experience briefer disruptions, occurring in the middle of the repair period and primarily evident in the active probing and BGP metrics.

Oracle Internet Intelligence Country Statistics graph for Venezuela, May 17 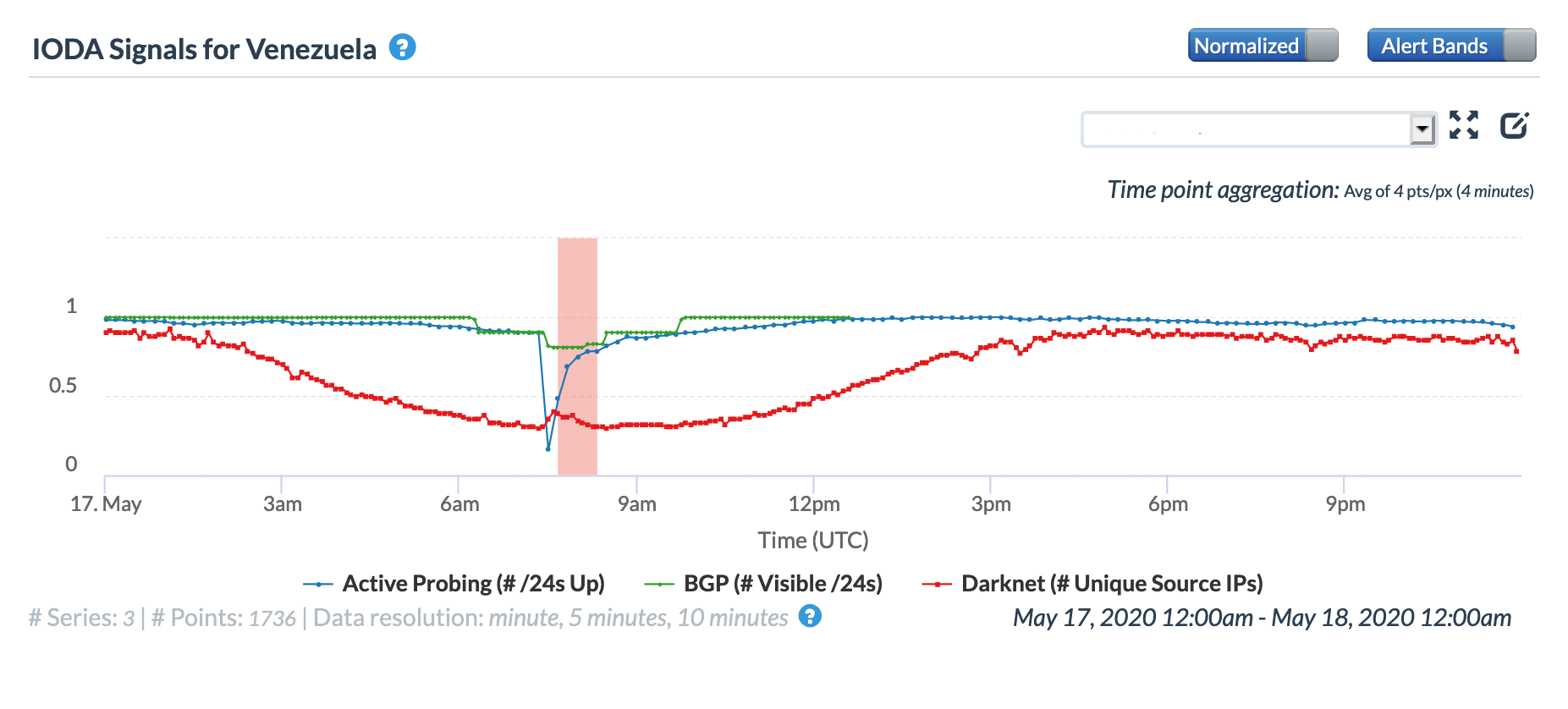
CAIDA IODA graph for Venezuela, May 17 
Oracle Internet Intelligence Traffic Shifts graph for AS6306 (Movistar), May 17 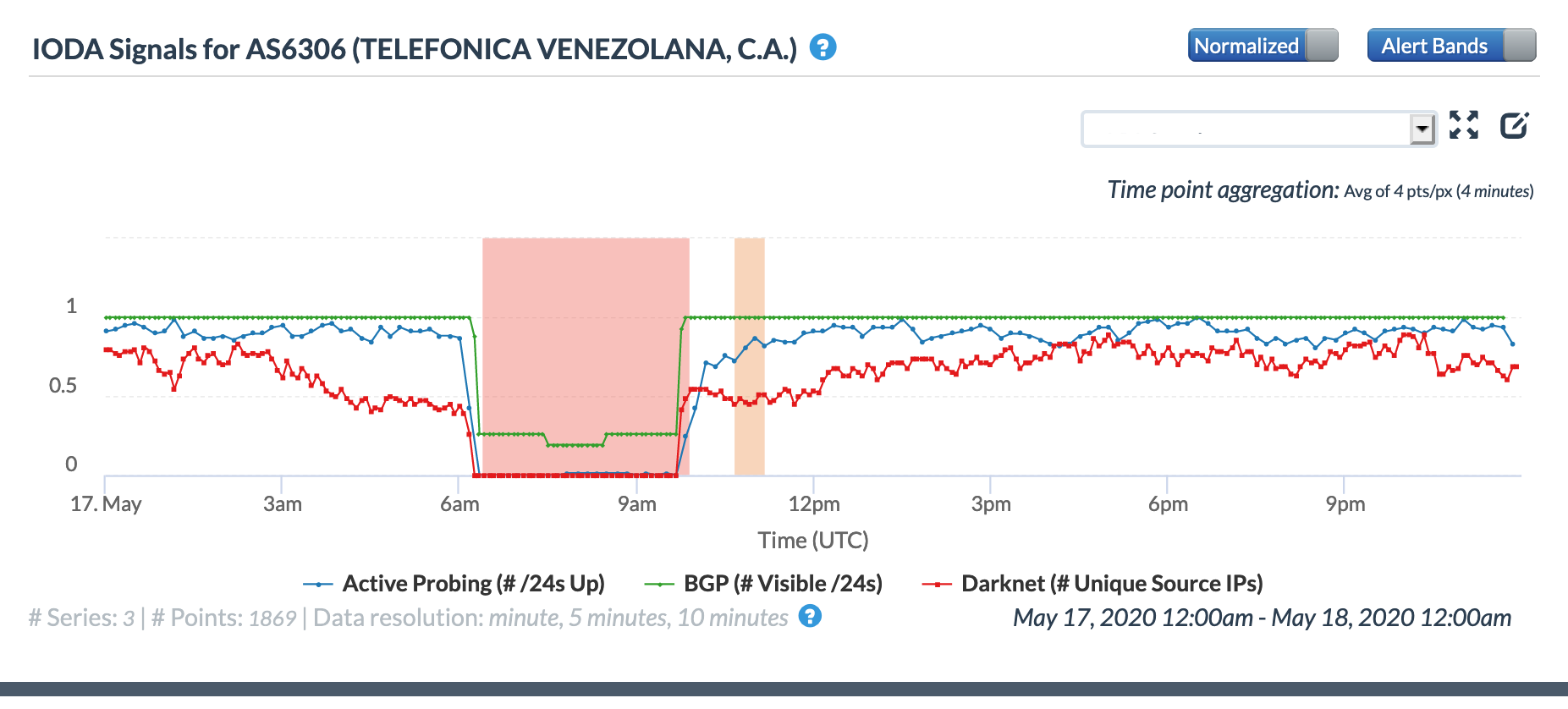
CAIDA IODA graph for AS6306 (Movistar), May 17 
Oracle Internet Intelligence Traffic Shifts graph for AS21826 (Inter), May 17 
CAIDA IODA graph for AS21826 (Inter), May 17 
Oracle Internet Intelligence Traffic Shifts graph for AS11562 (Net Uno), May 17 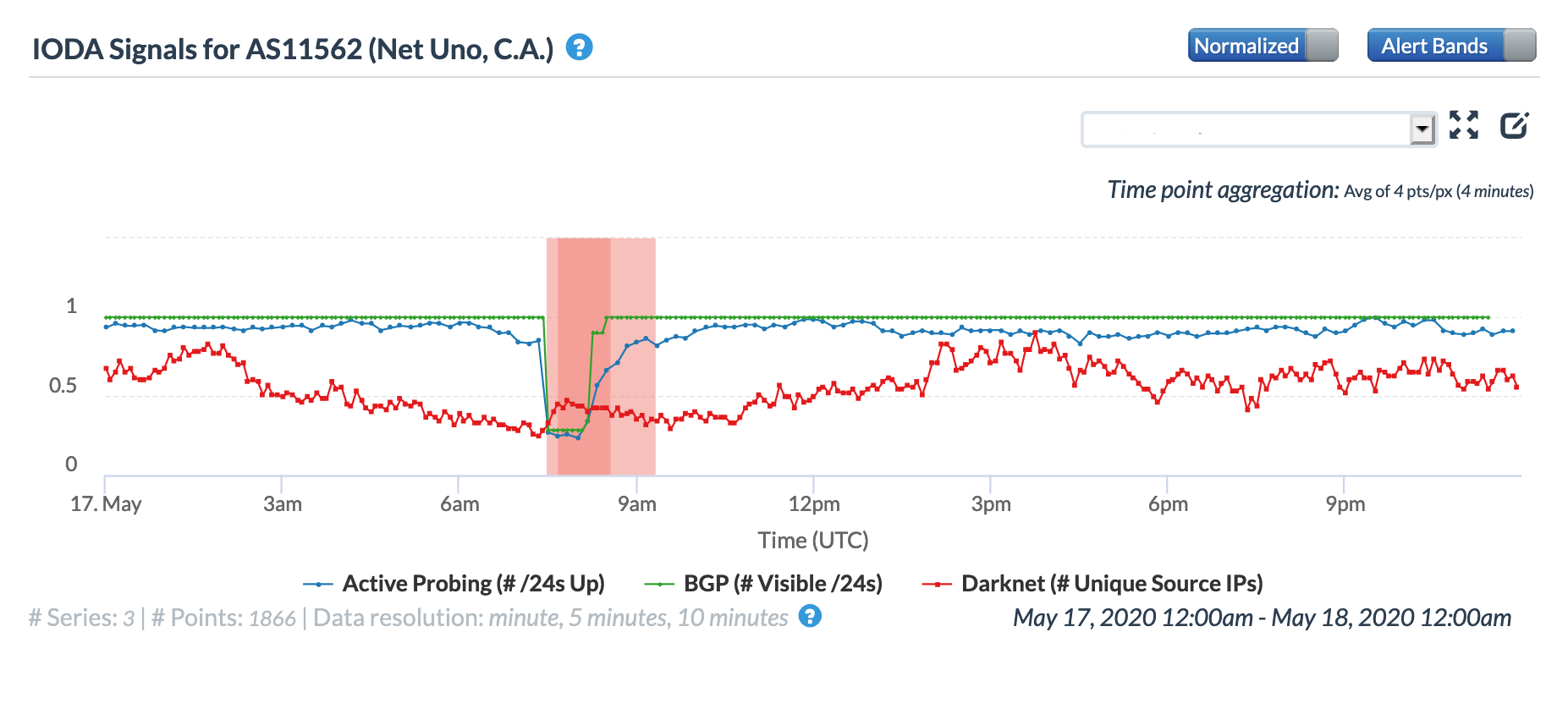
CAIDA IODA graph for AS11562 (Net Uno), May 17
A May 19 Tweet from Oracle Internet Intelligence highlighted Internet disruptions detected across multiple countries, and an associated Tweet pointed to the ACE submarine cable as the likely culprit. Impacted countries included Sierra Leone, Niger, Mauritania, Liberia, and the Gambia. The graphs below show that the disruptions began around 01:30 GMT, lasting approximately 90 minutes, although the impacts linger for several additional hours in Niger’s graphs.

Oracle Internet Intelligence Country Statistics graph for Sierra Leone, May 19 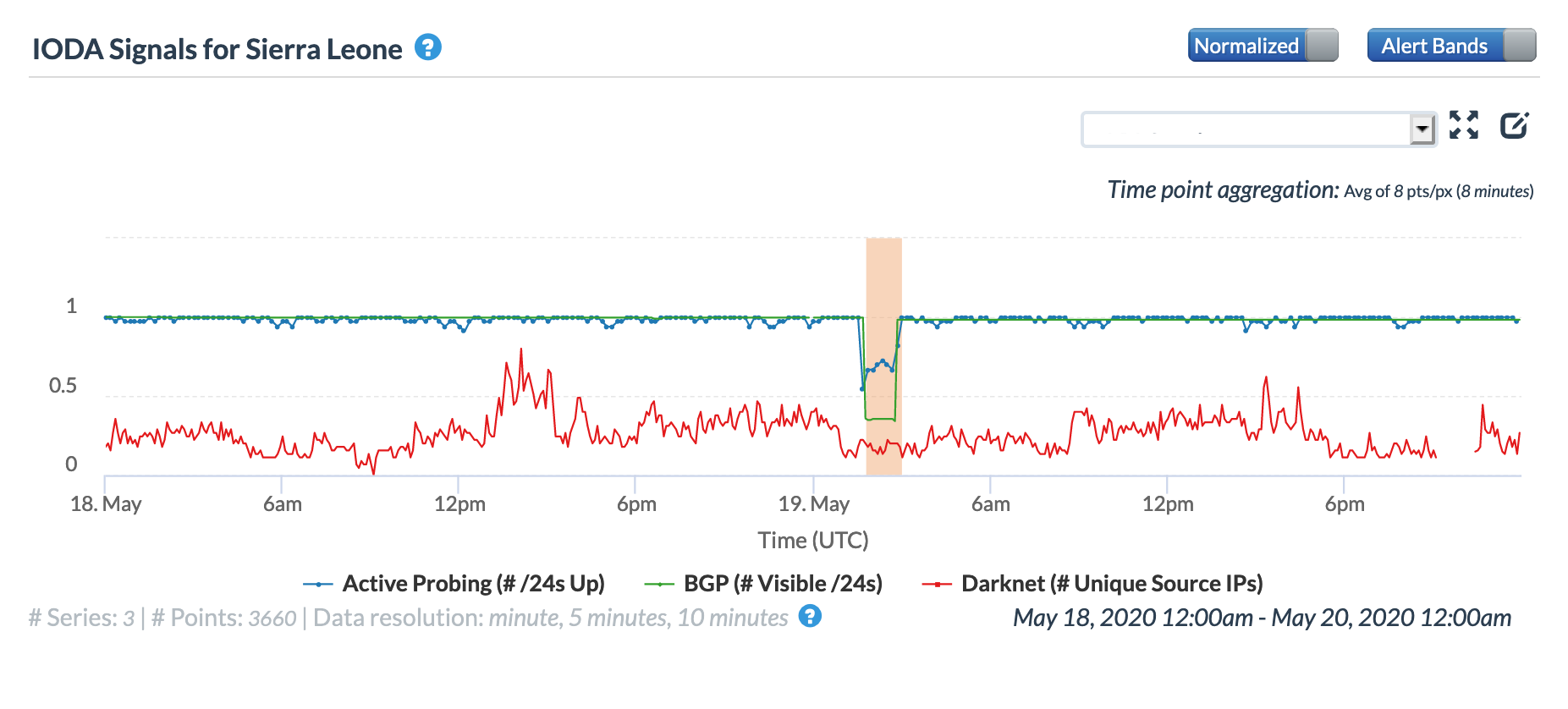
CAIDA IODA graph for Sierra Leone, May 19 
Oracle Internet Intelligence Country Statistics graph for Niger, May 19 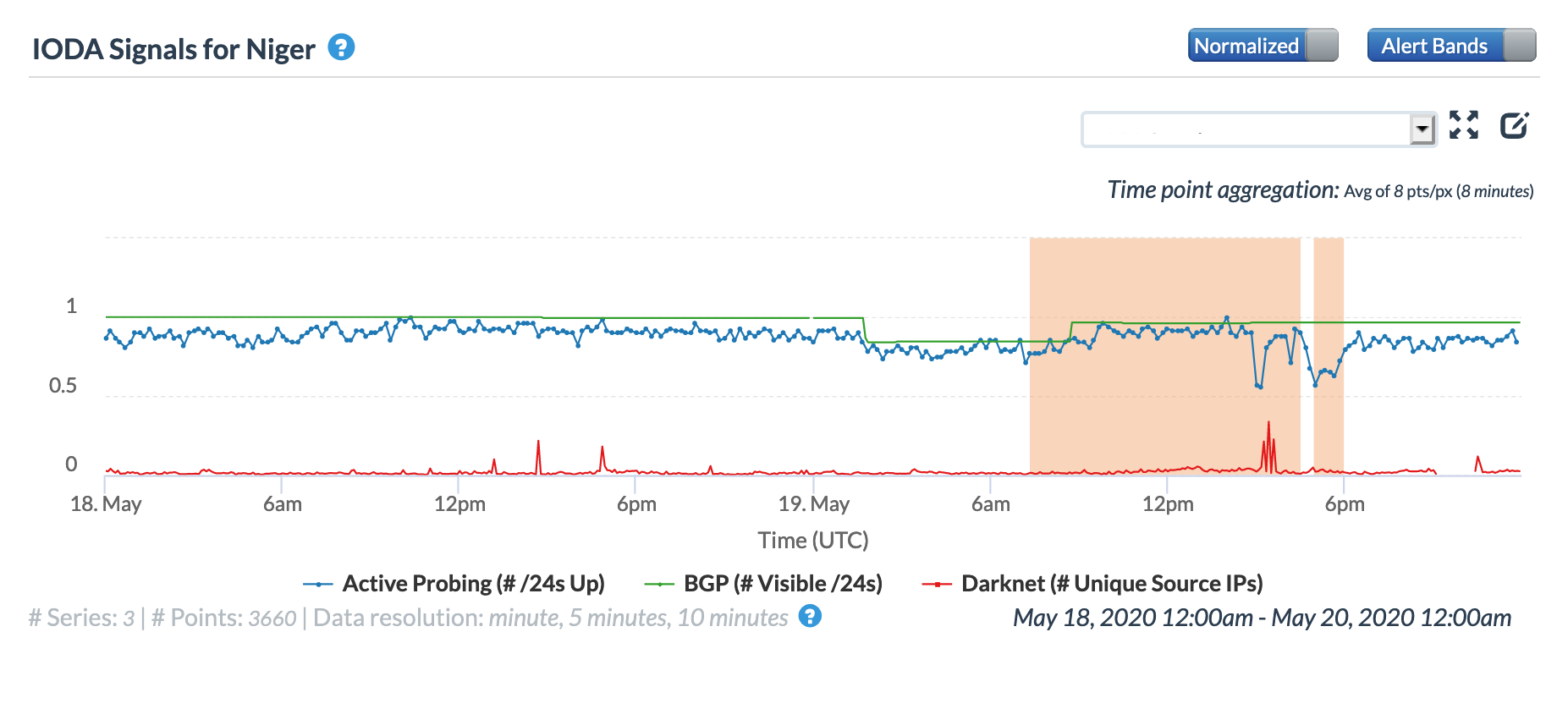
CAIDA IODA graph for Niger, May 19 
Oracle Internet Intelligence Country Statistics graph for Mauritania, May 19 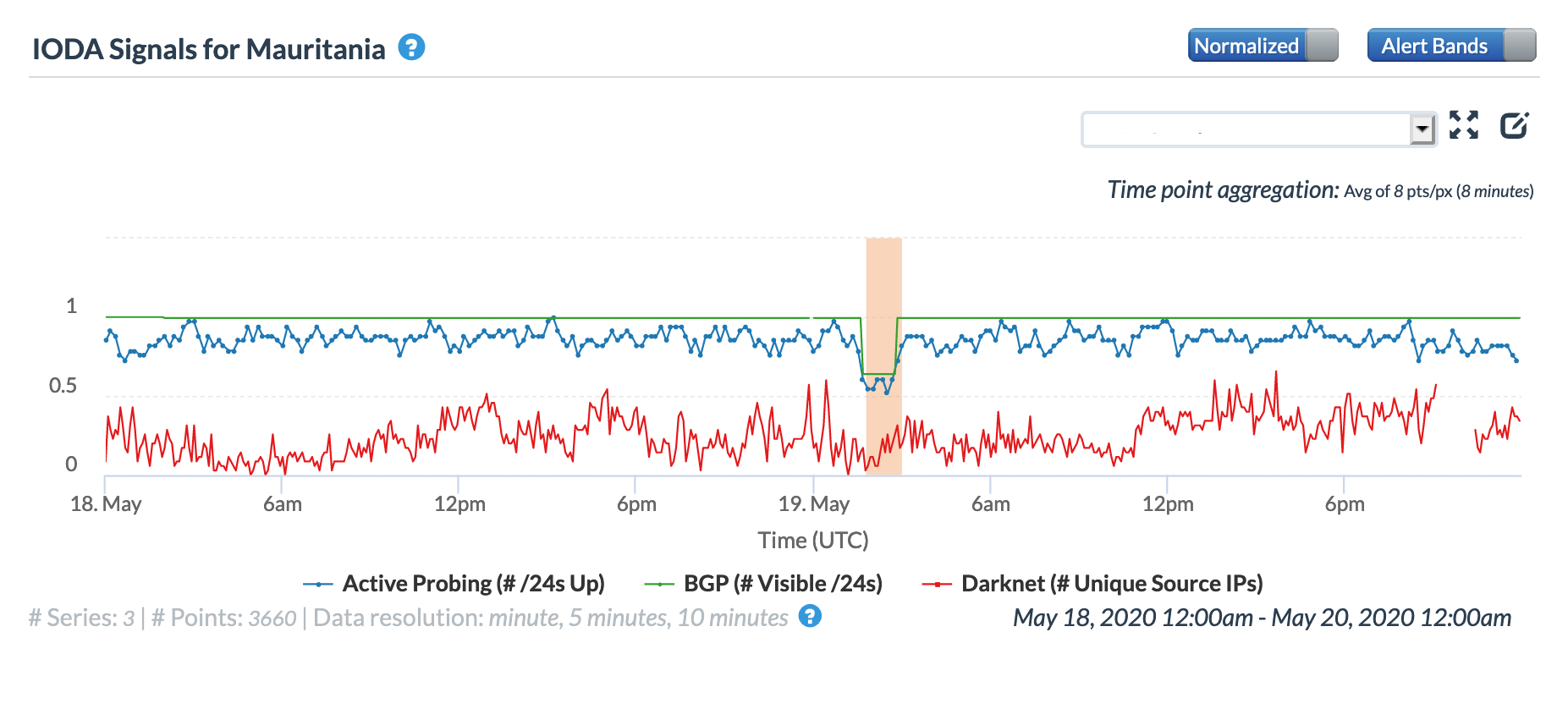
CAIDA IODA graph for Mauritania, May 19 
Oracle Internet Intelligence Country Statistics graph for Liberia, May 19 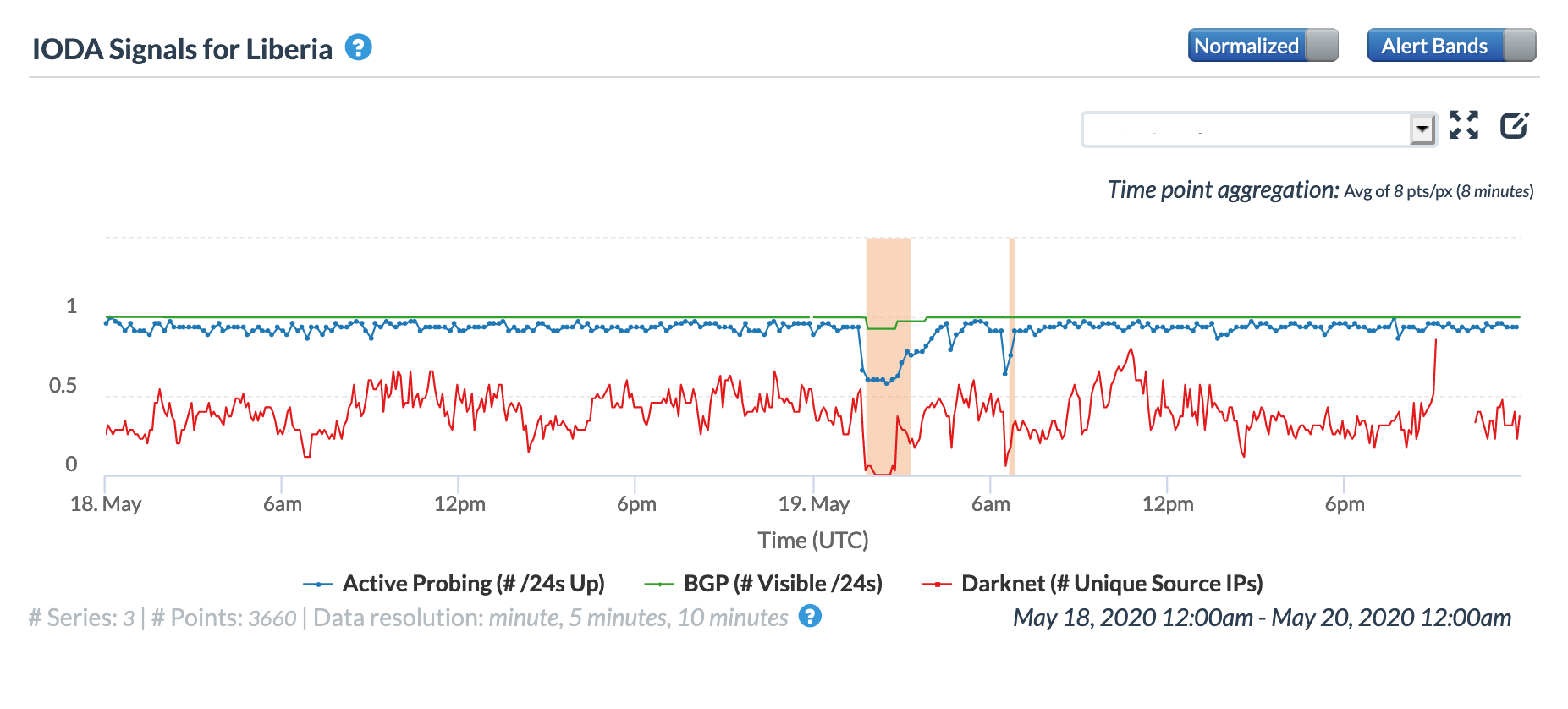
CAIDA IODA graph for Liberia, May 19 
Oracle Internet Intelligence Country Statistics graph for the Gambia, May 19 
CAIDA IODA graph for the Gambia, May 19
On May 27, a brief Internet disruption was detected on French Polynesia starting just after 12:00 GMT and lasting for about an hour, as shown in the graphs below. The active probing, BGP, and traffic metrics were impacted across both Oracle and CAIDA measurements. The Honotua submarine cable is the island nation’s primary international Internet connection, connecting it to Hawaii, and it is likely that problems with this cable were the cause of the observed disruption. The network-level graphs below all show AS36149 (Hawaiian Telecom Services Company) as an upstream provider, and a drop was seen in the number of successful traceroutes across this network in all three graphs.

Oracle Internet Intelligence Country Statistics graph for French Polynesia, May 27 
CAIDA IODA graph for French Polynesia, May 27

Oracle Internet Intelligence Traffic Shifts graph for AS56017 (Vitu), May 27 
Oracle Internet Intelligence Traffic Shifts graph for AS9471 (Onati), May 27 
Oracle Internet Intelligence Traffic Shifts graph for AS55943 (Onati), May 27
Network Issues
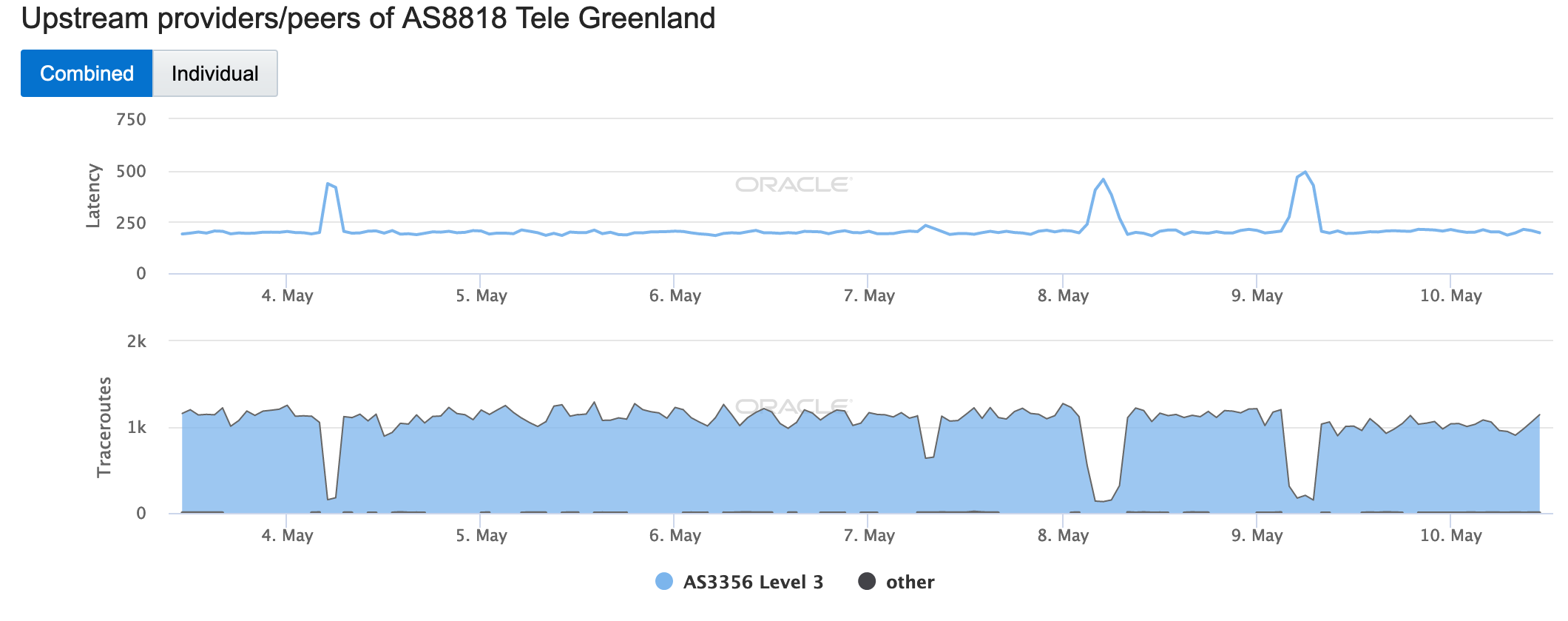
According a May 7 post to its Facebook page, Greenland network provider TELE-POST suffered an unspecified network issue that disrupted Internet connectivity for DSL users.
Visible in the graphs below, it appears that the disruption began around 06:30 GMT, and lasted for just over six hours. However, after the issue was addressed and connectivity restored, TELE-POST customers continued to have issues with Wi-Fi connectivity, leading to a series of additional Facebook posts (1, 2, 3) that provided situational updates and guidance on resetting modems.

Oracle Internet Intelligence Country Statistics graph for Greenland, May 7 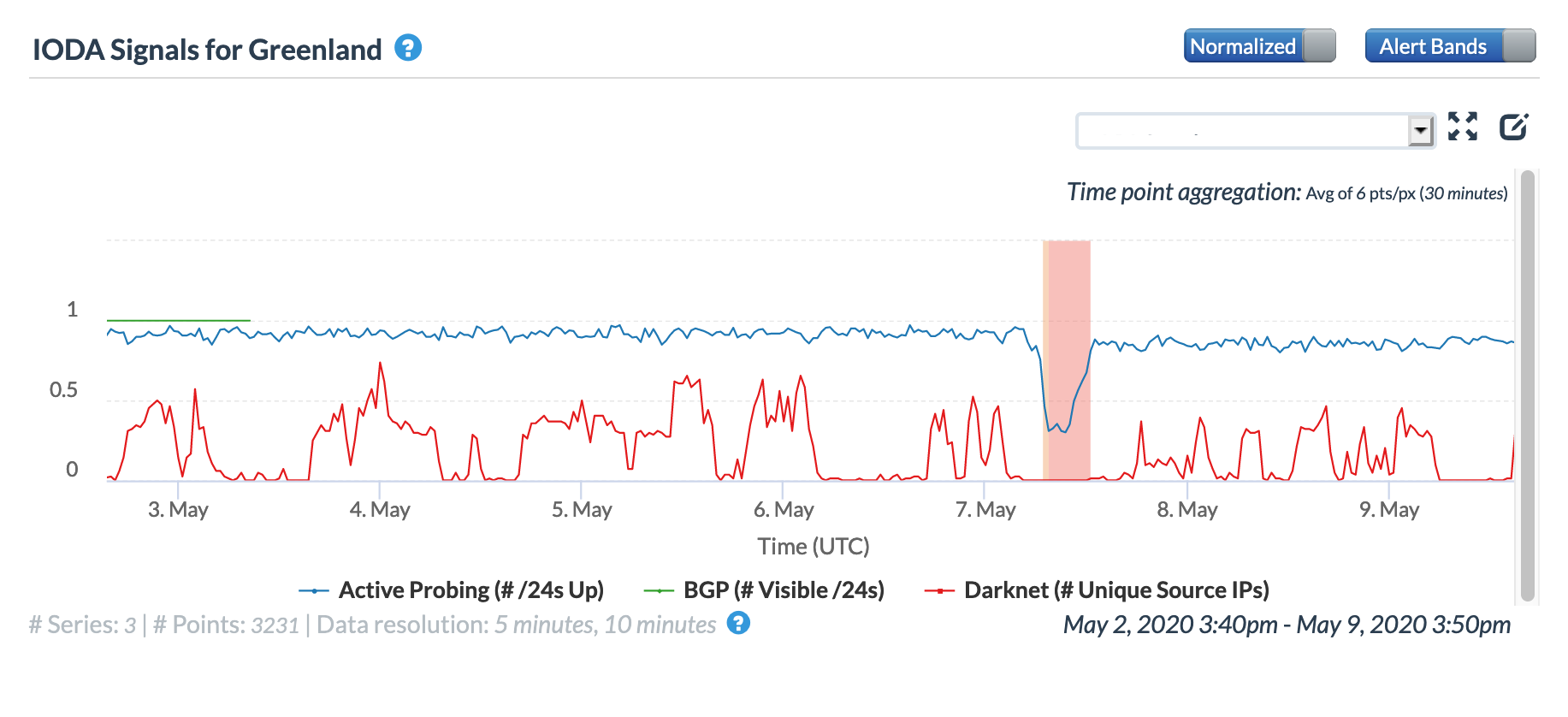
CAIDA IODA graph for Greenland, May 7 
CAIDA IODA graph for AS8818 (TELE-POST / Tele Greenland), May 7
The French territory of St. Pierre and Miquelon, located south of the Canadian island of Newfoundland, experienced a multi-hour Internet disruption on May 10. The graphs below show that the disruption began around 13:00 GMT, with connectivity restored about five hours later. Both the Oracle and CAIDA graphs show a significant decline in the active probing metrics, and the Oracle graph shows a similar decline in the BGP metric.

Oracle Internet Intelligence Country Statistics graph for St. Pierre and Miquelon, May 10 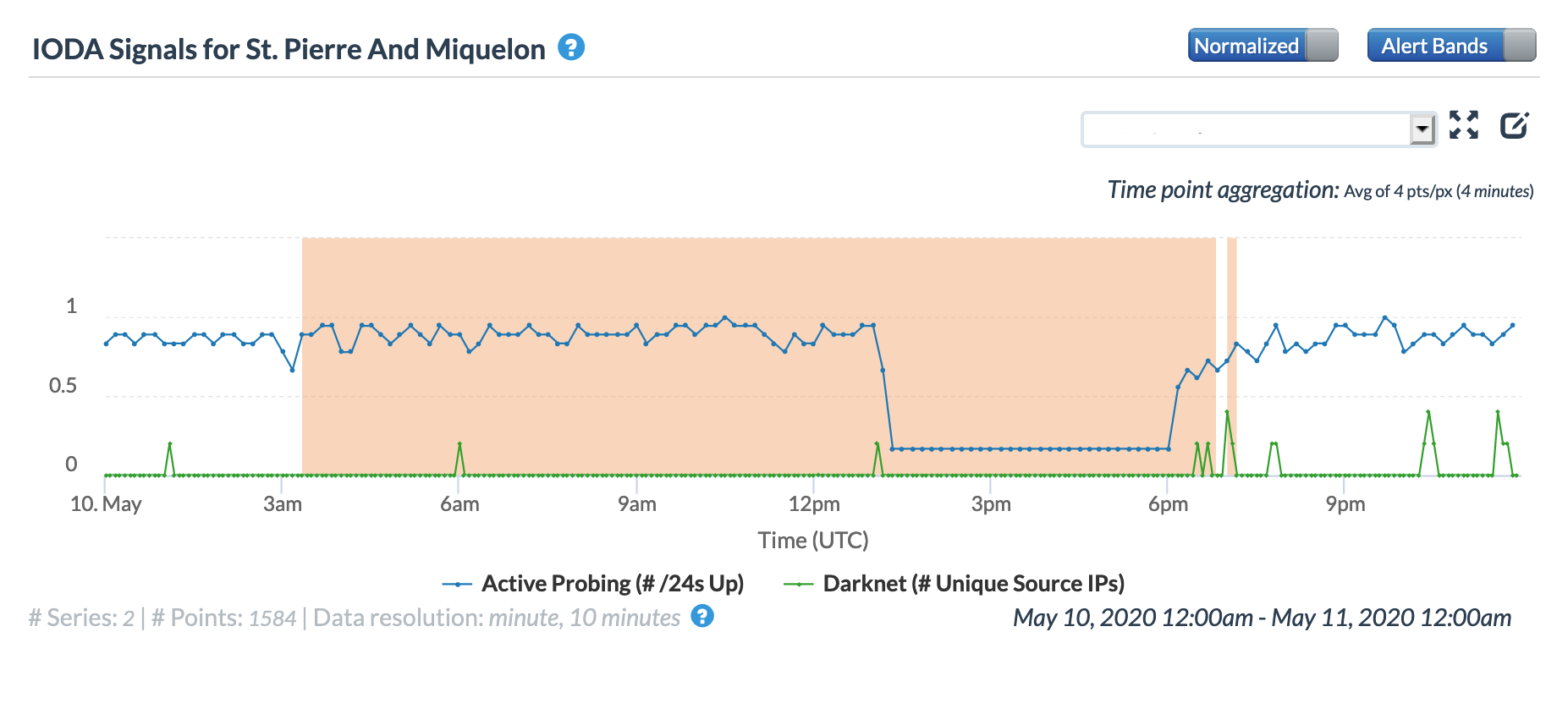
CAIDA IODA graph for St. Pierre and Miquelon, May 10
We're aware that customers in Harbour Breton and parts of Burin Peninsula are currently experiencing an interruption in service. We're investigating the cause and working to restore service as quickly as possible. We appreciate your patience and will update later this afternoon.
— Eastlink Support (@EastlinkSupport) May 10, 2020
The Tweet shown above from the support account of Canadian Internet provider Eastlink notes that the network was experiencing a service interruption. This interruption is evident in the Oracle graph below for AS11260 (Eastlink), and also in the graph below for AS3695 (SPM Telecom), which uses Eastlink as its primary upstream provider.

Oracle Internet Intelligence Traffic Shifts graph for AS11260 (Eastlink), May 10 
Oracle Internet Intelligence Traffic Shifts graph for AS3695 (SPM Telecom), May 10
Thousands of TalkTalk users in the United Kingdom experienced an Internet disruption for a couple of hours during the morning of May 29. While the disruption was covered in articles published on the Web sites of the Independent and the Daily Mail, neither included any information on the root cause of the issue. TalkTalk acknowledged the problem in Tweeted replies to customer complaints, but did not provide any information on what caused the disruption.
The graphs below show that the disruption began approximately 09:00 GMT and lasted for approximately 90 minutes, which is consistent with the timeline in the published reports. The active probing metric in the CAIDA graphs shows an obvious decline, while the Darknet metric remained largely unaffected, as did the BGP metric.

CAIDA IODA graph for AS13285 (TalkTalk), May 29 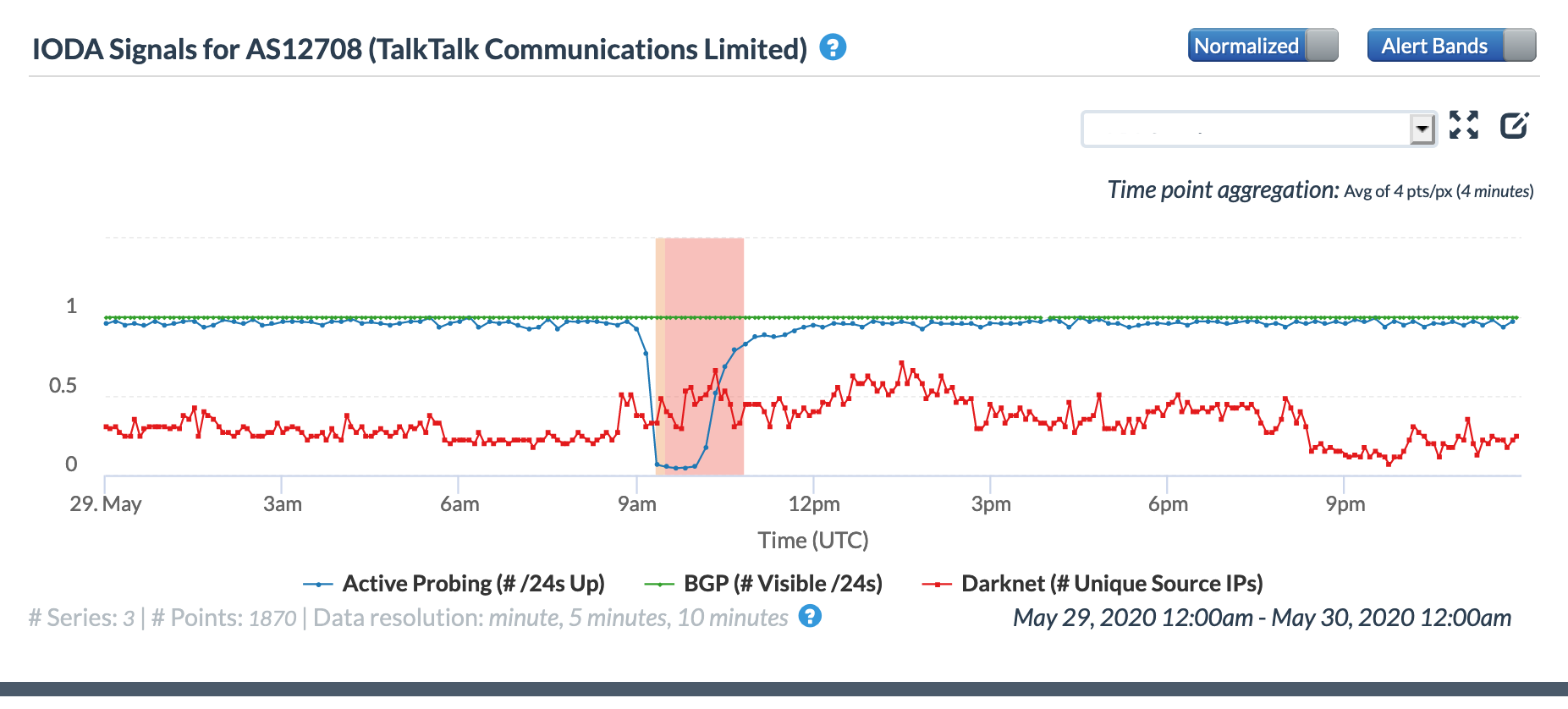
CAIDA IODA graph for AS12708 (TalkTalk), May 29 
Fing Internet Alerts outage graph for TalkTalk, May 29
Conclusion
Over the last several month, COVID-19 lockdowns and social distancing have driven nearly everyone onto the Internet for school, work, shopping, and entertainment. Given this increased reliance on the Internet for everyday life, it is imperative that network providers do a better job of communicating about Internet shutdowns, outages, and other disruptions that impact their networks. Ideally, this communication would be proactive and public, posted on status pages/sites (and archived for future reference), as well as to associated Twitter accounts and Facebook pages. (And by acknowledging issues in a timely fashion, and communicating about them openly, providers can control the narrative around such events, preventing rumors from spreading, and even potentially buying themselves a little customer goodwill.)
At the very least, providers need to respond in a timely fashion to inquiries about Internet disruptions observed on their networks made via social media and/or e-mail. In this day and age, given the importance of Internet connectivity, ignoring these inquiries is simply unacceptable.
]]>Power Outages
Internet connectivity in Venezuela was disrupted several times over the course of the month due to multiple widespread power outages. On September 12, NetBlocks reported that Caracas was experiencing its second power outage in two days, corroborated by a Tweet from @CORPOELECinfo, an account associated with Venezuela’s national electric corporation.
The impact of these two outages can be seen in the figures below for the Capital District and Miranda – Caracas straddles both states. A minor disruption can be seen mid-day on September 11, with a more significant disruption occurring mid-day on September 12.

CAIDA IODA graph for the Capitol District of Venezuela, September 11-12 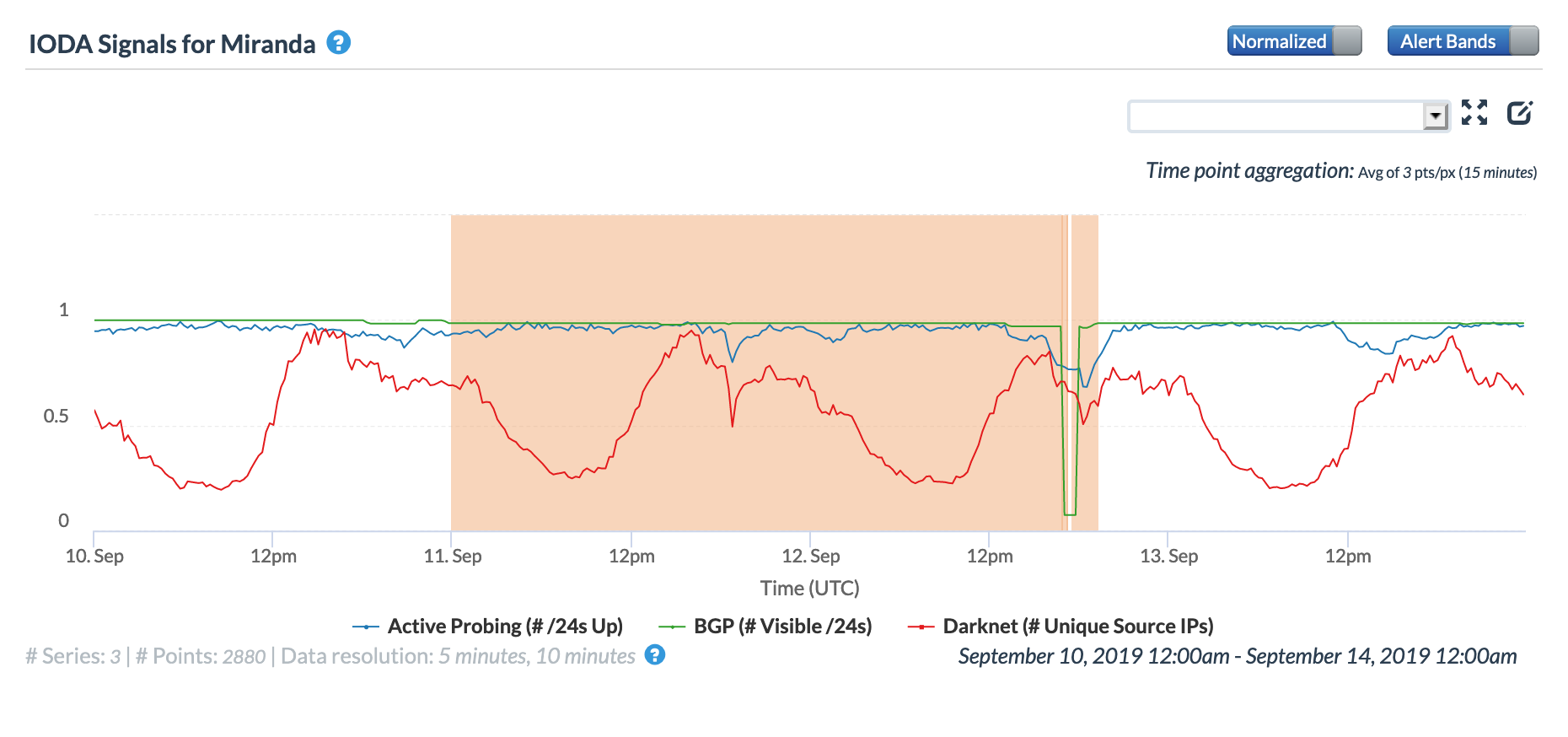
CAIDA IODA graph for Miranda,Venezuela, September 11-12
Just over a week later, another significant power outage disrupted Internet connectivity in Venezuela for several hours, as shown in the figures below. Starting around 1500 UTC on September 20, the disruption lasted until approximately 0100 UTC on September 21.

Oracle Internet Intelligence Country Statistics graph for Venezuela, September 20-21 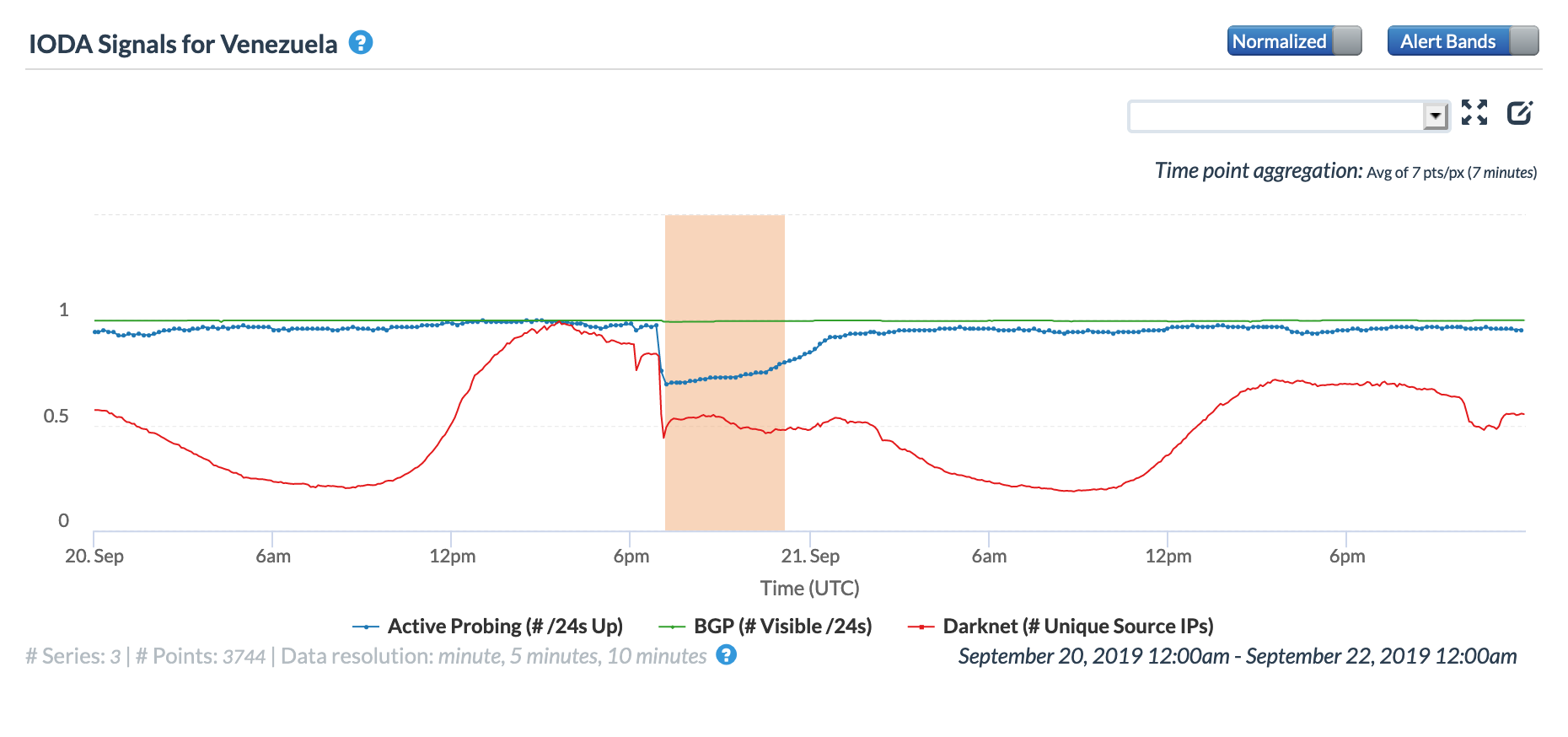
CAIDA IODA graph for Venezuela, September 20-21
The disruption was also very visible at a local level as the CAIDA IODA graphs below for the Venezuelan states of Lara, Tachira, and Zulia show, with marked drops in the Active Probing and Darknet metrics.

CAIDA IODA graph for Lara, Venezuela, September 20-21 
CAIDA IODA graph for Tachira, Venezuela, September 20-21 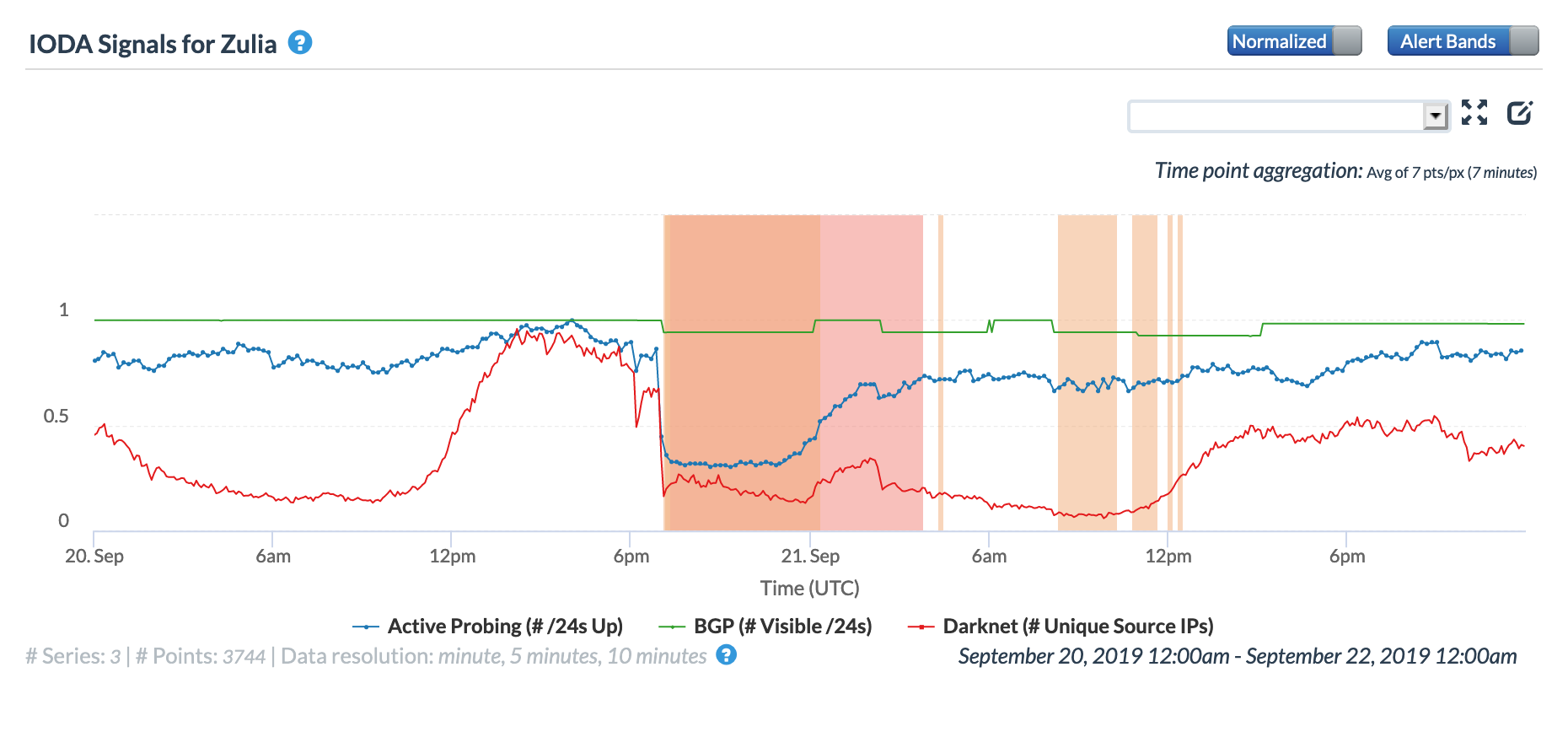
CAIDA IODA graph for Zulia, Venezuela, September 20-21
Brief power outages early in the day (GMT) on September 24 and mid-afternoon (GMT) on September 27 again caused Internet disruptions visible at a country level, as seen in the figures below.

CAIDA IODA graph for Venezuela, September 24 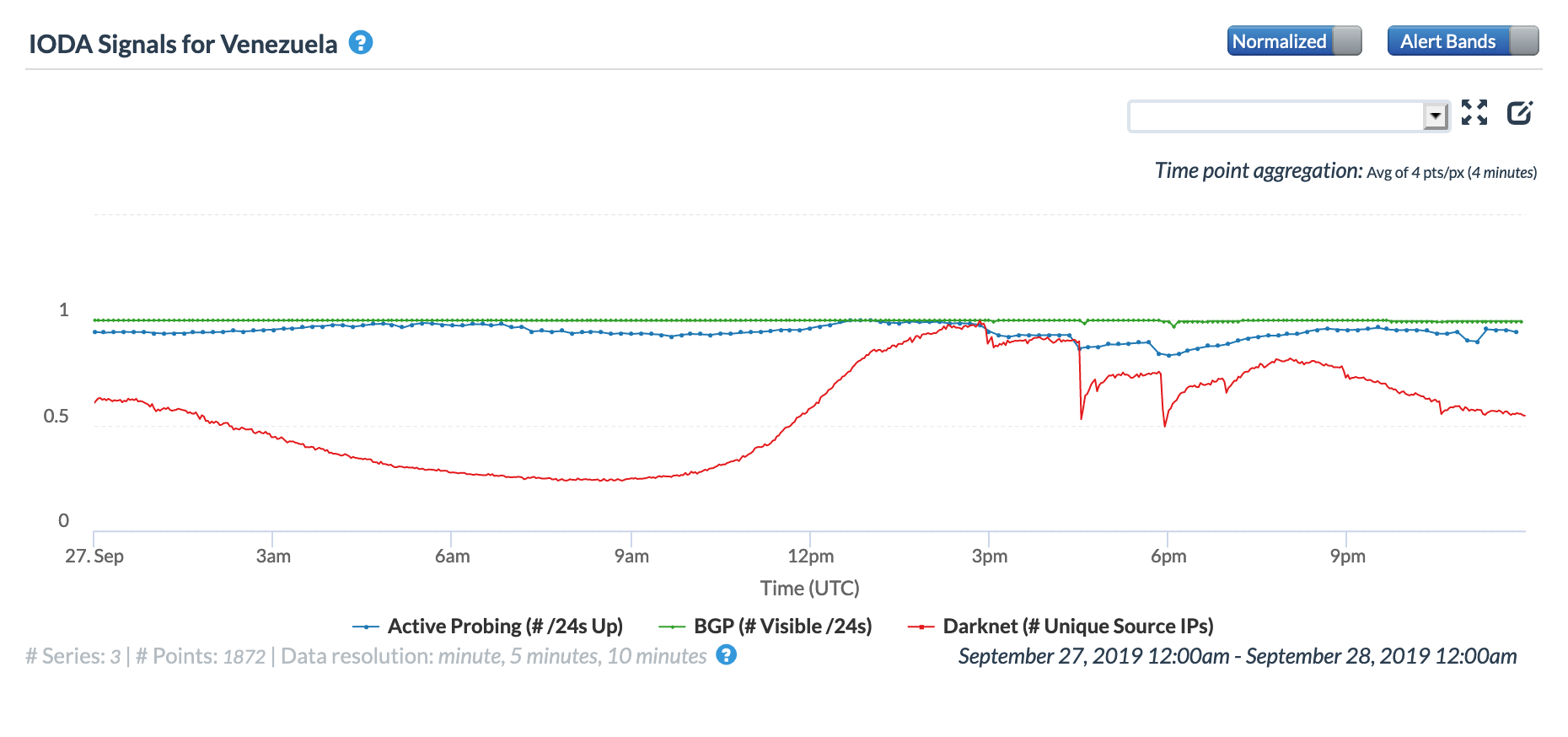
CAIDA IODA graph for Venezuela, September 27
National Exams
After seeing several Internet disruptions during the last week of August intended to prevent cheating on national exams, two more disruptions occurred in Iraq during the first few days of September. As the figures below show, partial disruptions were observed on September 1, 2, and 3, with diminishing severity across the three days.


Hurricanes
Several significant Atlantic Ocean hurricanes impacted Internet connectivity during September, starting with Hurricane Dorian. On September 1 & 2, Dorian made multiple landfalls in the Bahamas, causing significant damage. As the Oracle Internet Intelligence and CAIDA IODA figures below show, Internet connectivity in the Bahamas began to degrade shortly after midnight (GMT) on September 2, and then degraded significantly around 0730 GMT. The impact can also be observed at a city and network level, as seen in the additional CAIDA IODA figures below. However, in the main city of Freeport, the Internet disruption started earlier, with a significant drop in the Active Probing metric observed around 0200 GMT. While a slight decline was observed in the Active Probing metric for AS15146 (Cable Bahamas) around 0200 GMT, a more significant decline occurred around 0730 GMT. As the Google Transparency Report graph for the Bahamas below shows, connectivity took several weeks to return to “normal” levels.

Oracle Internet Intelligence Traffic Statistics graph for the Bahamas, September 2 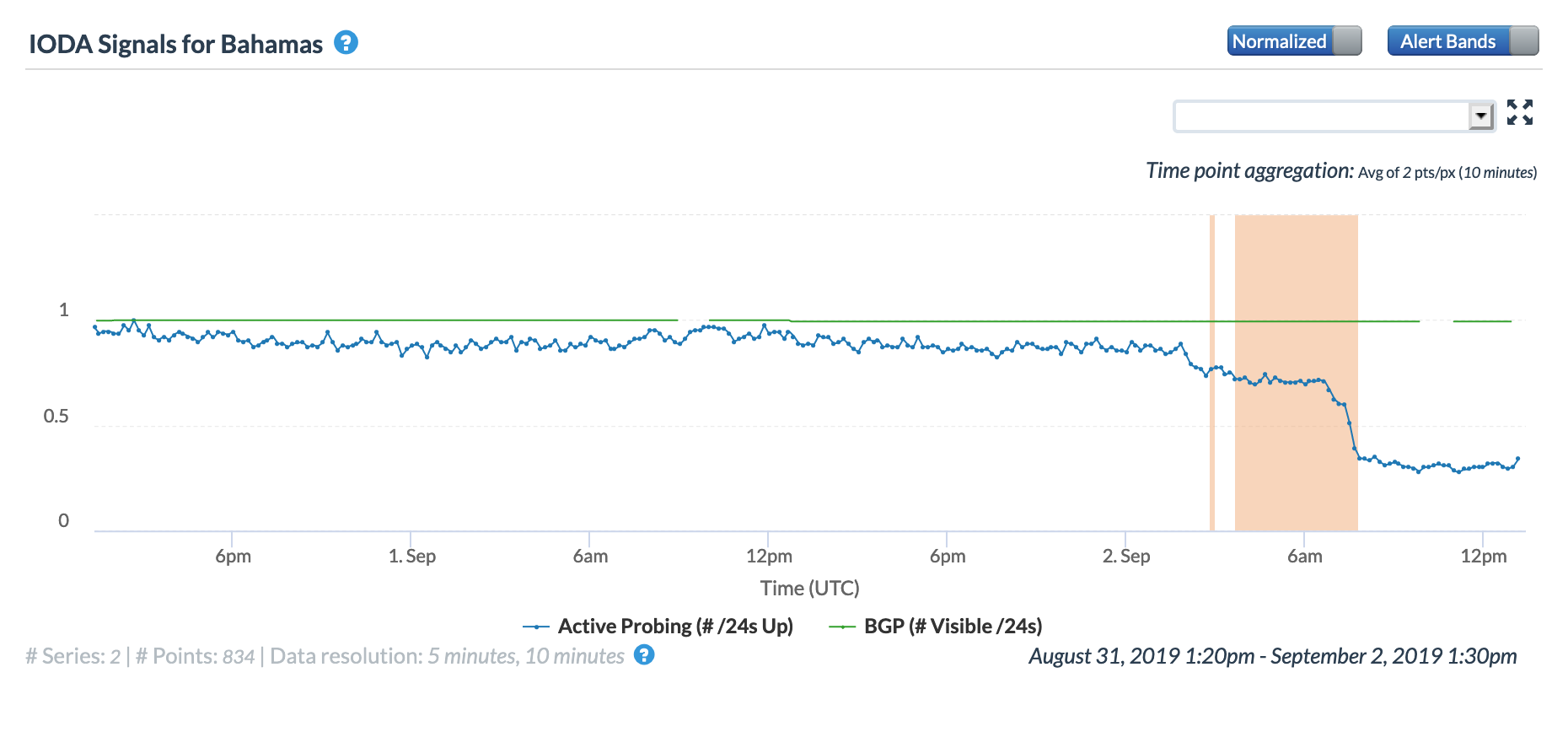
CAIDA IODA graph for the Bahamas, September 2
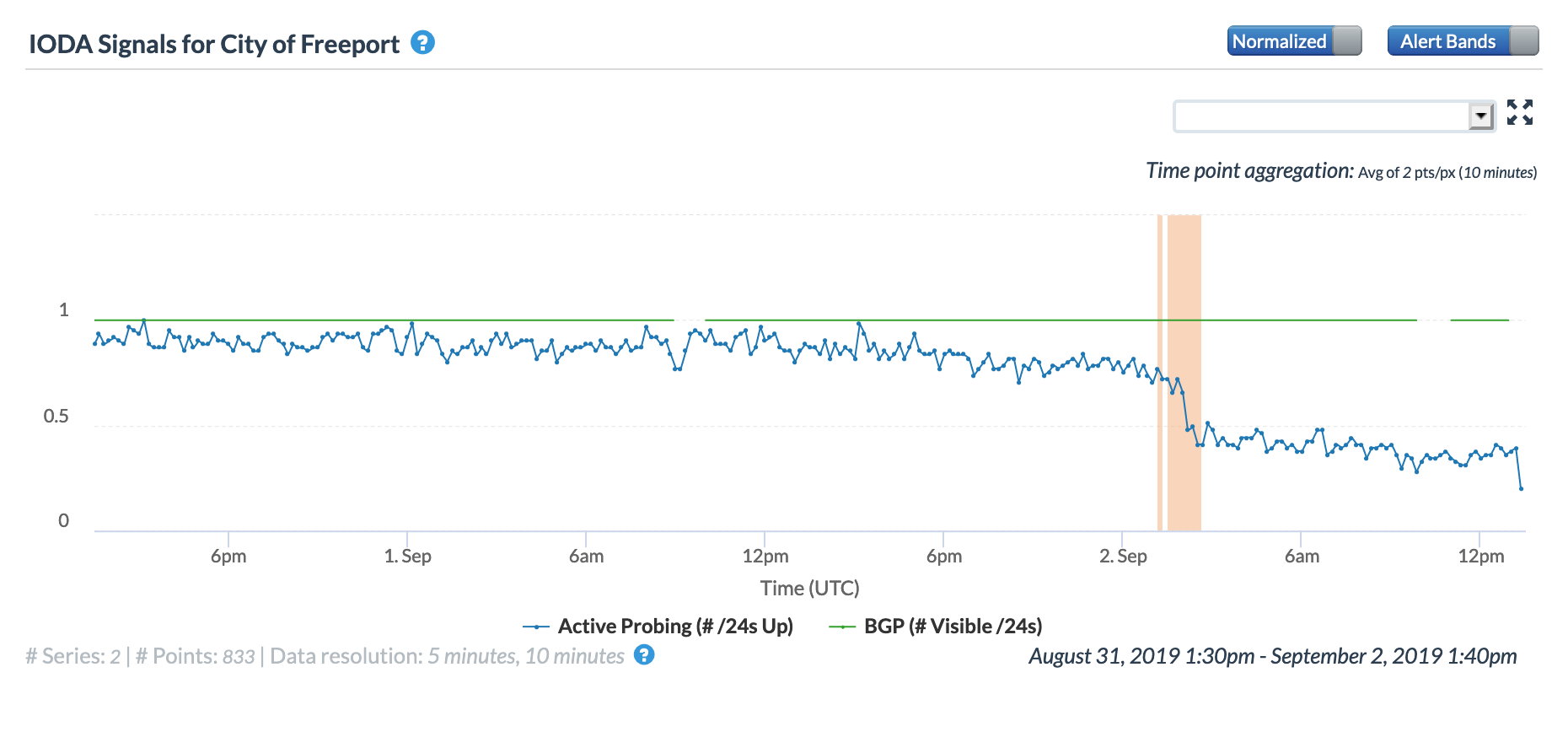
CAIDA IODA graph for Freeport, Bahamas, September 2 
CAIDA IODA graph for AS15146 (Cable Bahamas), September 2

A week later, after moving up the eastern seaboard of the United States, Hurricane Dorian landed in the Canadian province of Nova Scotia. There, the strong winds impacted Internet connectivity for subscribers of local network provider Eastlink in cities including Halifax, Dartmouth, and Truro, according to Fing Internet Alerts. The figure below from Fing shows that the disruption began around 1320 GMT, which corresponds to the time that the Active Probing and Darknet metrics began to decline in the CAIDA IODA figure below.

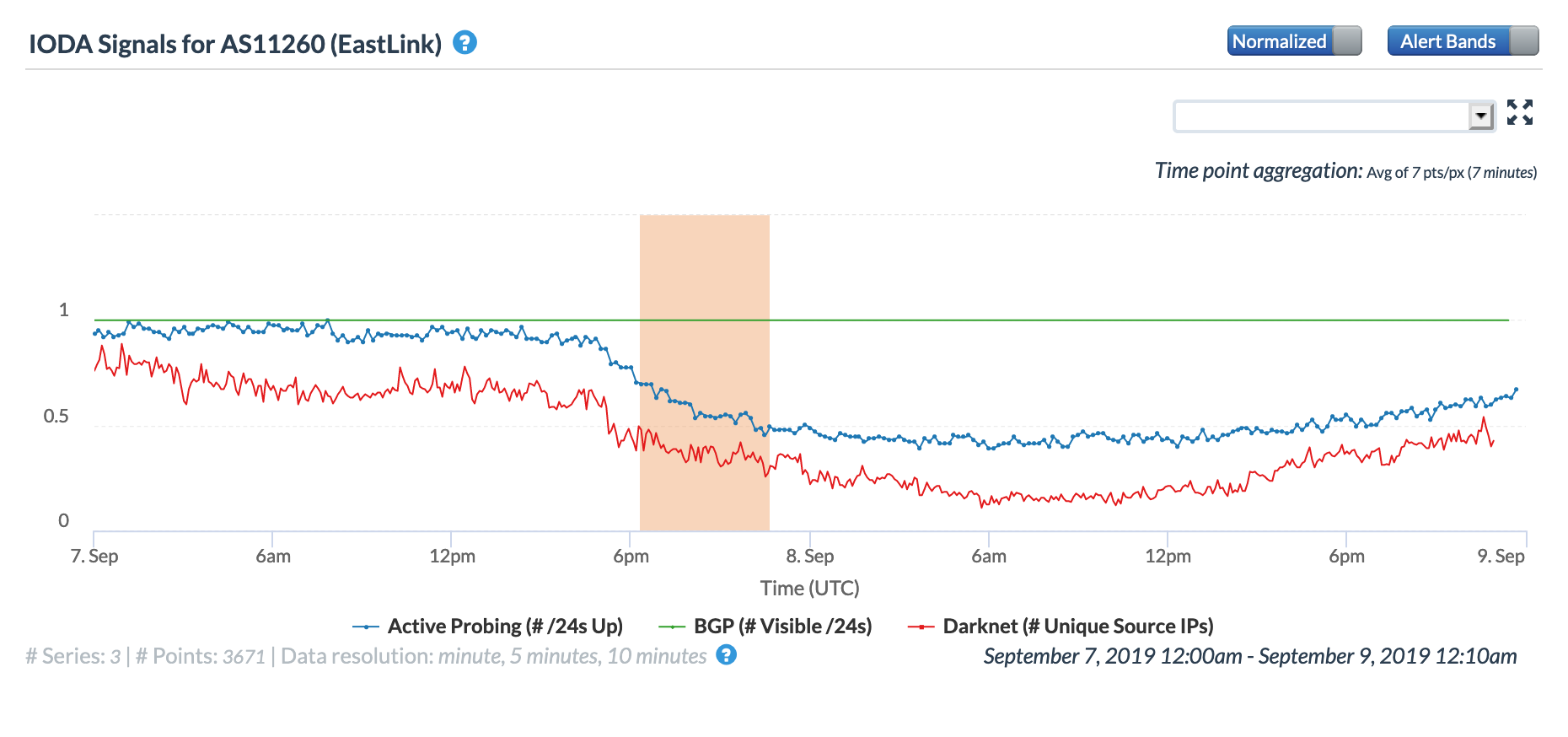
On September 19, Hurricane Humberto battered Bermuda, reportedly knocking out power for 80% of the island’s electricity customers. This widespread impact is best reflected in the lower peak in the DNS Query Rate metric seen in the Oracle figure below, the significant drop in the Darknet metric in the CAIDA IODA figure, and the visibly lower peak and deeper trough in the Google figure. Oracle’s Traceroute Completion Ratio metric and IODA’s Active Probing metric also saw declines, as would be expected, but the drops were less pronounced. This may be because a large portion of the targets selected for these active measurements are infrastructure components kept online with backup generators or other alternative power sources.

Oracle Internet Intelligence Country Statistics graph for Bermuda, September 19 
CAIDA IODA graph for Bermuda, September 19 
Google Transparency Report graph for Bermuda, September 19
Network Issues
On the morning of September 1 (GMT), country-level disruptions are visible in the Oracle Internet Intelligence Country Statistics graph for Haiti, shown in the figure below. Three separate disruptions occurred – the first lasted approximately four hours, starting at 0300 GMT, followed by two separate hour-long disruptions, starting at approximately 0740 GMT and 0900 GMT.

The observed disruption was apparently due to a fiber cut experienced by local provider Digicel Haiti, as it explained in the Tweet below. (English translation, via Google Translate: “We want to apologize to all customers who encountered a difficulty yesterday or morning while using the network! Unfortunately one of our underwater fiber optic cables was cut off! Our technicians work tirelessly to repair it quickly, now all our services are working.”) The Oracle Internet Intelligence Traffic Shifts figure shown below illustrates the impact of the fiber cut in Digicel Haiti – a near complete failure of traceroutes through upstream providers to reach the network, with a significant spike in latency for the few that did get through.

On September 16, Internet users in St. Thomas on the U.S. Virgin Islands experienced an Internet disruption due to a fiber cut. In a post to its Facebook page, local service provider Viya noted that a public works contractor had severed a fiber optic cable, impacting connectivity. The CAIDA IODA figure below shows a visible drop in the Active Probing metric for St. Thomas starting just after 1200 GMT. (However, the apparent corresponding increase in the Darknet metric is unusual – it is not clear why it occurred.)

Singaporean provider StarHub experienced a multi-hour disruption on September 17 that impacted both fixed and mobile Internet users. To their credit, StarHub was quick to respond, and ultimately posted an update on its Web site, providing more information on the incident:
“An internet routing issue has been identified as the root cause of the incident, and StarHub has ruled out a cyber attack. StarHub takes this incident seriously and is implementing measures to prevent a recurrence.”
The CAIDA IODA figures below, ordered by the number of IPv4 prefixes originated, show the impact of the routing issue on five StarHub autonomous systems. The most significant impact appeared to be with AS55430, associated with StarHub’s Next Generation Nationwide Broadband Network. Connectivity for AS10091, associated with StarHub’s discontinued cable Internet service, also saw a major impact.
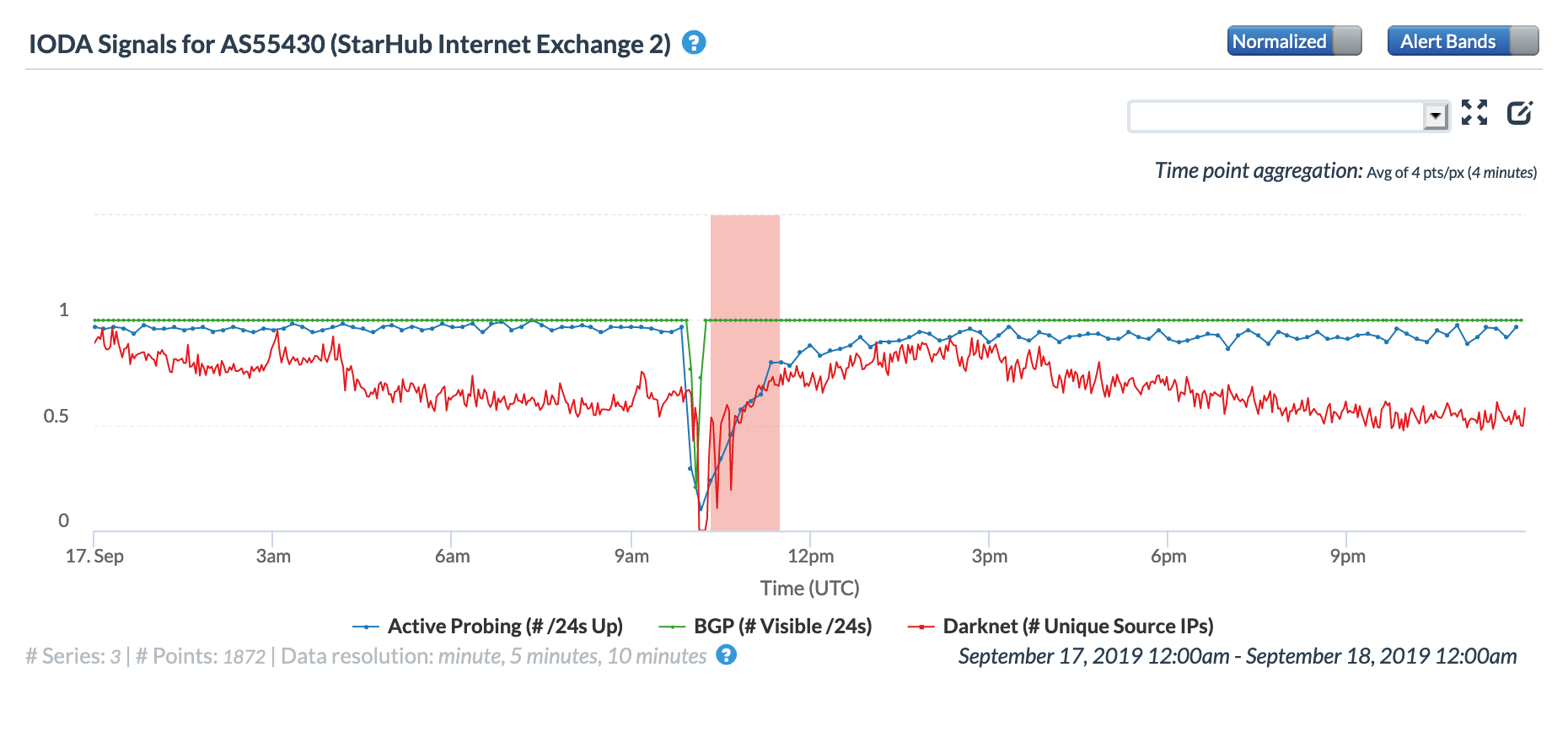
CAIDA IODA graph for AS55430 (StarHub-NGNBN) 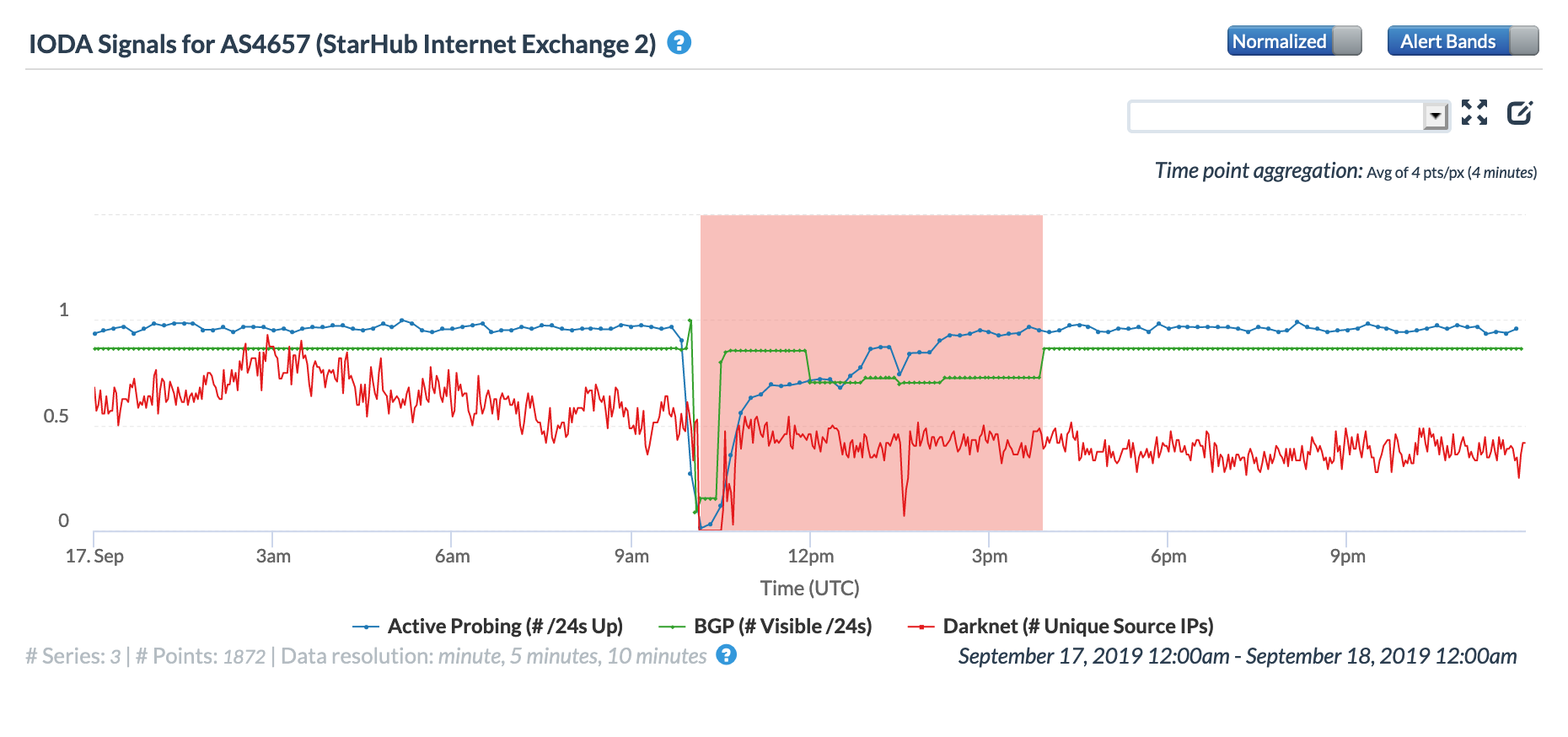
CAIDA IODA graph for AS4657 (StarHub-INTERNET) 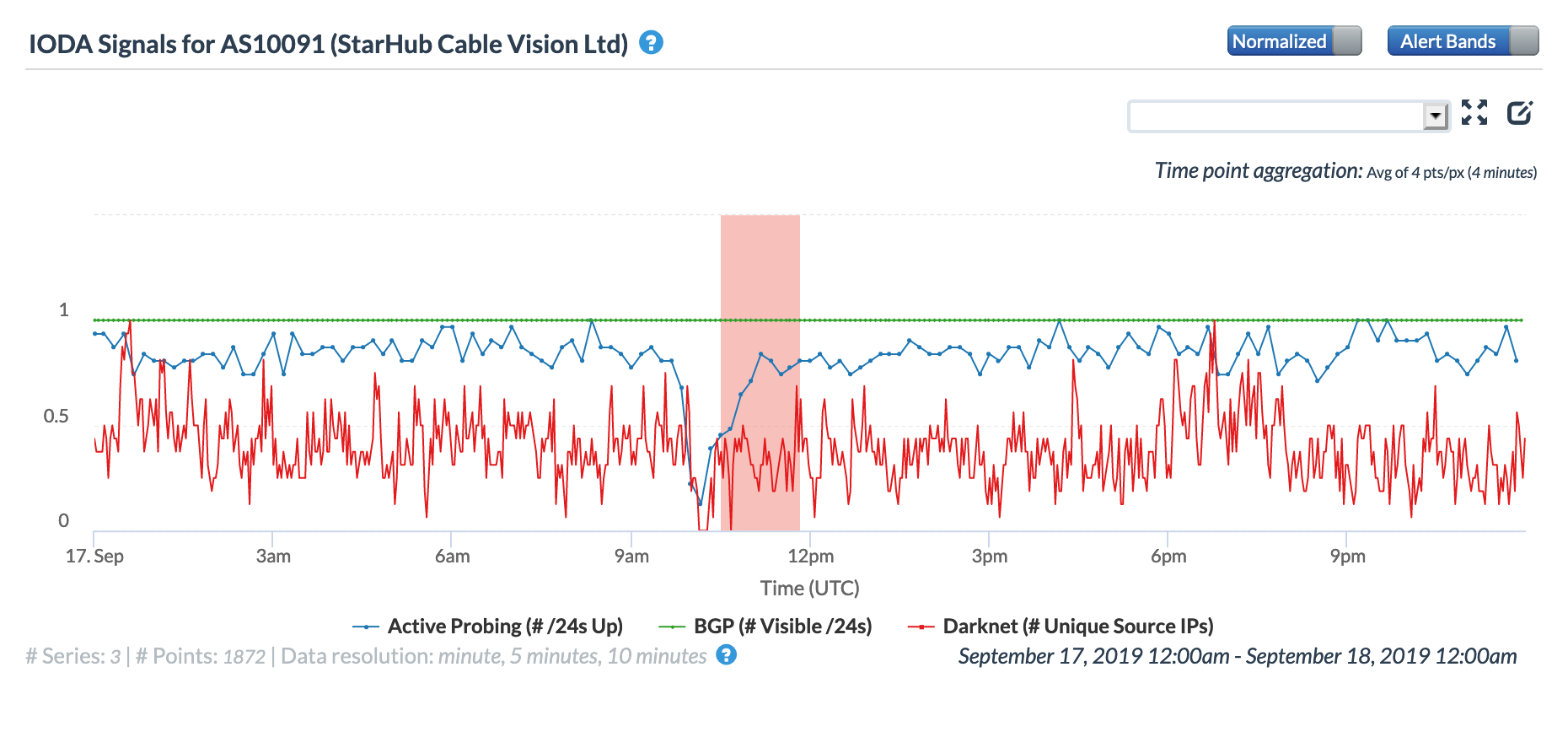
CAIDA IODA graph for AS10091 (StarHub-CABLE) 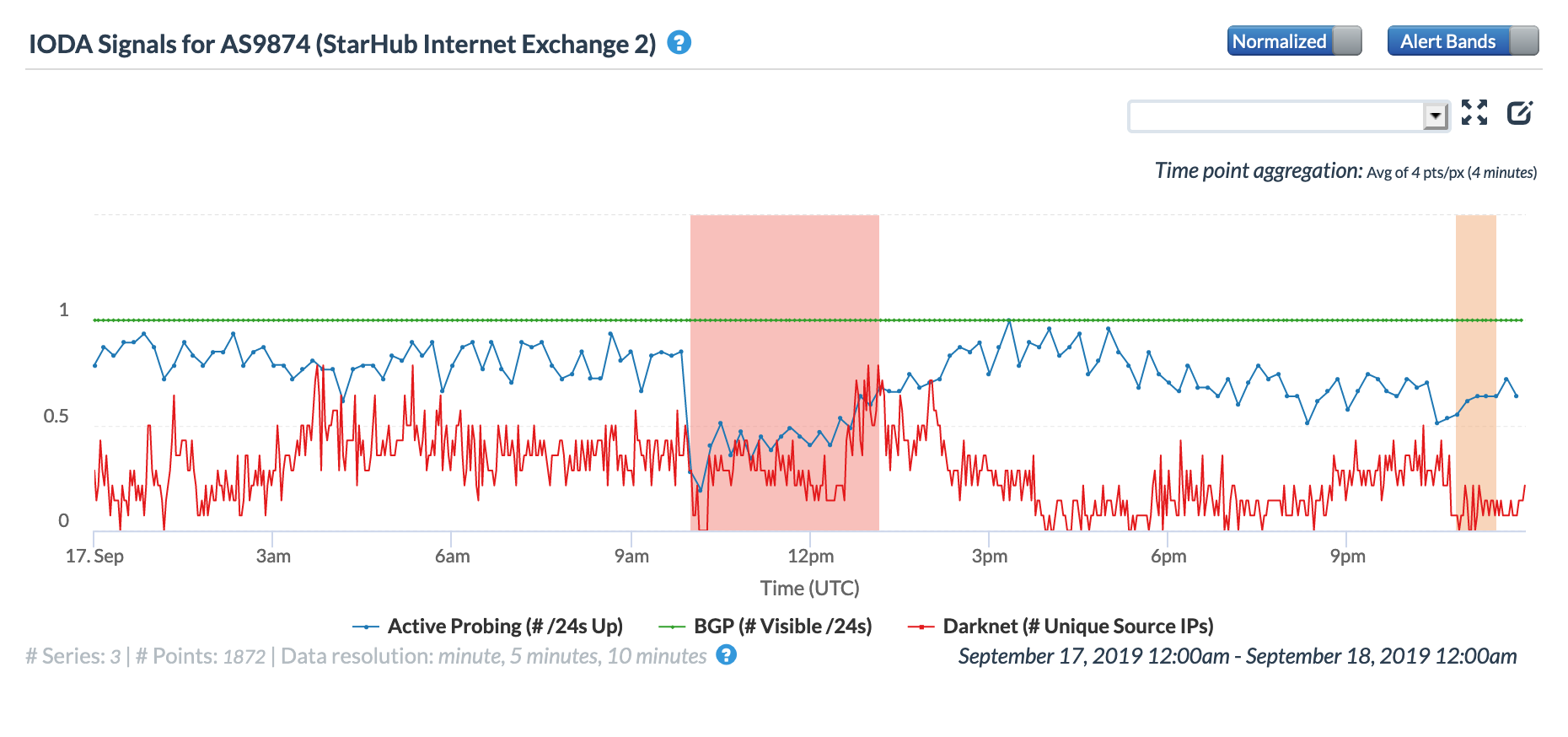
CAIDA IODA graph for AS9874 (StarHub-MOBILE) 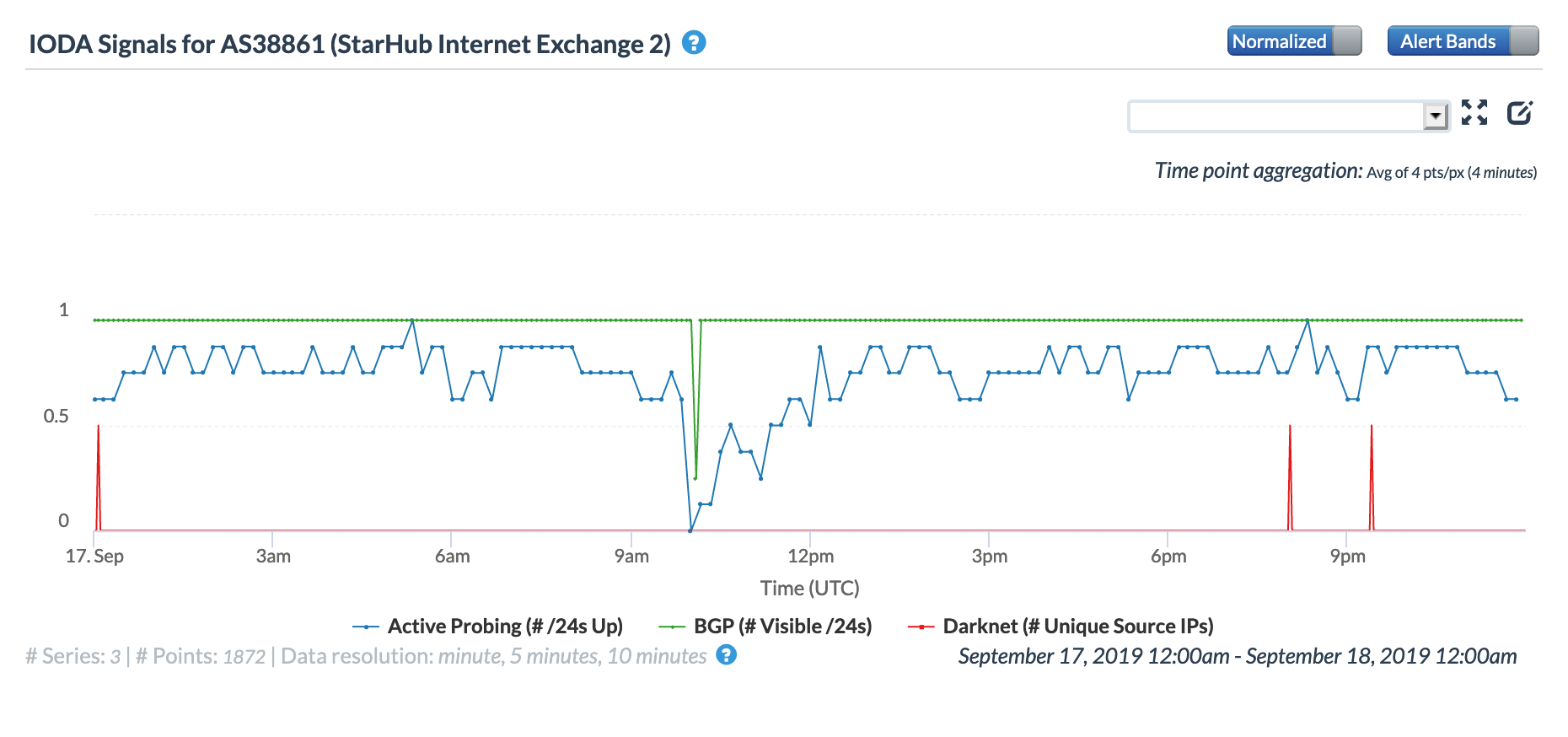
CAIDA IODA graph for AS38861 (StarHub-INTERNET2)
Fing Internet Alert Tweeted about an Internet disruption affecting New Zealand provider Trustpower on September 29. The CAIDA IODA figure below for the network shows that the disruption was brief but significant, with clear declines occurring in both the Active Probing and Darknet metrics. Trustpower posted several apology Tweets like the one shown below, explaining that it had experienced a brief outage in its fiber services.

Somewhat unsurprisingly, chronically problematic submarine cable SEA-ME-WE-3 suffered another failure on September 20, according to a published report. While the cable connects Australia to Asia and Europe, the Perth-to-Singapore segment suffered issues this time, with the problem apparently occurring between repeaters 345 and 346. The segment has experienced documented problems in the past, but traffic has been able to fail over to the Australia-Singapore Cable (ASC) since September 2018.
DDoS Attack
Cool Ideas, one of South Africa’s largest Internet Service Providers, was targeted by a DDoS attack on September 21 & 22. The attack reportedly used DNS Amplification to overwhelm Cool Ideas’ connections with traffic. Cool Ideas posted status updates to its Web site while the attack was underway, alerting users to potential connectivity loss and degraded performance.

Based on the CAIDA IODA figure below, it appears that the attack may have come in several waves, with multiple declines seen in the Active Probing metric during the two day period. The Oracle Internet Intelligence figure below shows how the attack impacted latency for traceroutes to targets within the Cool Ideas network, with increases observed during the waves of the attack. The figure also shows how Cool Ideas’ upstream connectivity shifted as a result of the attack, with traffic moving from AS6939 (Hurricane Electric) to AS3741 (Internet Solutions). A Cool Ideas representative noted that they had integrated attack mitigation mechanisms with their Internet Solutions connectivity, which is likely why they shifted to having more traffic flow through that upstream provider (so it could be scrubbed).


This upstream connectivity shift is illustrated in more detail in the figure below from IIJ Lab’s Internet Health Report. The graph shows the AS dependencies for Cool Ideas’ ASN during the duration of the attack. Before the attack began, Cool Idea had a significant dependency on AS6939, but this dropped over the course of the attack, with other network providers, including AS3741 and AS174 (Cogent), seeing increased AS hegemony.

Correction
In the August 2019 Internet Disruption Report, we classified the Internet shutdown in the Jammu and Kashmir region of India as a sub-national shutdown that was not visible on publicly available monitoring tools. A CAIDA IODA team member alerted us that the disruption was in fact visible in their tool. The figure below shows a decline in the Active Probing metric on August 4, when the shutdown began, along with a corresponding drop in the Darknet metric. We thank the CAIDA team for the update, and apologize for the error.

Conclusion
September also saw a number of Internet disruptions where the cause was unclear – research did not uncover any associated local event or information published by a service provider on their Web site or social media presence. That latter point continues to be a source of frustration, with multiple service providers again failing to respond to requests made via social media for additional information about Internet disruptions observed to have impacted their networks.
Having said that, the underlying reasons for government-directed Internet shutdowns ultimately become well-known, and in early September, the New York Times published an article that examined both the human and economic costs of such shutdowns, looking at several that have recently occurred in African nations.
“The shutdowns do more than stunt the democratic process. They can batter whole economies and individual businesses, as well as drastically disrupt the daily life of ordinary citizens, turning the search for mobile service into a game of cat and mouse with the police and driving people across borders just to send emails for work.”
And although this has been in planning for quite some time, Russia will apparently soon begin testing its ability to effectively isolate the Russian Internet (RuNet) from the global Internet. Driven by legislation signed earlier this year, according to a published report, the legislation mandates that Russian Internet service providers have the technical means to disconnect from the rest of the world and reroute Internet traffic through exchange points managed by Roskomnadzor, Russia’s telecommunications and media regulator. If they are successful in implementing such a system, tests and/or activation will likely result in Internet disruptions being visible in popular monitoring tools not only for Russia, but also neighboring countries that route traffic through Russia.
]]>National Exams
After ending June with regional Internet disruptions reportedly intended to prevent student cheating on national Physics exams in Iraq, there were six additional nationwide disruptions observed over the first half of July, as seen in the figures below. Multi-hour disruptions took place on July 1, 4, 7, 10, 13, and 15. Published reports indicate that the Internet was again disrupted at the request of the education ministry in an effort to prevent student cheating. Iraq has been implementing such tactics since 2015.
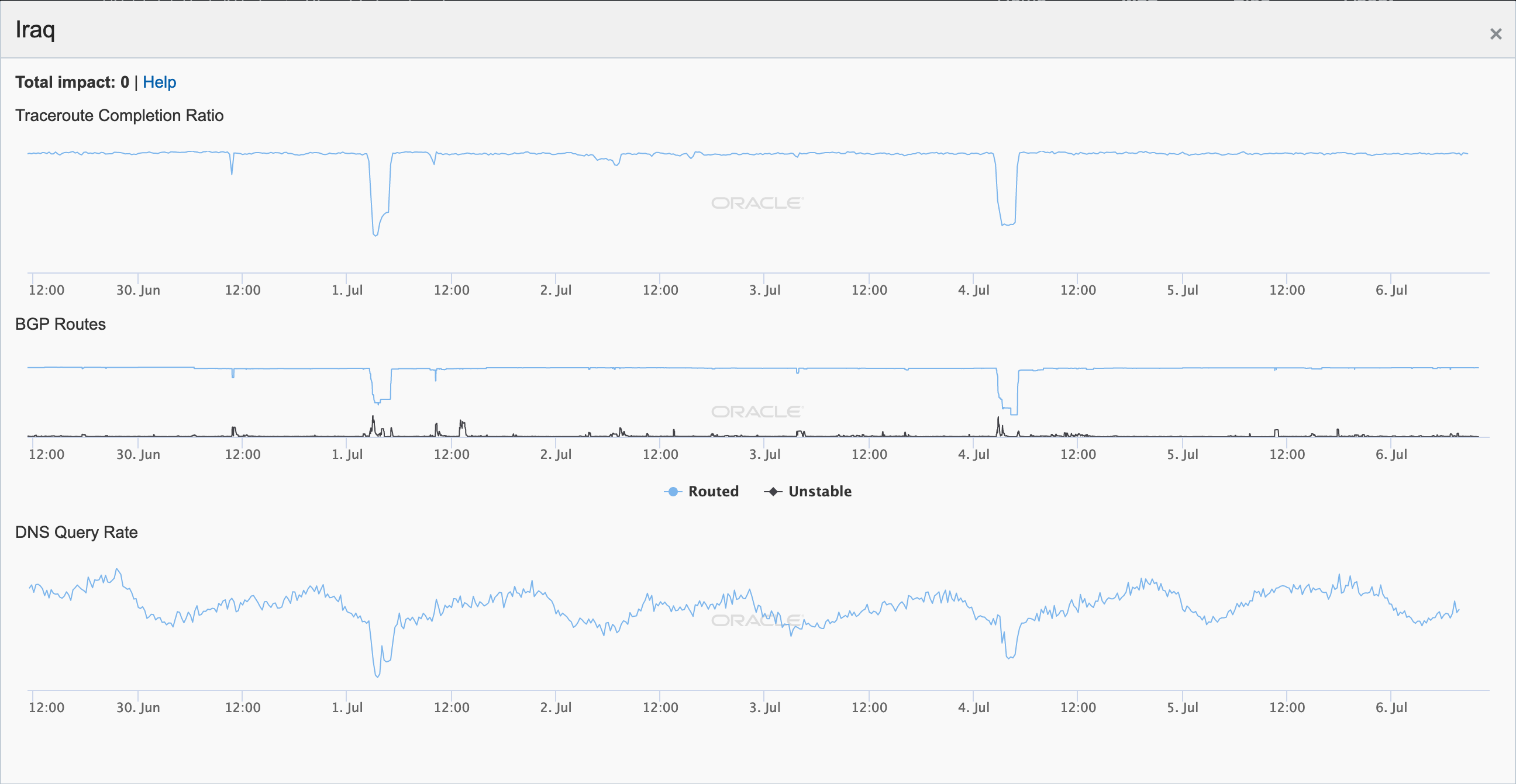
Oracle Internet Intelligence graph for Iraq, July 1-4 
Oracle Internet Intelligence graph for Iraq, July 4-7 
Oracle Internet Intelligence graph for Iraq, July 7-10 
Oracle Internet Intelligence graph for Iraq, July 13-15 
Google Transparency Report traffic graph for Iraq, July 1-16
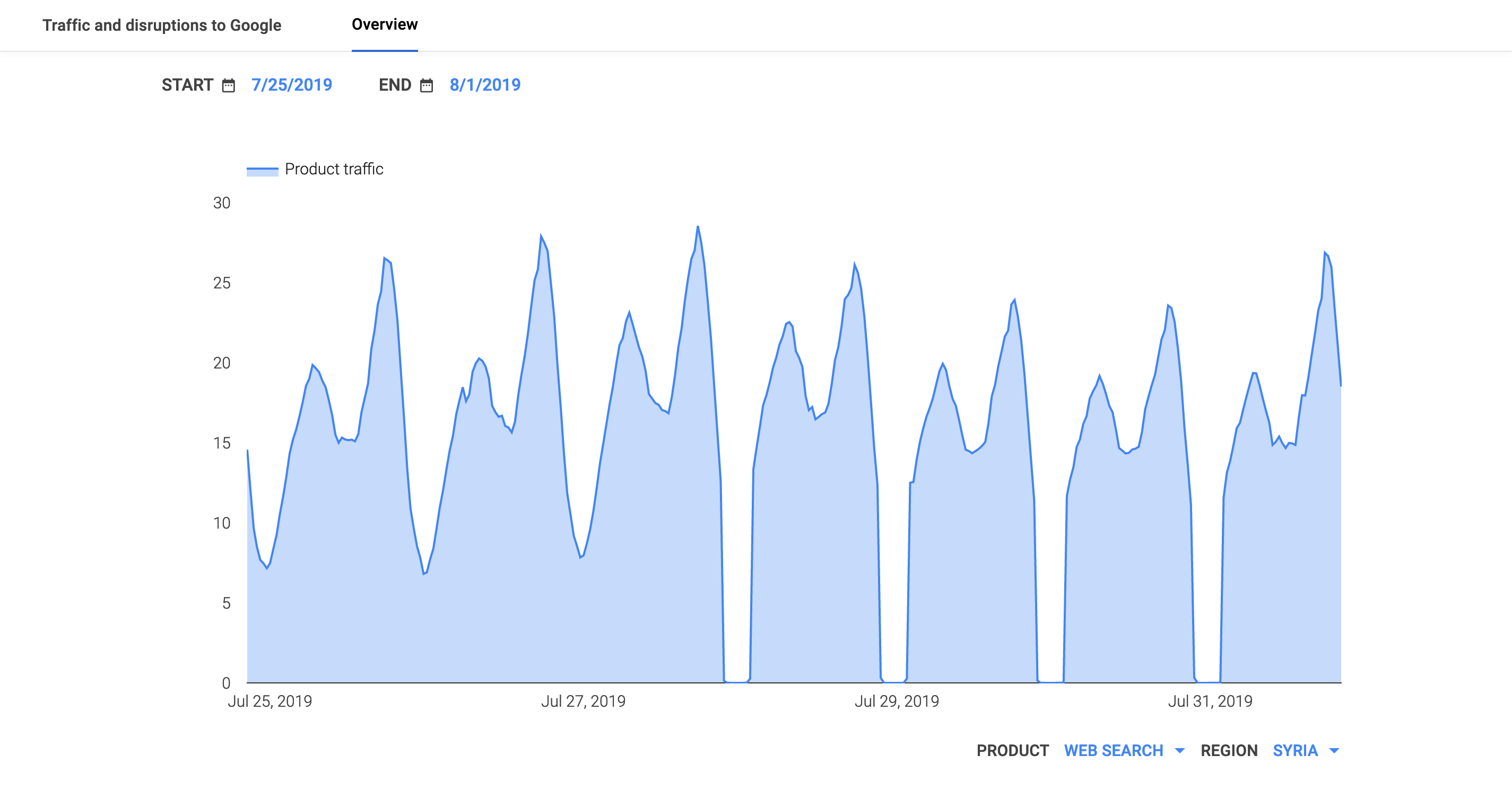
After five exam-related Internet disruptions were observed in Syria during the first three weeks of June, another four were observed across the last days of July, as seen in the figures below. The impact is shown at a country level, as well as for AS29256 (Syrian Telecom), the state-affiliated telecommunications provider. Although no specific documentation of these disruptions being related to national exams could be found online (either in published reports or on the Syrian education ministry Web site), their frequency and duration closely resembles similar verified disruptions seen in the past. As such, they are being categorized as exam-related.
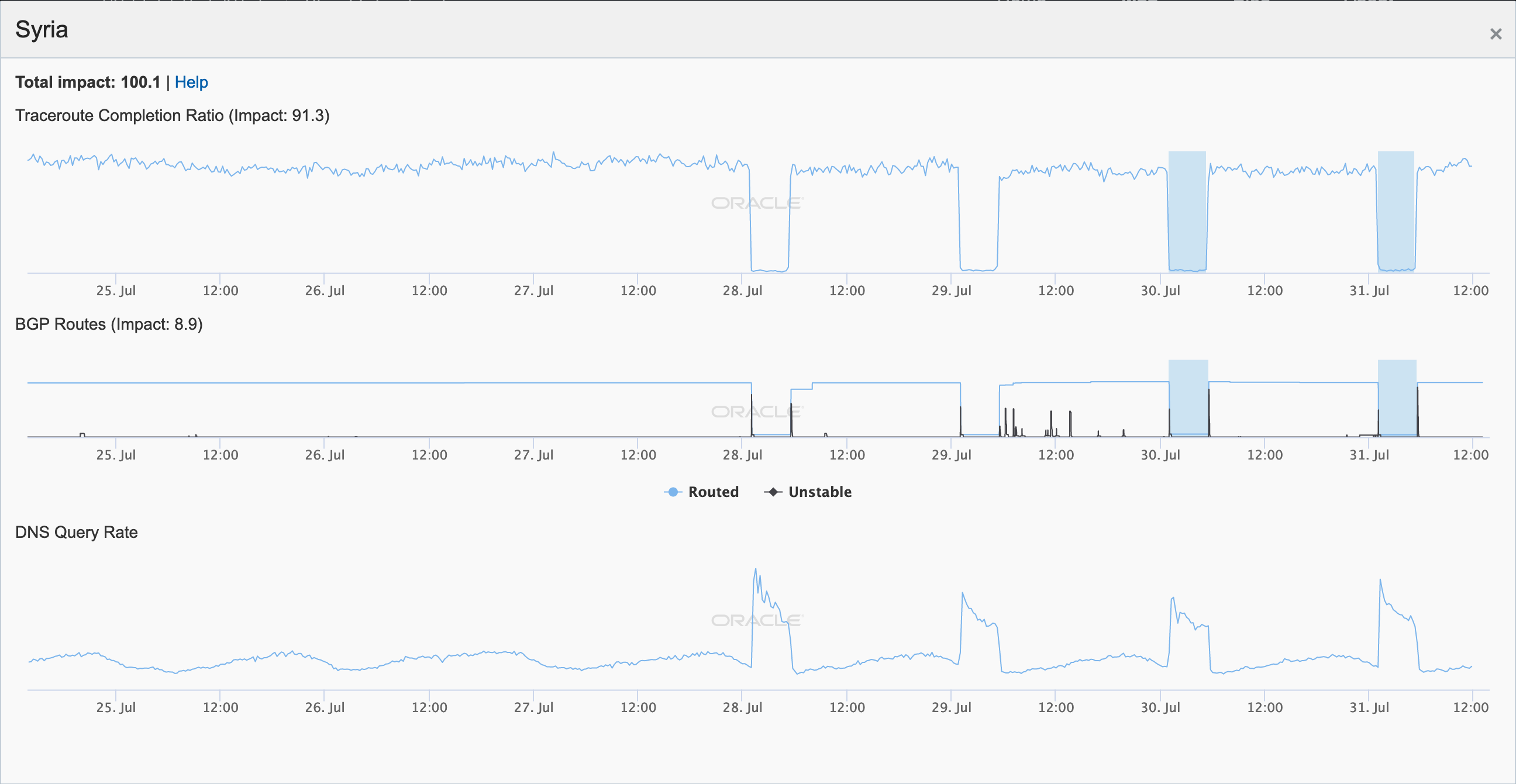
Oracle Internet Intelligence graph for Syria, July 25-31 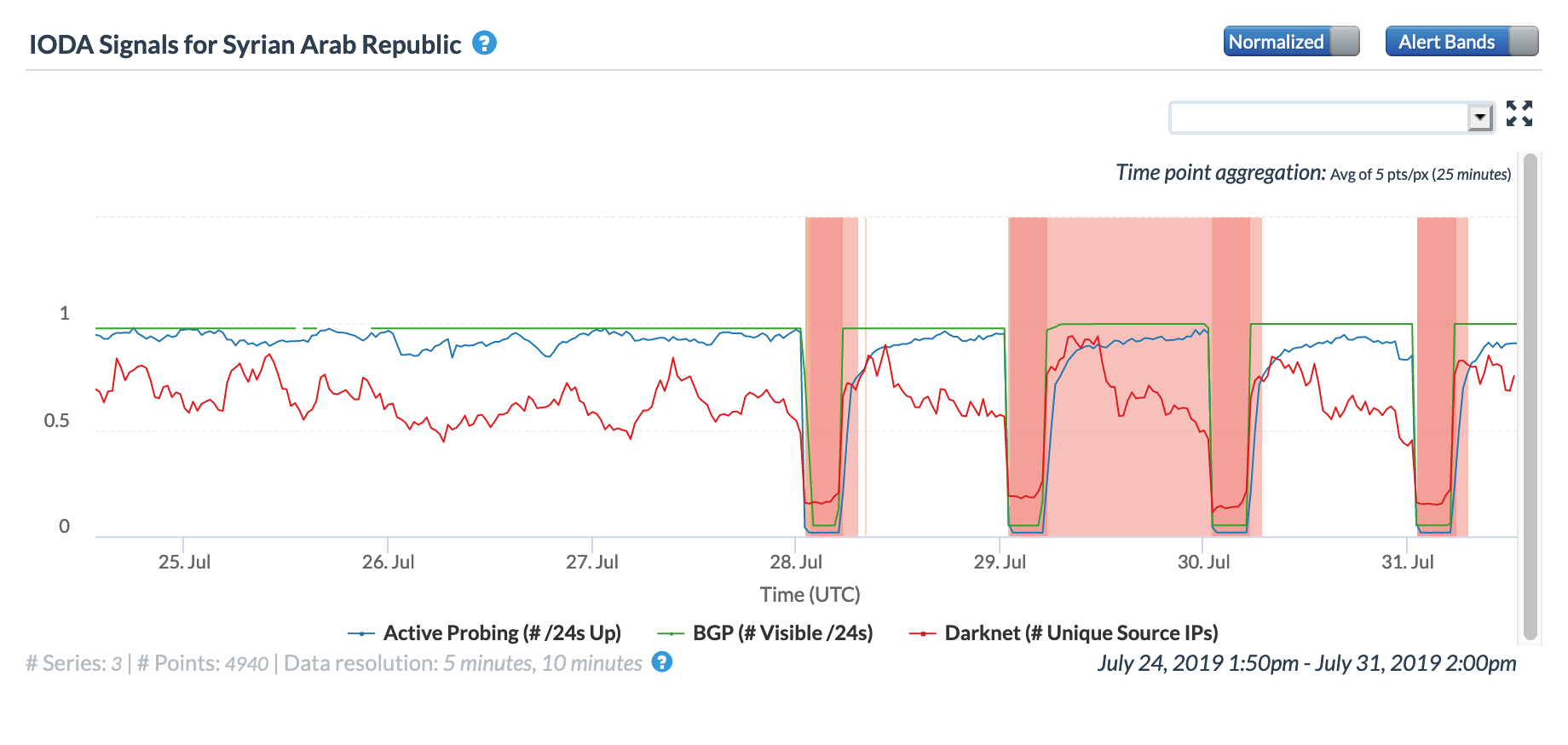
CAIDA IODA graph for Syria, July 25-31

Oracle Internet Intelligence graph for AS29256, July 25-31 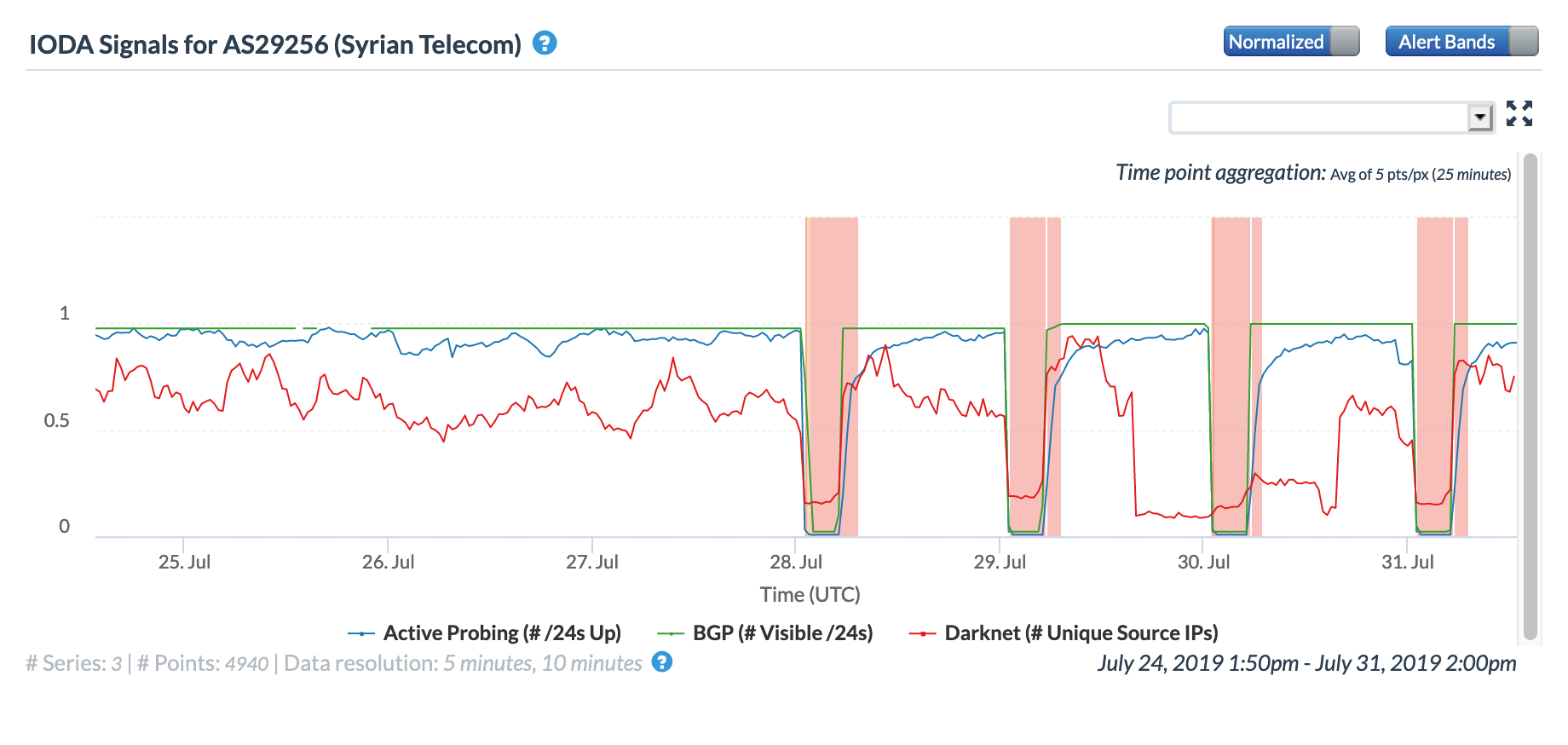
CAIDA IODA graph for AS29256, July 25-31
Power Outage
In its first major power outage since March, Venezuela suffered a massive blackout on July 22, plunging more than half of Venezuela’s 23 states into darkness. The figures below show that power failed around 20:00 GMT, ultimately disrupting Internet connectivity for more than a day. As illustrated in the Oracle Internet Intelligence and CAIDA IODA graphs, the active measurements (traceroute & ping) dropped immediately and took a significant amount of time to recover; the passive (user traffic) measurements (DNS, darknet, Google Web search) exhibited the same behavior. However, only minor churn is evident in Oracle’s and CAIDA’s BGP-based metrics, indicating that the routes to networks within the country remained available, even if endpoints on those networks were unreachable.
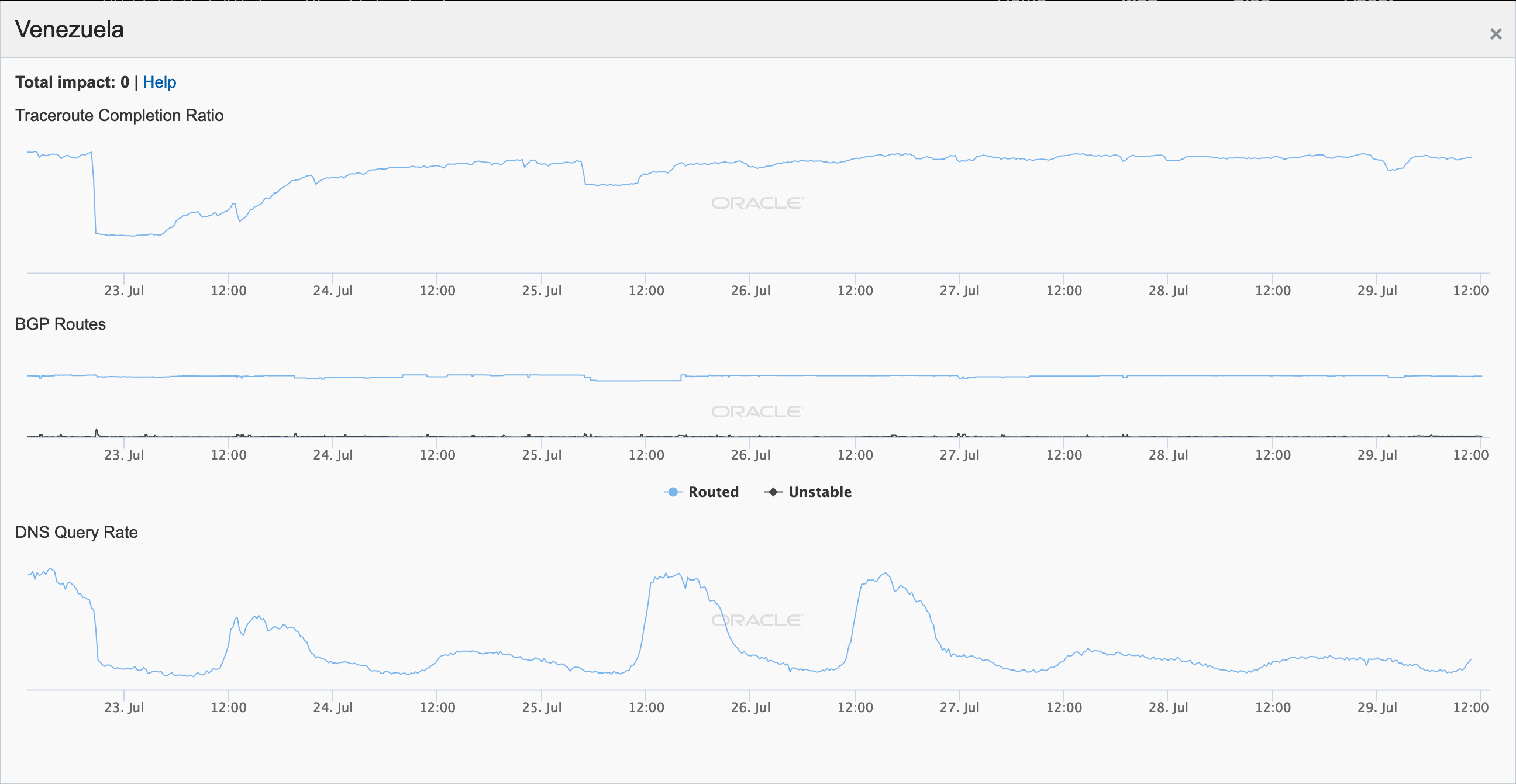
Oracle Internet Intelligence graph for Venezuela, July 22-29 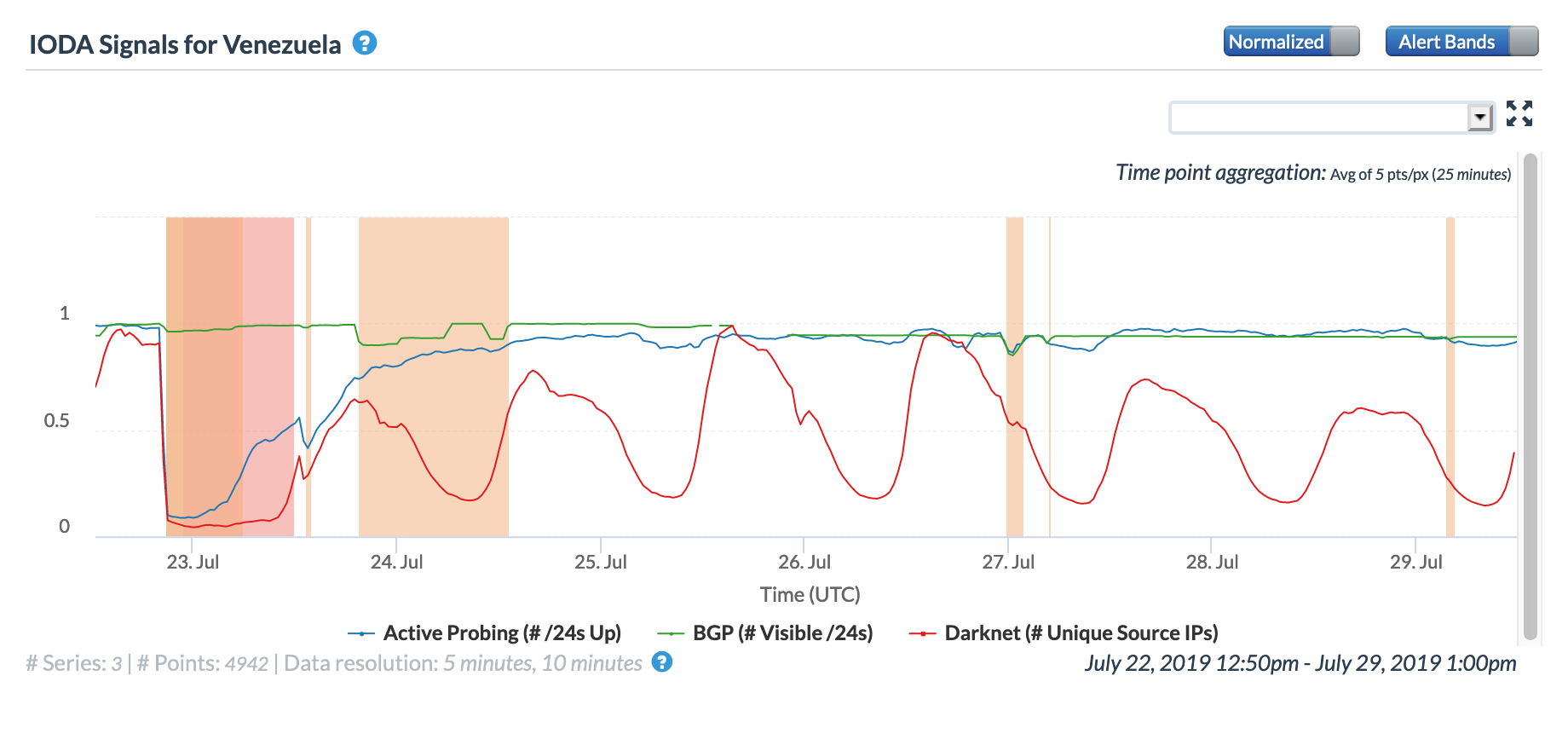
CAIDA IODA graph for Venezuela, July 22-29 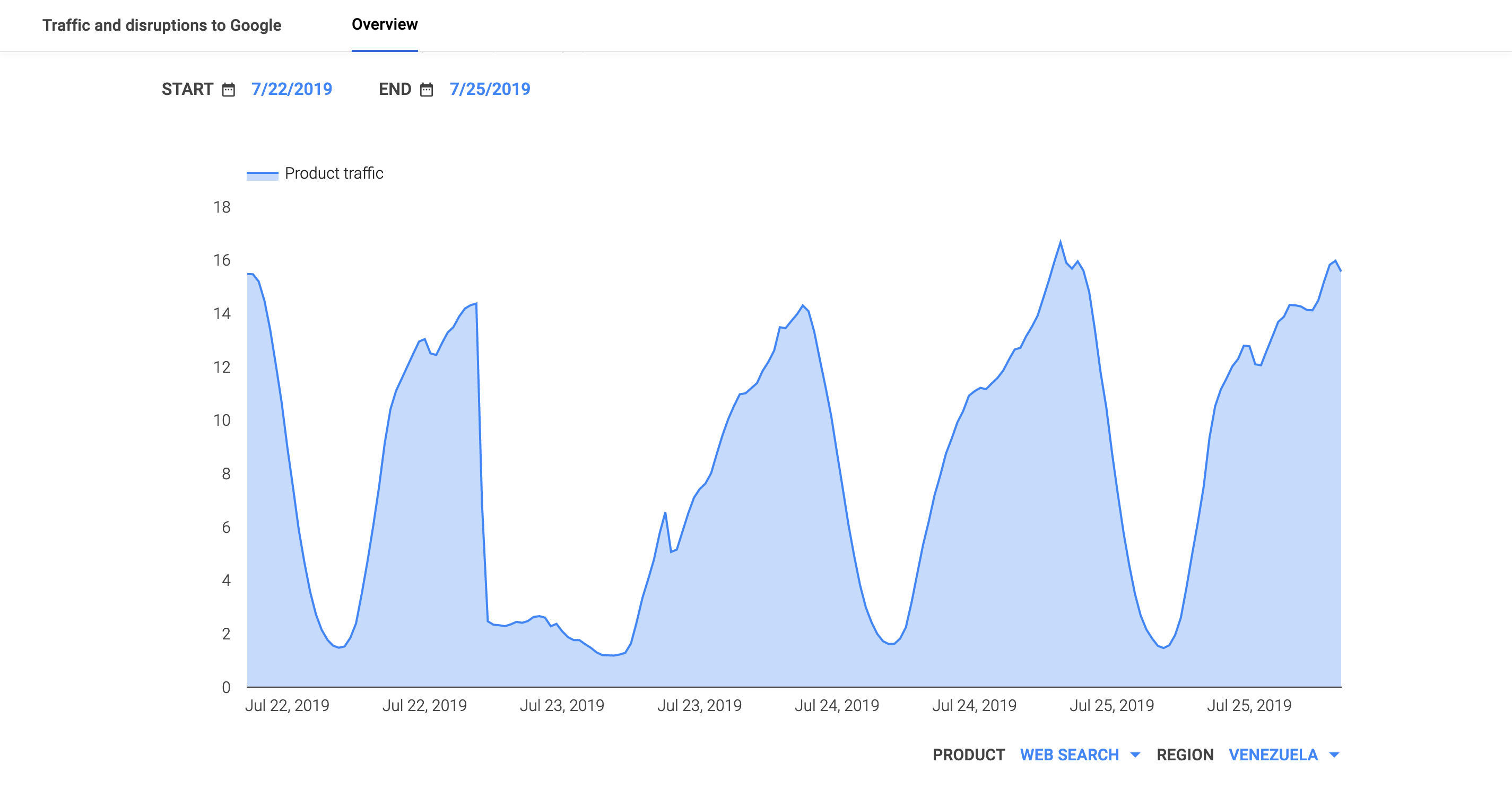
Google Transparency Report traffic graph for Venezuela, July 22-29
The @outagedetect Twitter account, associated with Internet connection and connected device monitoring company Fing, also observed the disruption within its monitoring of subscriber devices on CANTV, Venezuela’s state-run Internet service provider and posted the Tweet below:
Government Directed
Also on July 22, a fire broke out at the Kondengui Central Prison in Cameroon’s capital city of Yaounde after detainees held a protest in the overcrowded detention facility. A published report noted “The internet was shut down while a drone was flown over the prison.” This shutdown is likely the root cause of the Internet disruptions shown in the graphs below, for both Cameroon at a country level, as well as for AS30992 (MTN Cameroon), a major network provider within the country.
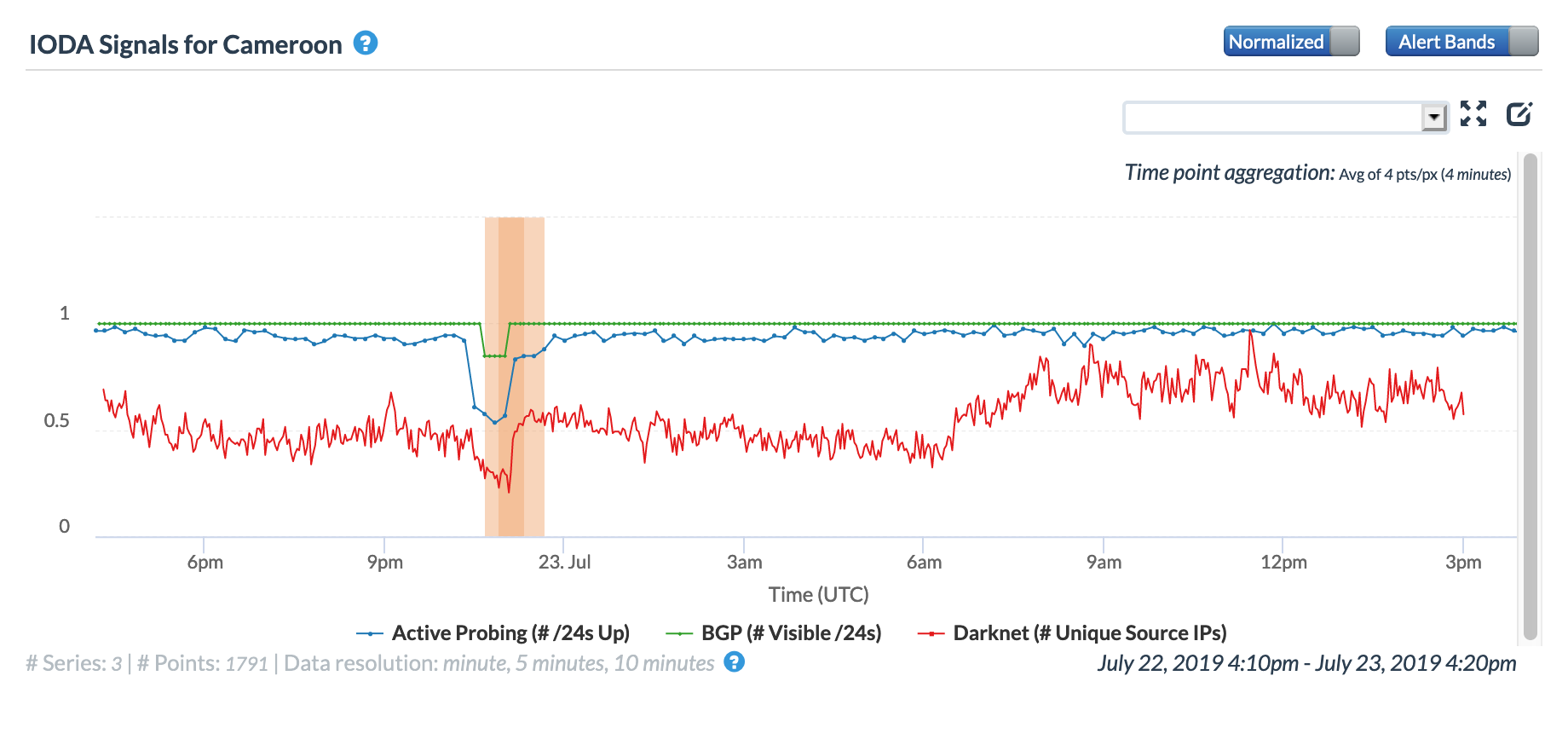
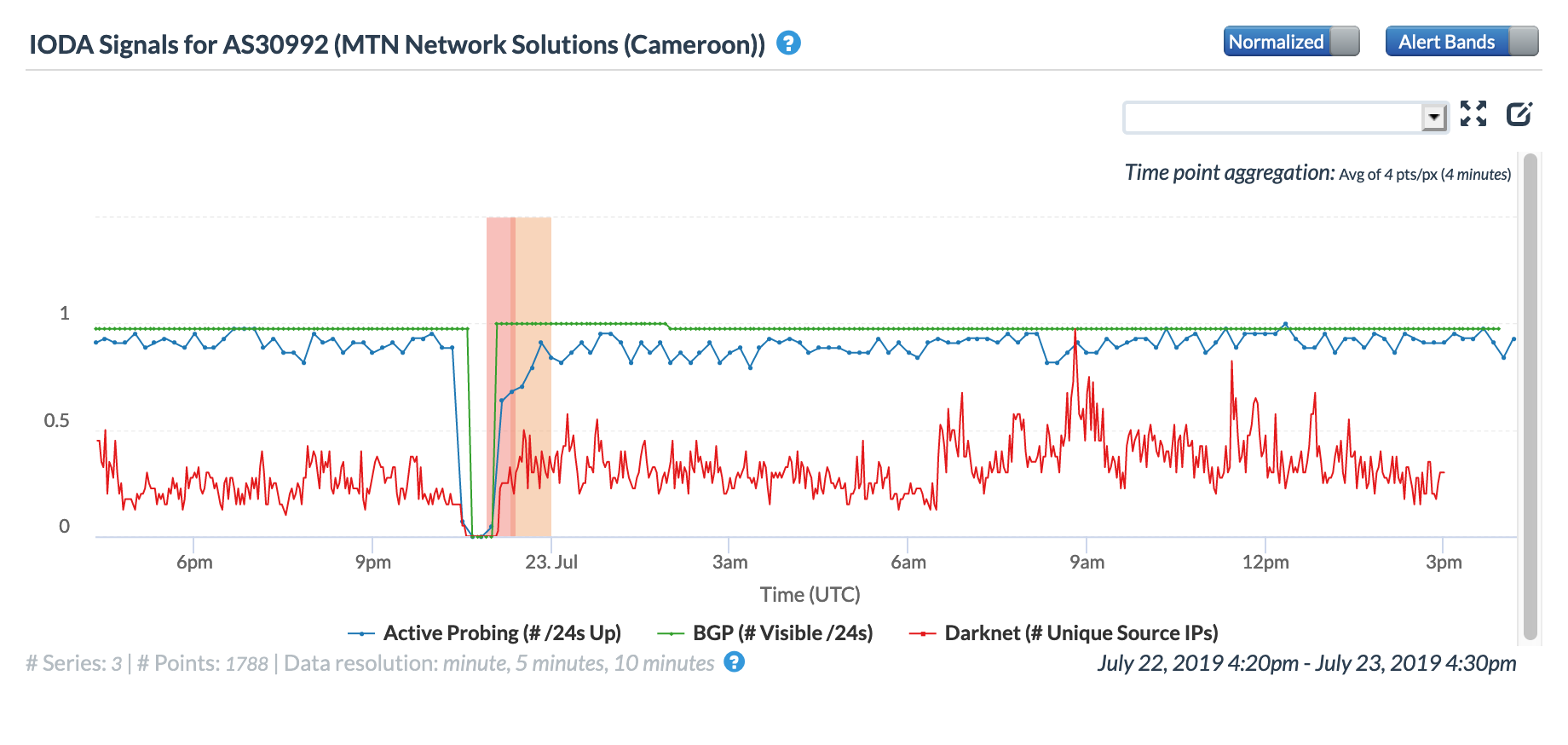
Severe Weather
While this blog generally looks at country-scale Internet disruptions, the network impact of severe weather events is much more localized, wreaking havoc and causing connectivity problems across a much smaller geographic area.
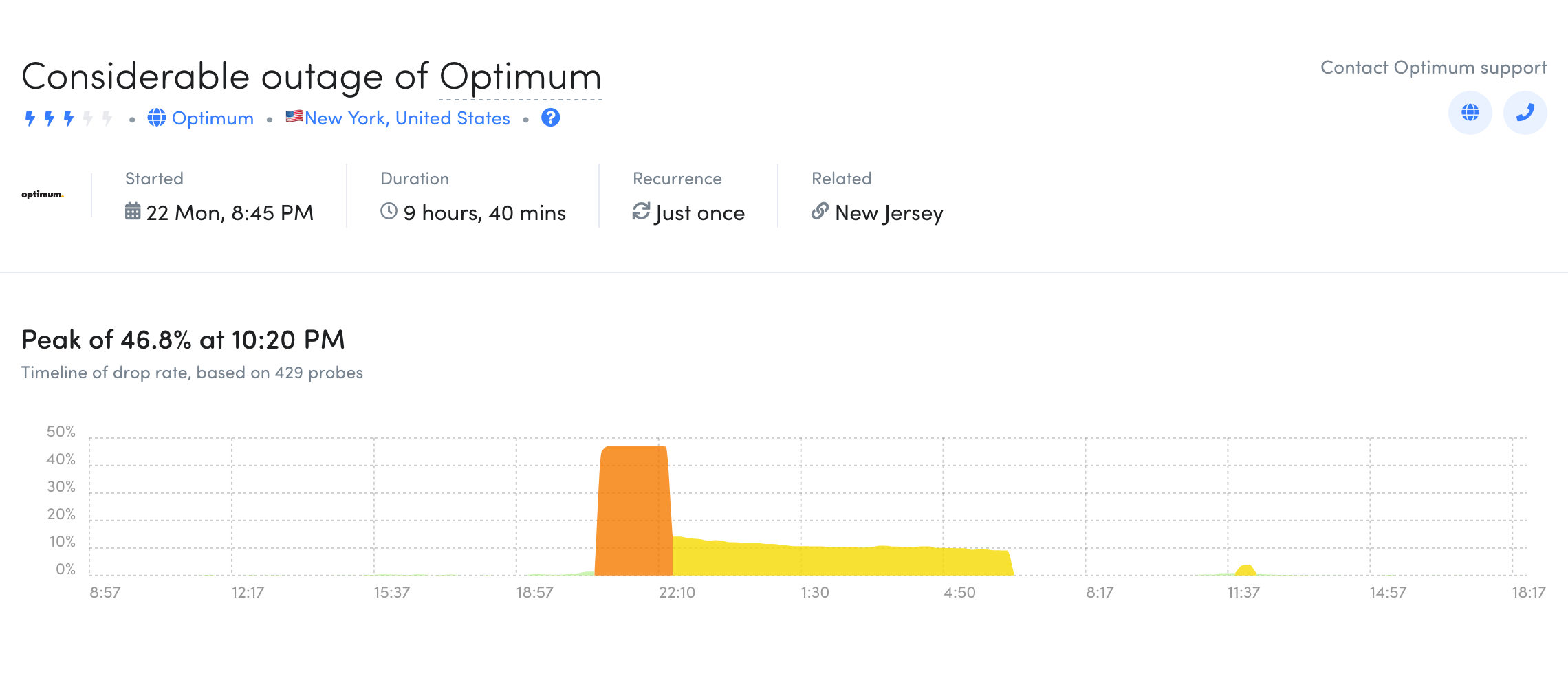
On July 23, Fing’s @outagedetect Twitter account highlighted a “considerable” outage impacting customers of network provider Optimum Online in New York & New Jersey.
Fing’s detail view showed that the disruption started at 20:45 (ET) on July 22, and lasted for nearly 10 hours. The disruption can also be seen in the CAIDA IODA graph below, with drops in the Active Probing and Darknet metrics seen for several hours, roughly aligned with the orange portion of the Fing graph. (Optimum Online is the high-speed Internet brand of Cablevision Systems.)
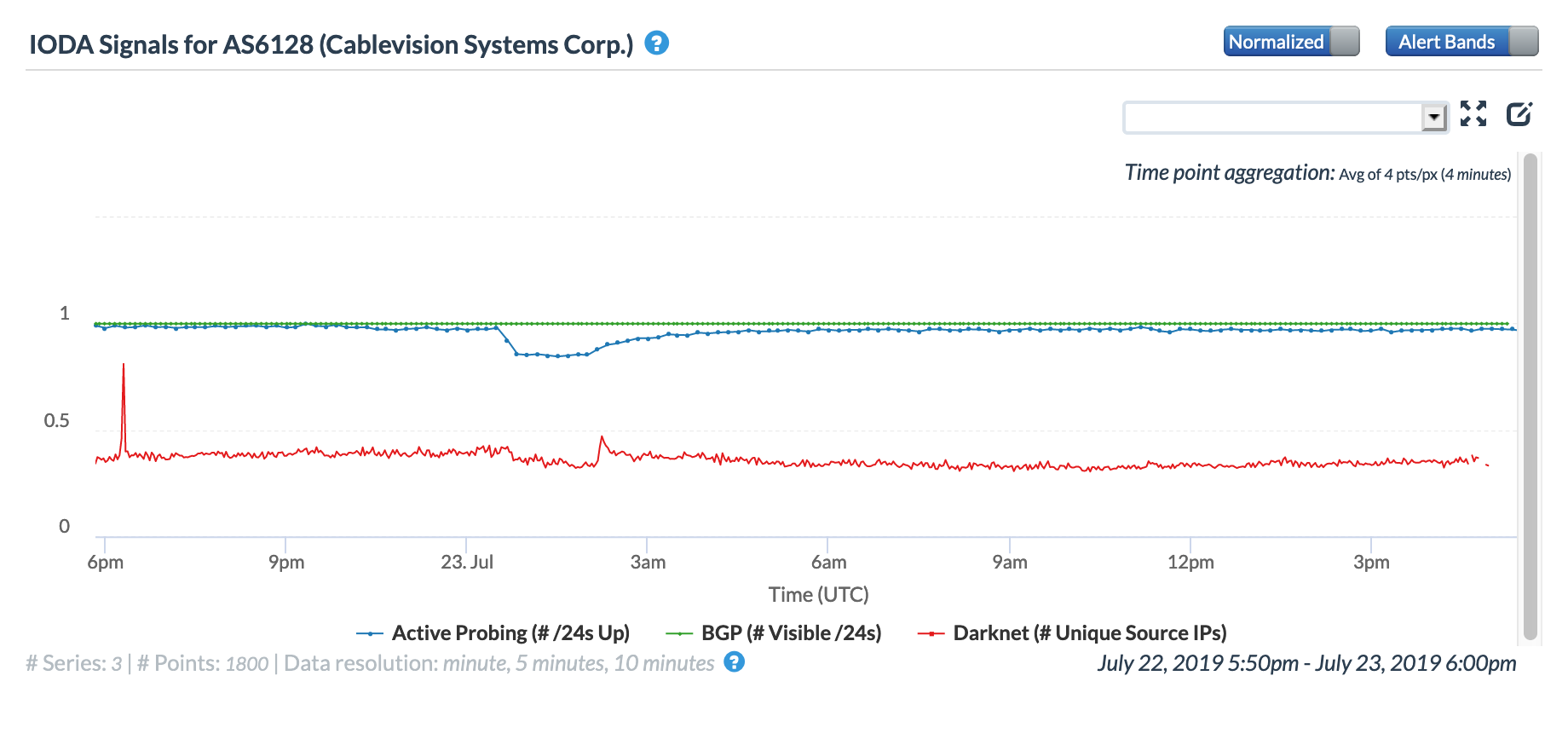
The disruption coincided with heavy rainstorms that hit the greater New York City area, and Optimum Online’s @OptimumHelp Twitter account confirmed that the observed outages were, in fact, storm-related.
On July 23, powerful storms hit several towns on Cape Cod in Massachusetts, spawning multiple tornadoes. At 12:12 (ET), a Boston-area weather forecaster Tweeted that the towns of South Brewster, East Harwich, and South Orleans were next up in the storm’s path. Just a few minutes later, Fing’s @outagedetect account Tweeted about an Internet outage impacting Comcast users in those towns. The associated detail view indicated that the disruption lasted for nearly 11 hours.
Fiber/Cable Issues
Late in the day (GMT) on July 7, the Gambia suffered a fairly significant multi-hour Internet disruption, as seen in the figure below. The BGP metric dropped to near-zero, indicating that a few of the country’s network prefixes were still being actively routed, which accounts for the continued traceroute and DNS activity.
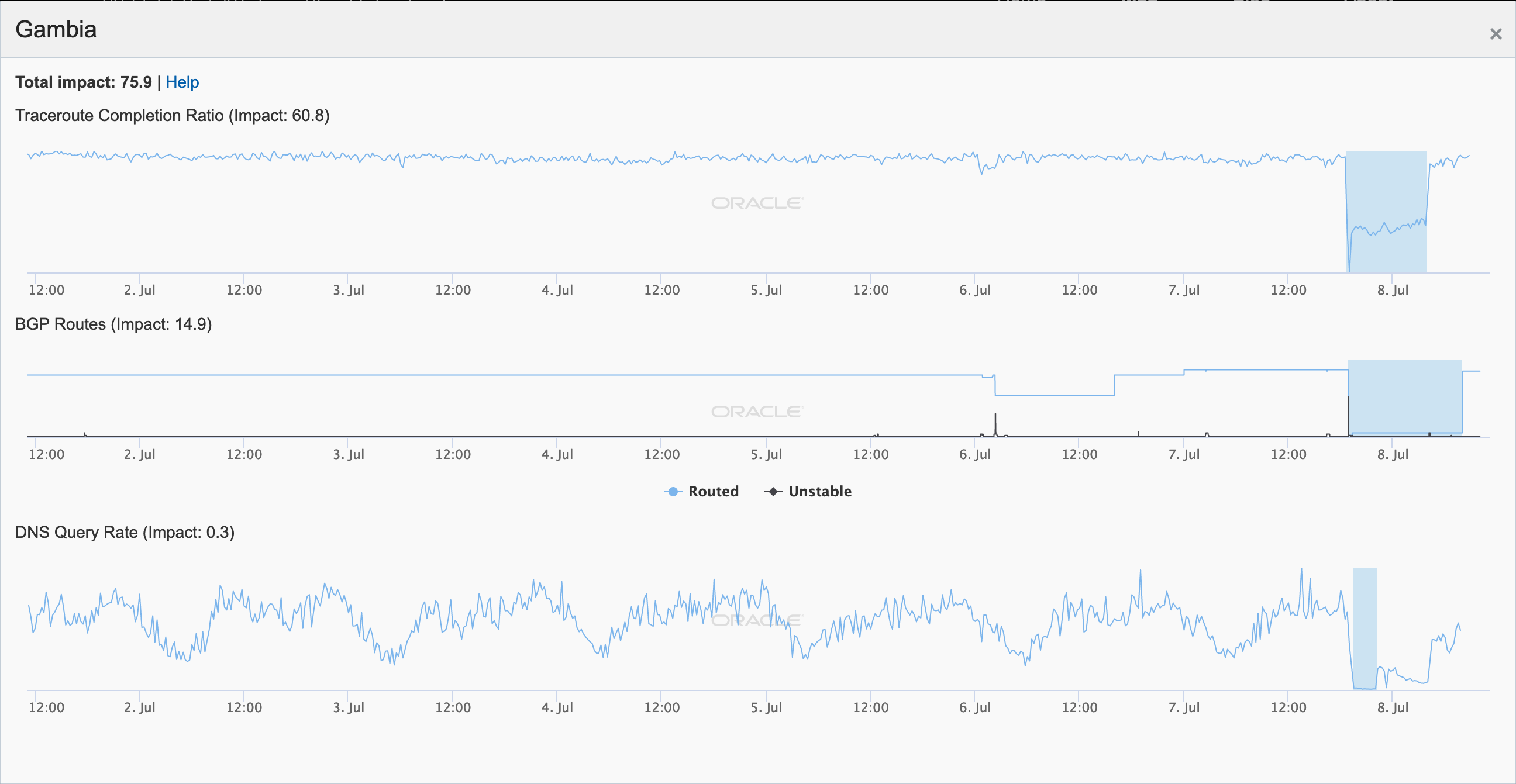
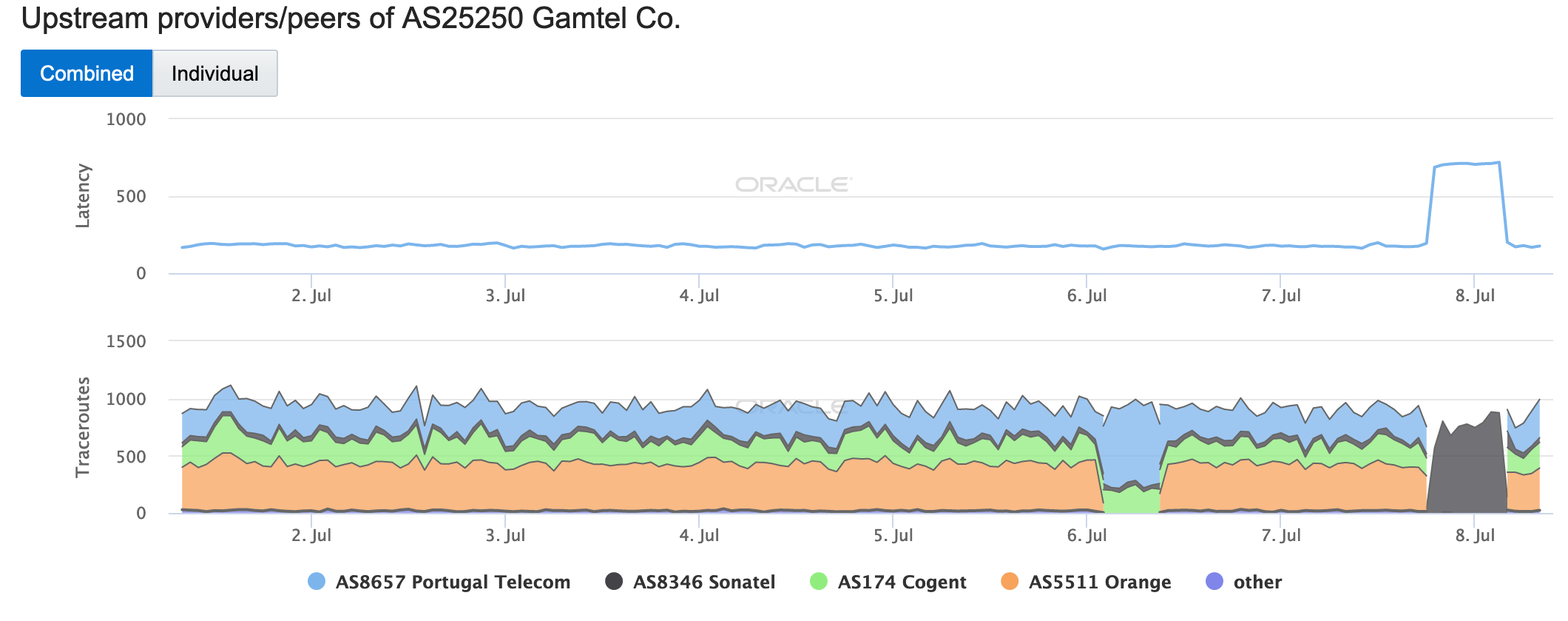
The next morning, Gambia Telecommunications Company (Gamtel) noted that the observed issue was related to technical issues at the gateway to the ACE (Africa Coast to Europe) submarine cable. While the country has other terrestrial international Internet connections, the ACE cable is its sole submarine connection. The impact to Gamtel’s Internet connectivity is shown in the figure below — latency spiked as traceroutes to endpoints within the country failed over to a connection through Sonatel, as paths through the other carriers became unavailable.
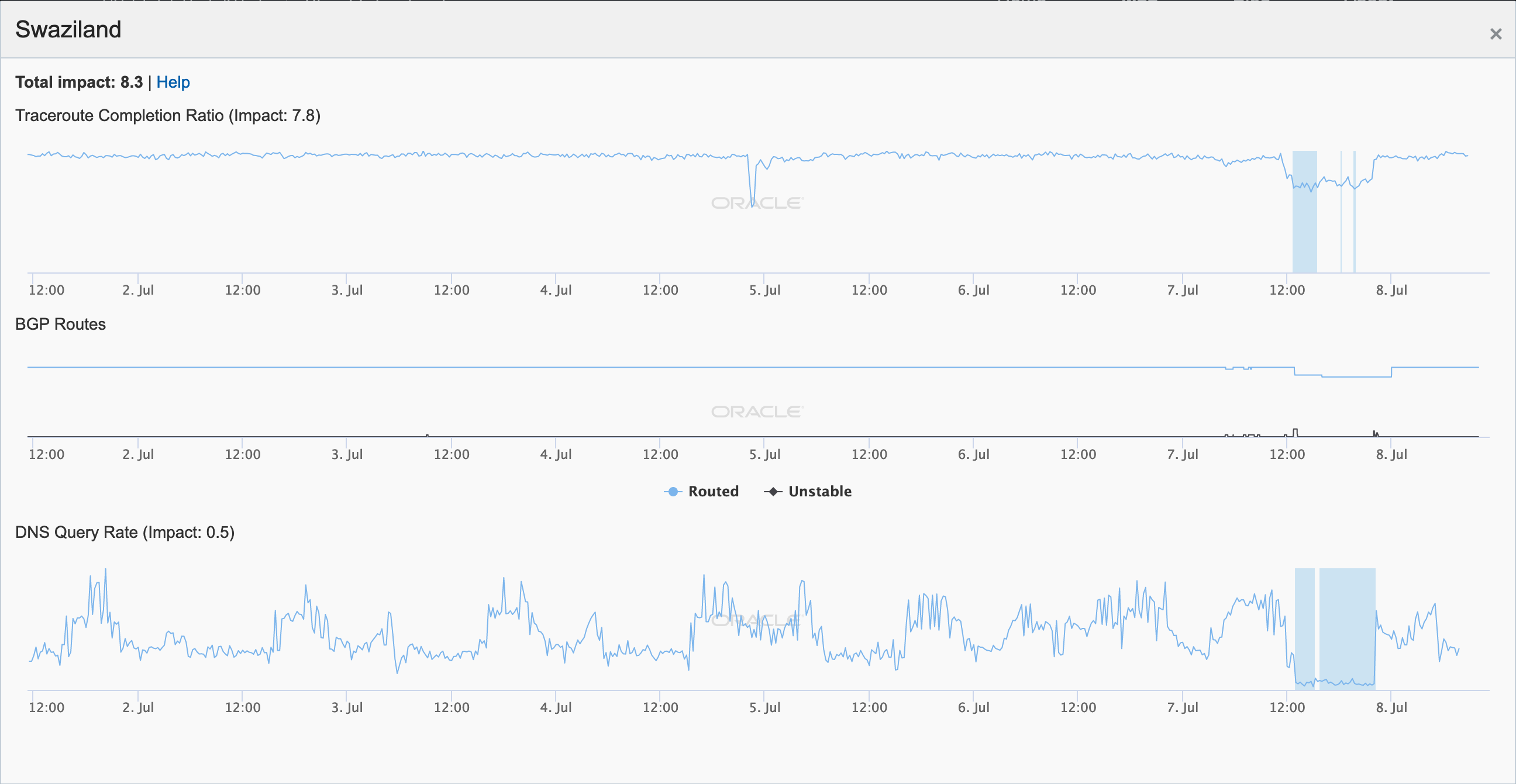
Earlier that same day, Swaziland also suffered an Internet disruption, as seen in the figure below. Although the traceroute and BGP metrics only showed a slight decline, the DNS query rate dropped significantly.
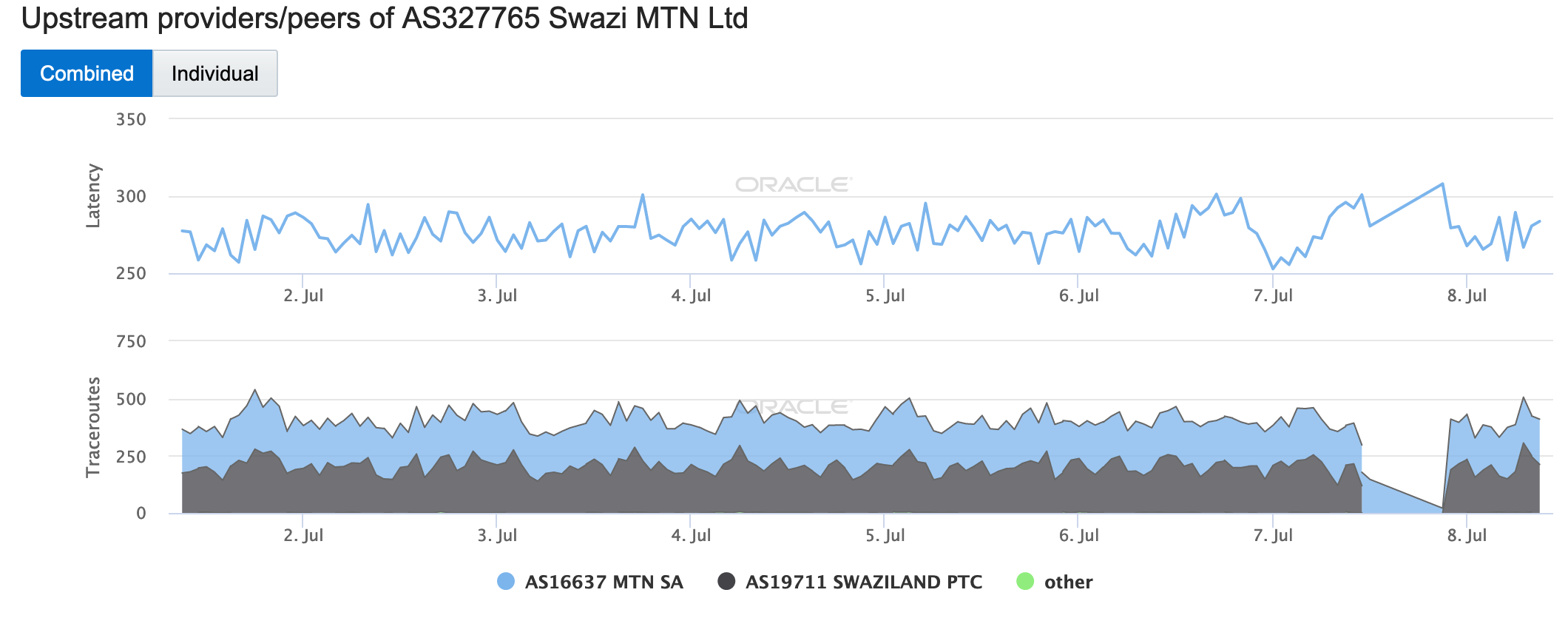
A significant disruption was observed at the same time at AS327765 (Swazi MTN), a Swazi telecommunications company. The figure below shows that during the disruptions, traceroutes to endpoints within the network completely stop transiting AS19711 (Swaziland PTC). The next day, @MTNSwaziland Tweeted an apology for the prior day’s disruption, noting that it was due to a fiber optic “breakdown” at Eswatini Post & Telecom Corporation – the same network noted above. (Swaziland was renamed “the Kingdom of eSwatini” in 2018.)
Unattributed Causes
In the Internet disruptions reviewed above, the root causes were discoverable thanks to news coverage of an associated event or a social media post by an impacted network service provider. However, there were a number of other disruptions observed across multiple countries in July where the root causes were unknown – no associated social media posts from impacted providers or known local events that could have had a significant impact to Internet connectivity. In addition, for many of these disruptions, the affected service providers did not respond to outreach on social media, including Twitter and Facebook.
United Kingdom
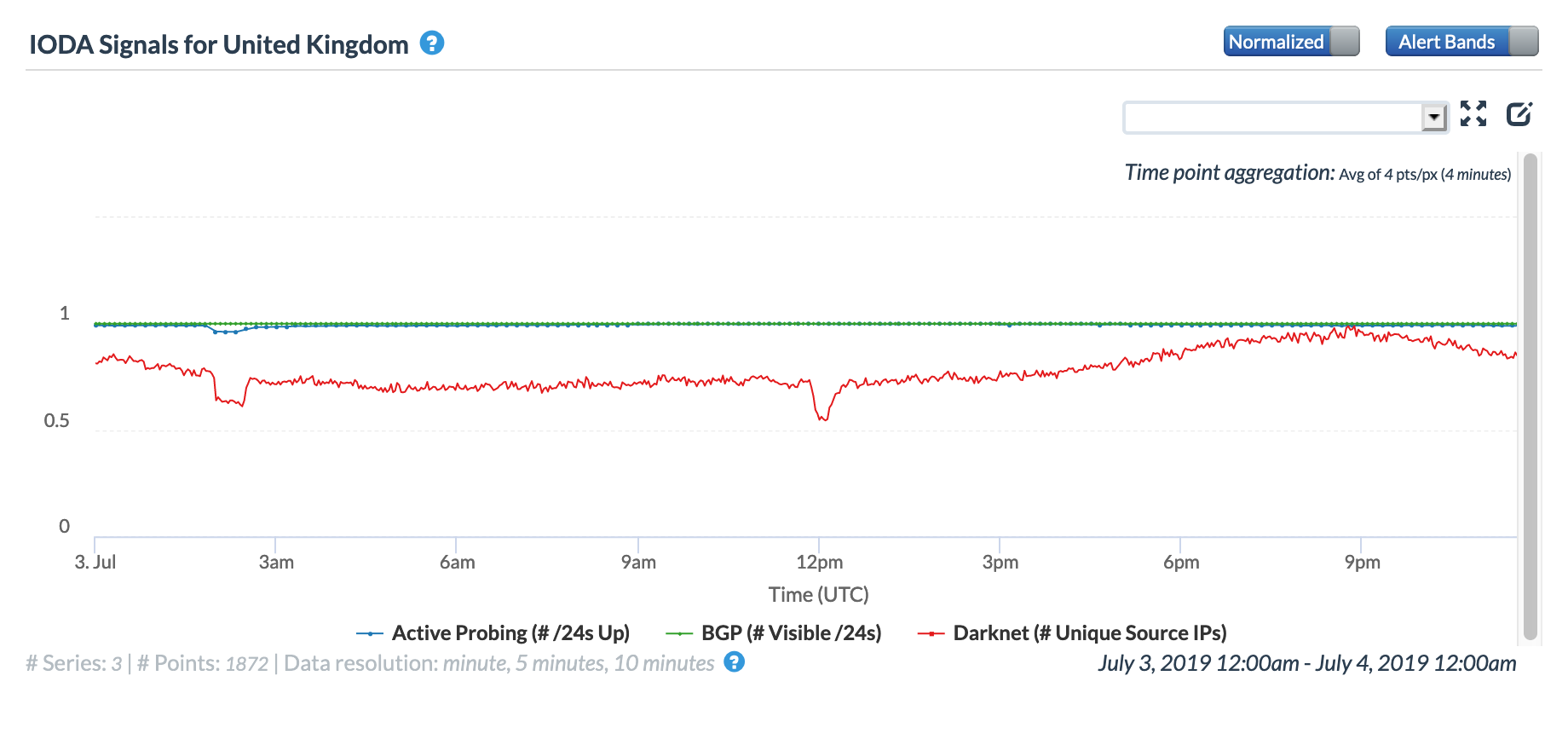
CAIDA IODA graph for United Kingdom, July 3 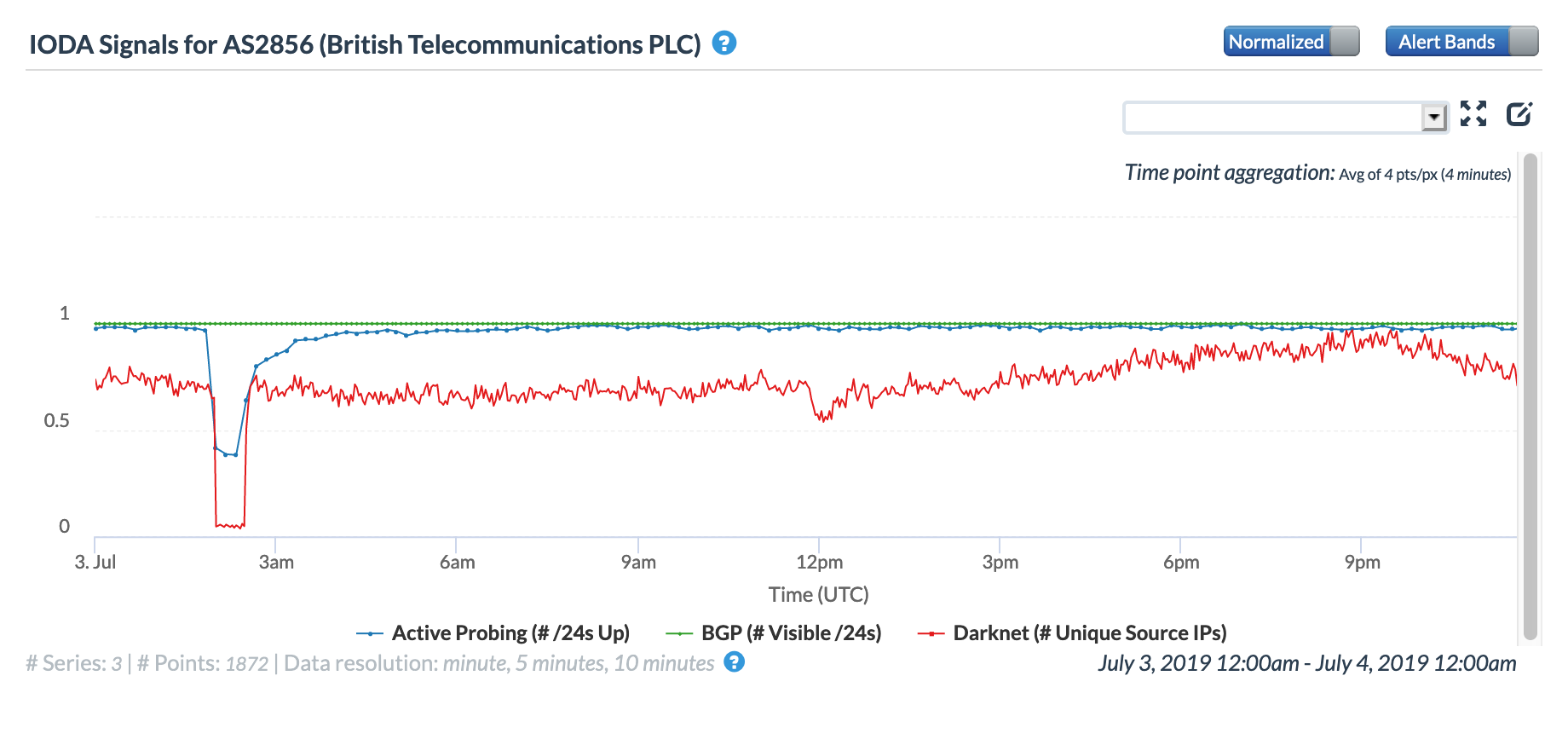
CAIDA IODA graph for AS2856 (BT), July 3
The Gambia
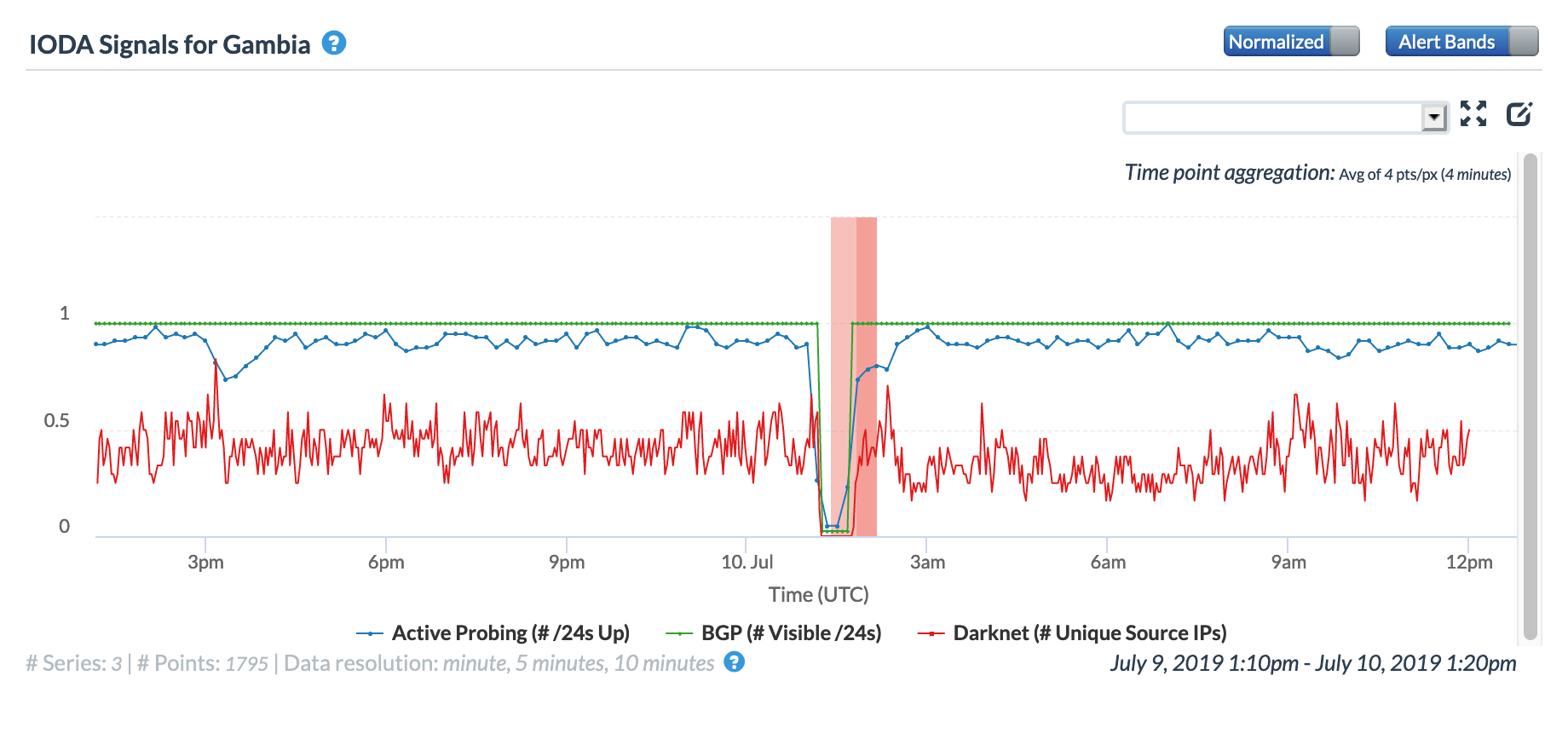
CAIDA IODA graph for Gambia, July 10 
CAIDA IODA graph for AS25250 (Gamtel), July 10
Togo
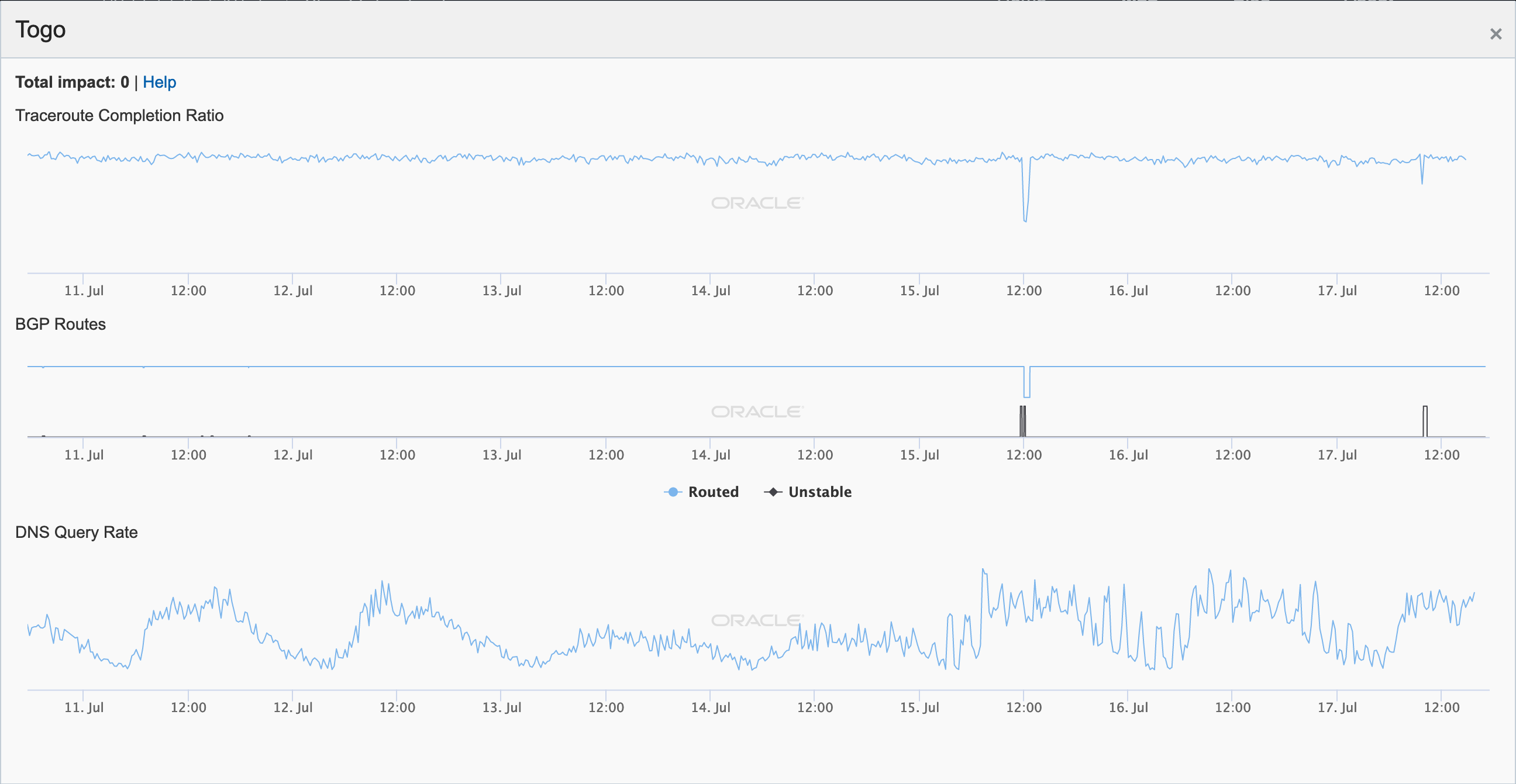
Oracle Internet Intelligence graph for Togo, July 10-17 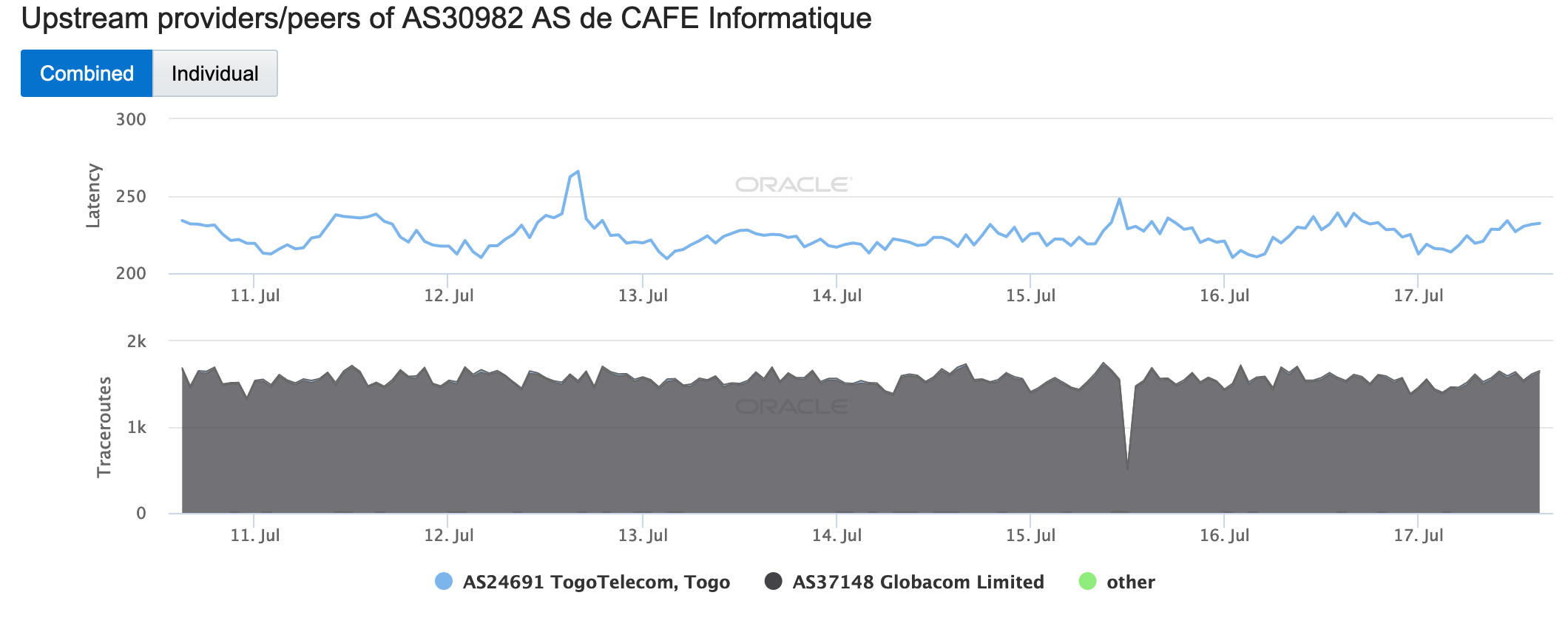
Oracle Internet Intelligence graph for AS30982 (Cafe Informatique), July 10-17 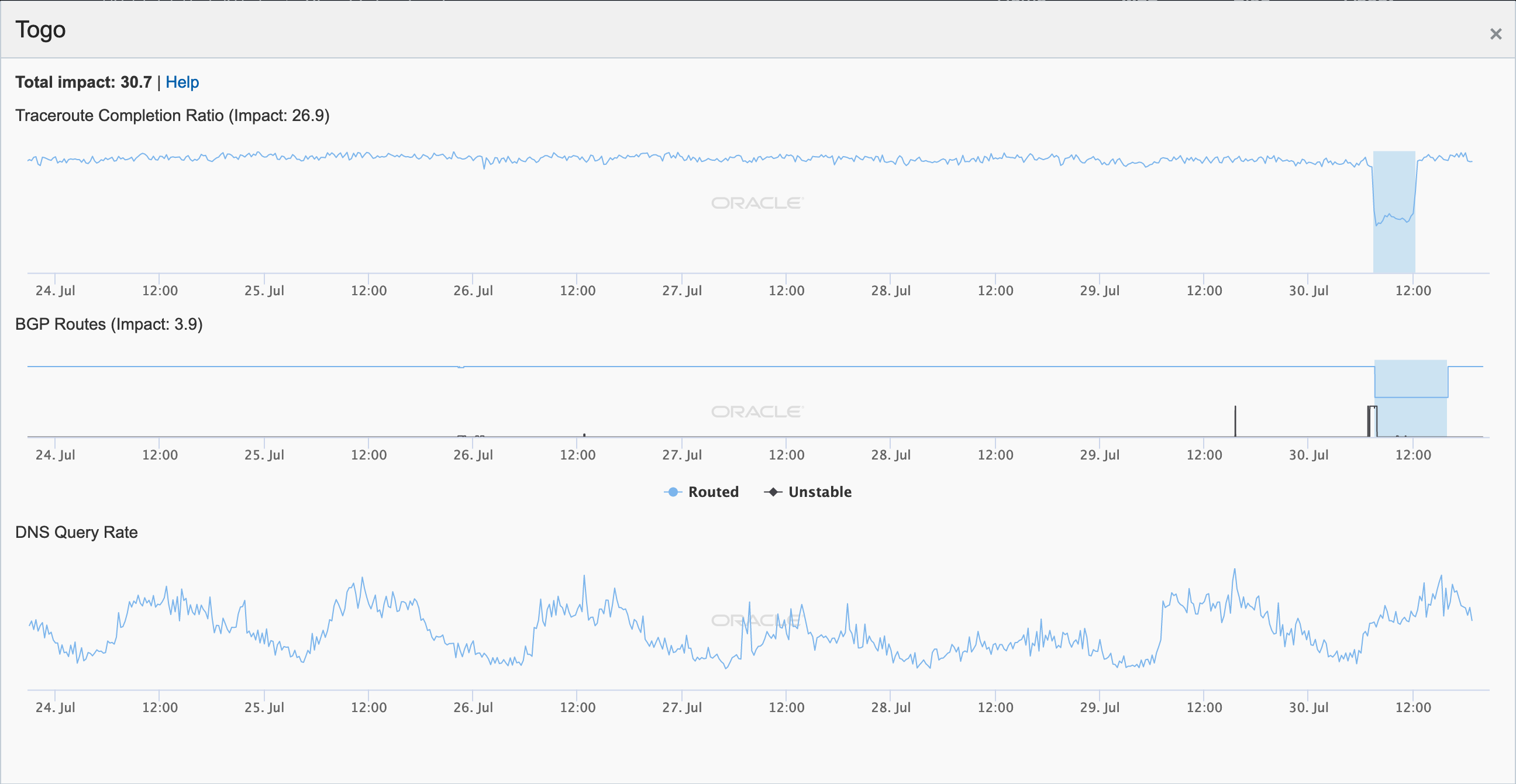
Oracle Internet Intelligence graph for Togo, July 23-30 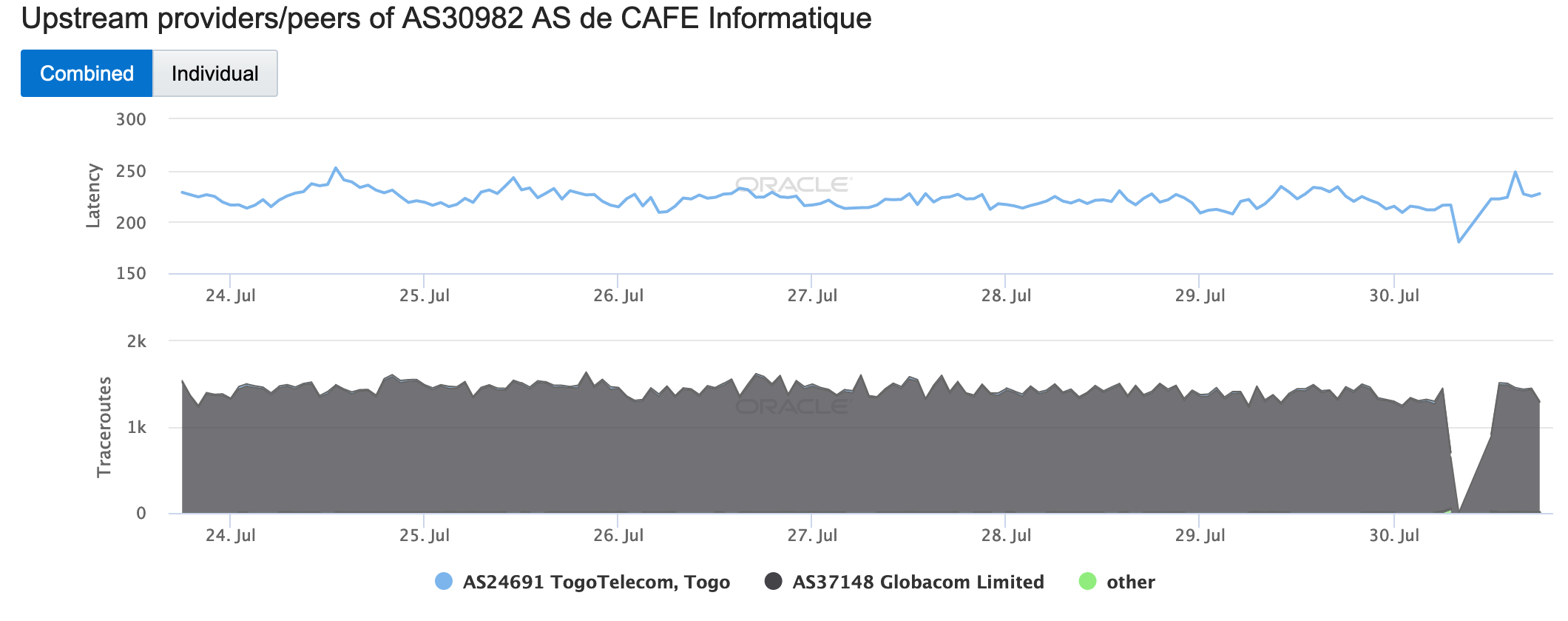
Oracle Internet Intelligence graph for AS30982 (Cafe Informatique), July 23-30
Congo
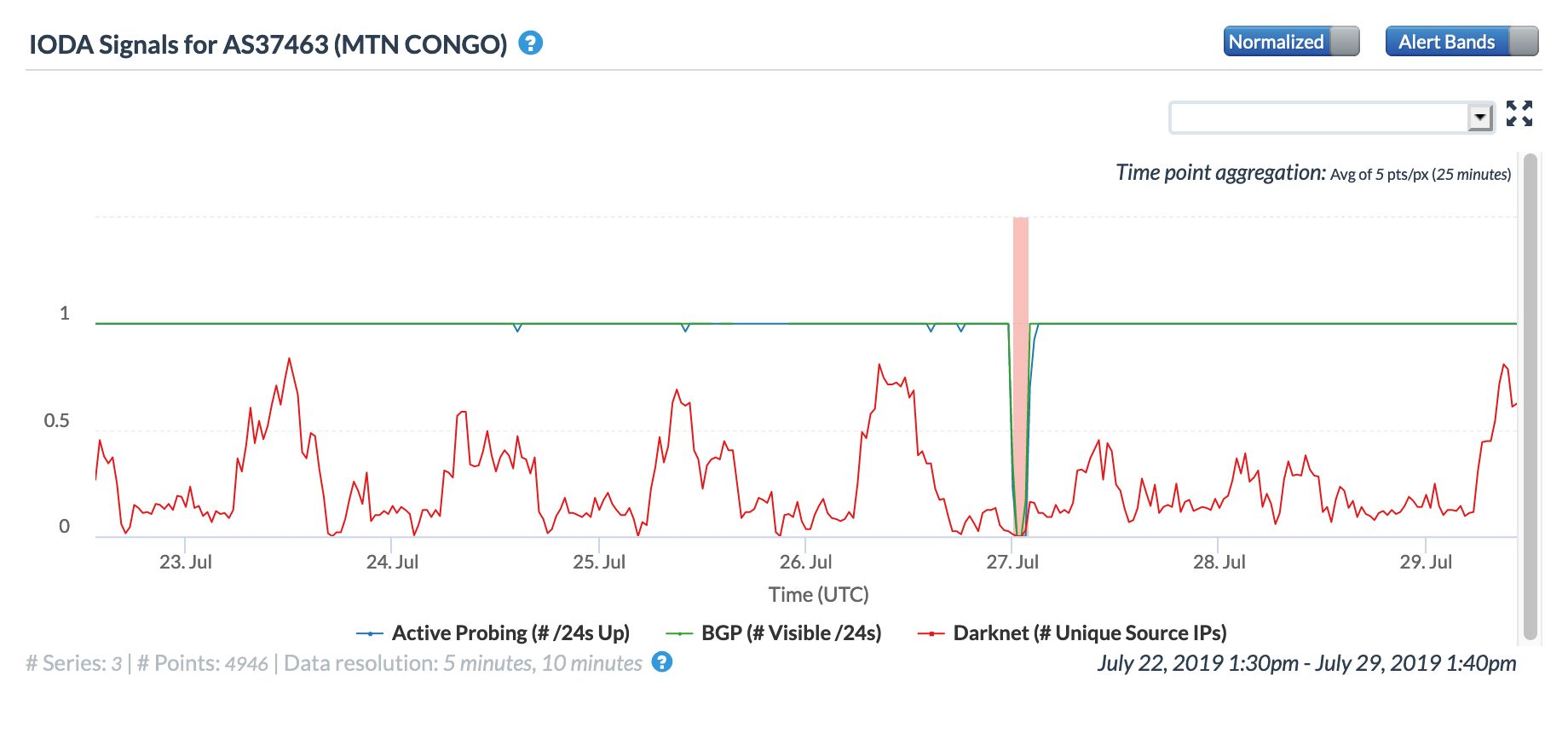
CAIDA IODA graph for AS37643 (MTN Congo), July 27 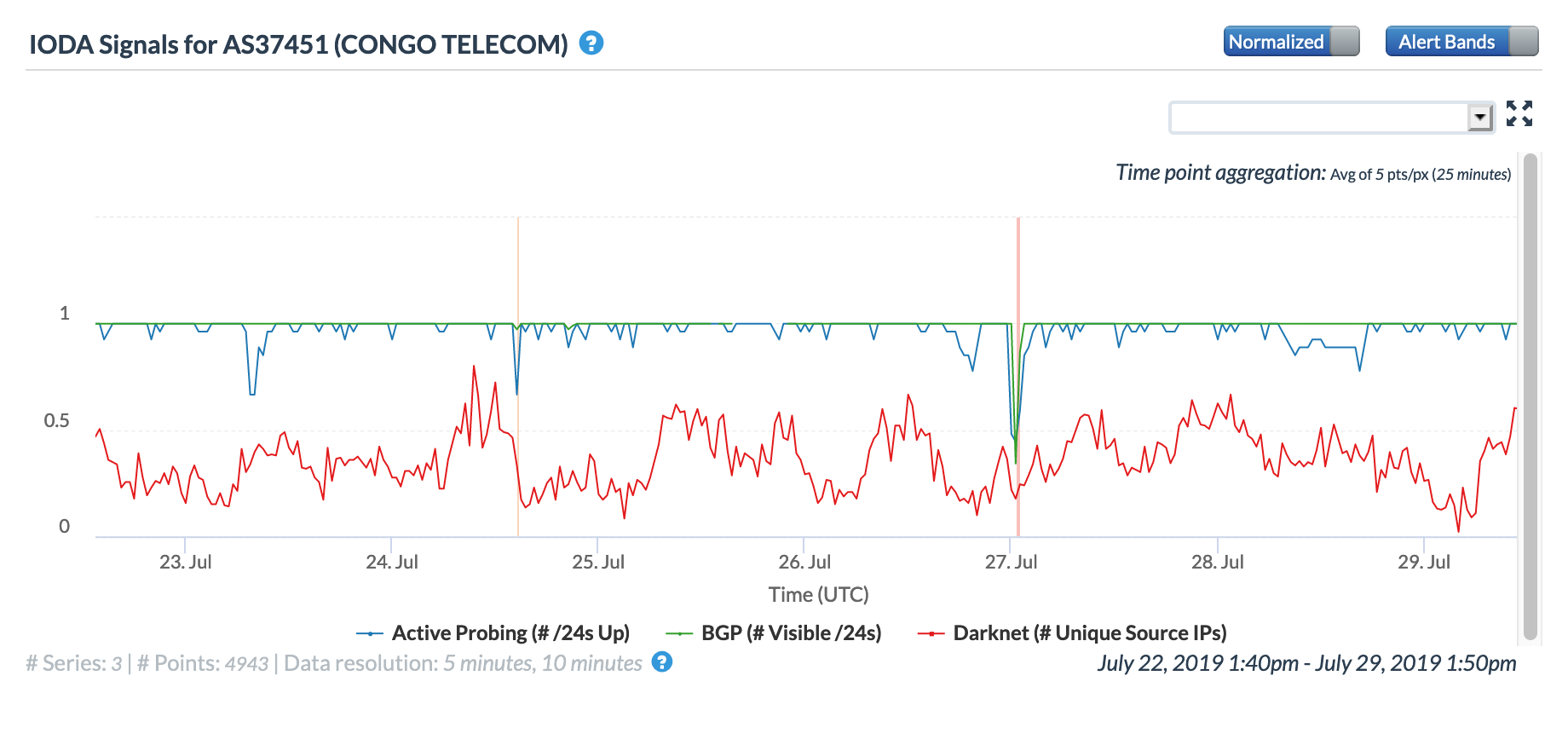
CAIDA IODA graph for AS37451 (Congo Telecom), July 27 
CAIDA IODA graph for AS37281 (OFIS-Computers), July 27 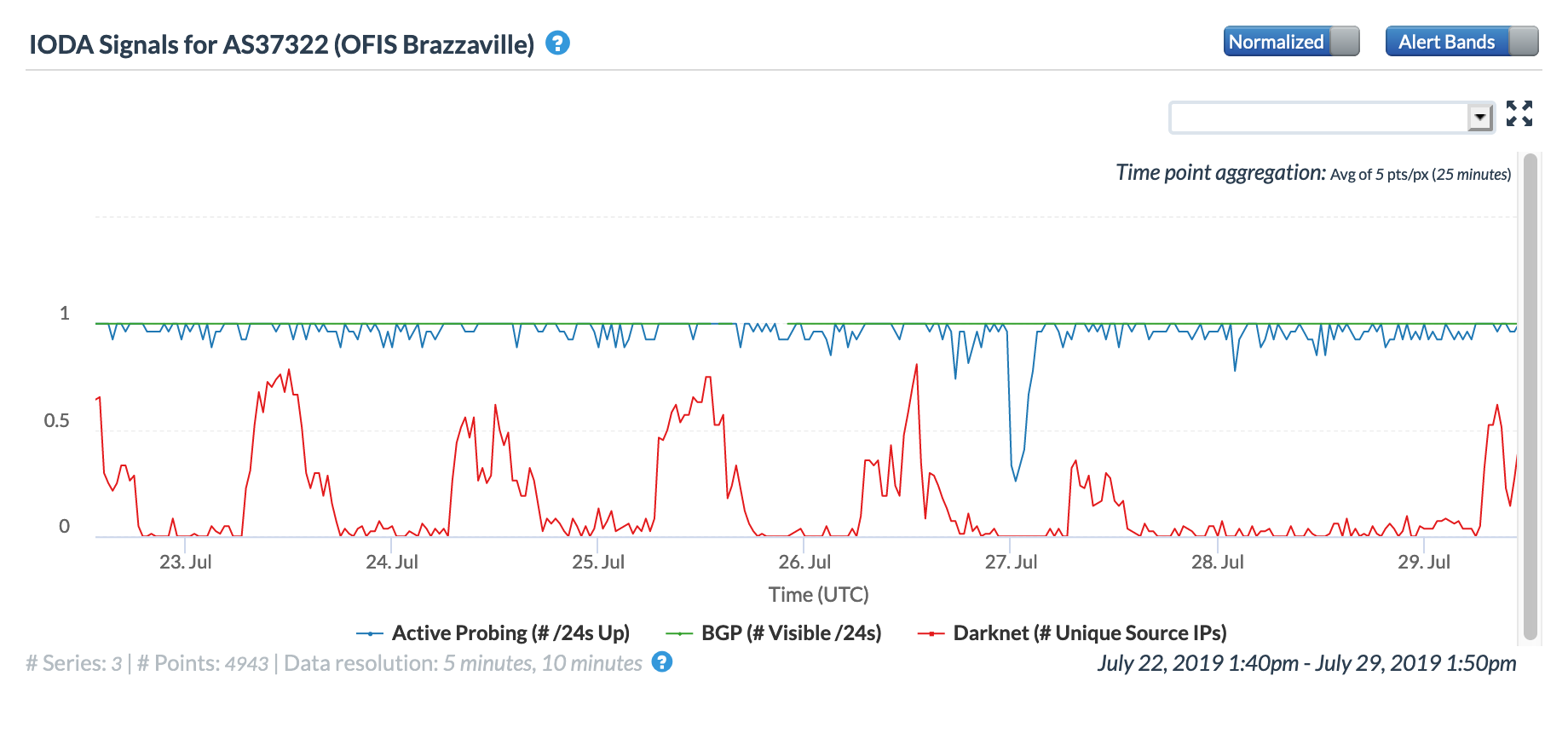
CAIDA IODA graph for AS37322 (OFIS Brazzaville), July 27
Gabon

CAIDA IODA graph for Gabon, July 29 
CAIDA IODA graph for AS16058 (Gabon Telecom), July 29
Saint Barthelemy
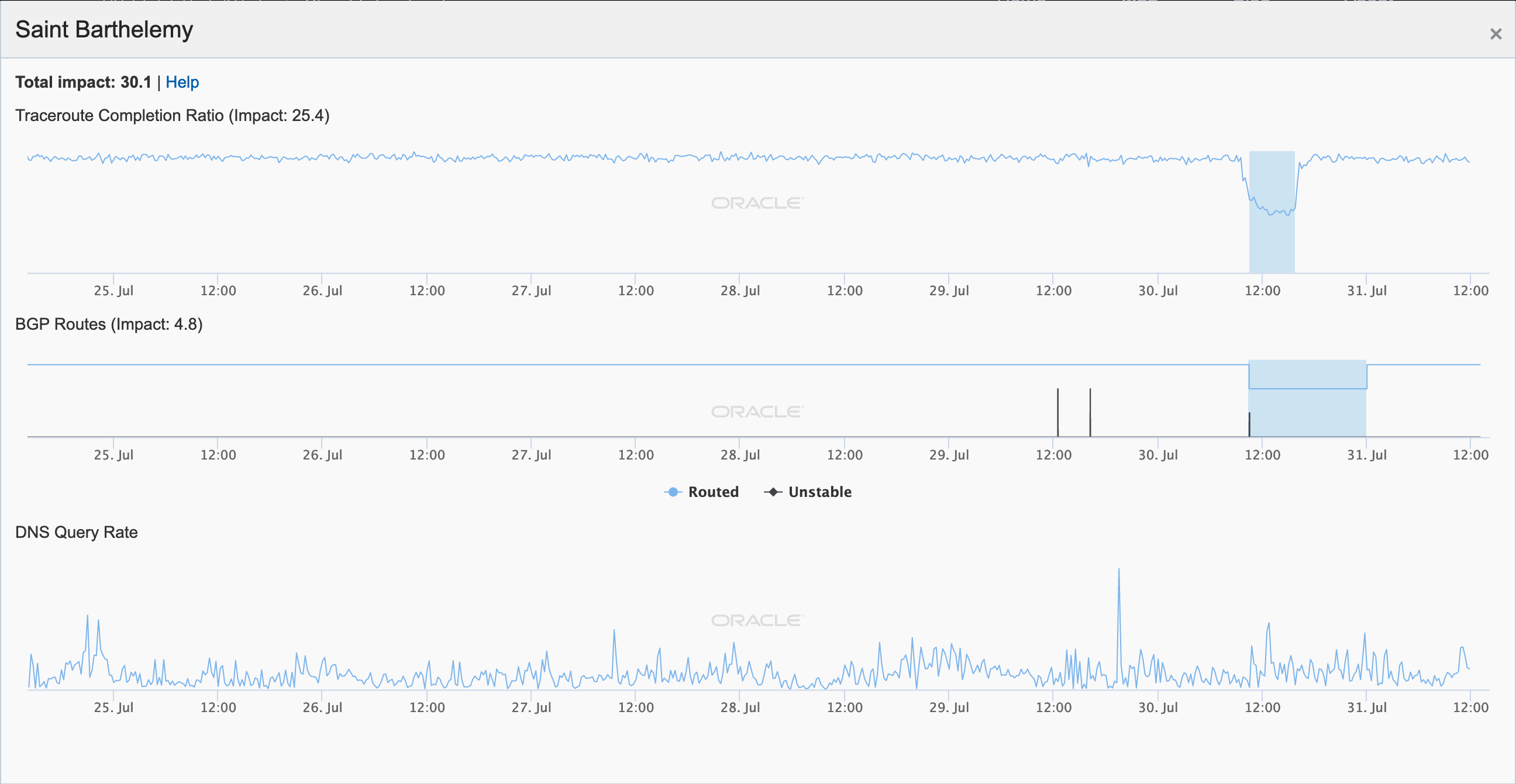
Oracle Internet Intelligence graph for Saint Barthelemy, July 30
Conclusion
Information and data on the severity, duration, and extent of Internet disruptions, both at national and local scales, is becoming increasingly available through organizations like Oracle Internet Intelligence, CAIDA IODA, Fing Internet Alert, the Google Transparency Report, Netblocks, and the Monash University IP Observatory. As such it is becoming easier to learn about and publicize such disruptions when they occur, and to hold the providers accountable for these disruptions.
As seen above and in past posts, many providers are transparent, and use social media to explain (and sometimes even apologize for) what happened. However, many providers not only fail to proactively provide information to their subscribers and the public when such events occur, but they also fail to reply to inbound requests for additional information. (Compounding the problem, some have social media presences that have been inactive for months or years.)
We call on telecommunication and network service providers to be more transparent and more active on social media with respect to providing insights into the causes of observed disruptions, and to actively monitor their social media presence for inbound requests for information. (And of course, to respond to those requests in a timely fashion).
]]>Cable Complications
Greenland receives international Internet connectivity via the Greenland Connect submarine cable, linking the country to Iceland and Canada through landing points in Nuuk and Qaqortaq. In December 2018, the submarine cable link between these two cities suffered damage, disrupting Internet connectivity for users in Greenland. TELE-POST, a subsidiary of national telecommunications company TELE Greenland, has been tracking cable repair efforts over the last several months — efforts that have been slowed due to weather and ice cover.
Some repairs took place in early May, stabilizing Internet connectivity for users in North Greenland. However, disruptions to Internet connectivity in Greenland were also observed during this time frame, as seen in the figures below. While it has not been definitively confirmed that these disruptions were, in fact, due to cable repair efforts, TELE-POST has noted on the status site that connectivity for some customers may be turned on/off while repair efforts are underway.
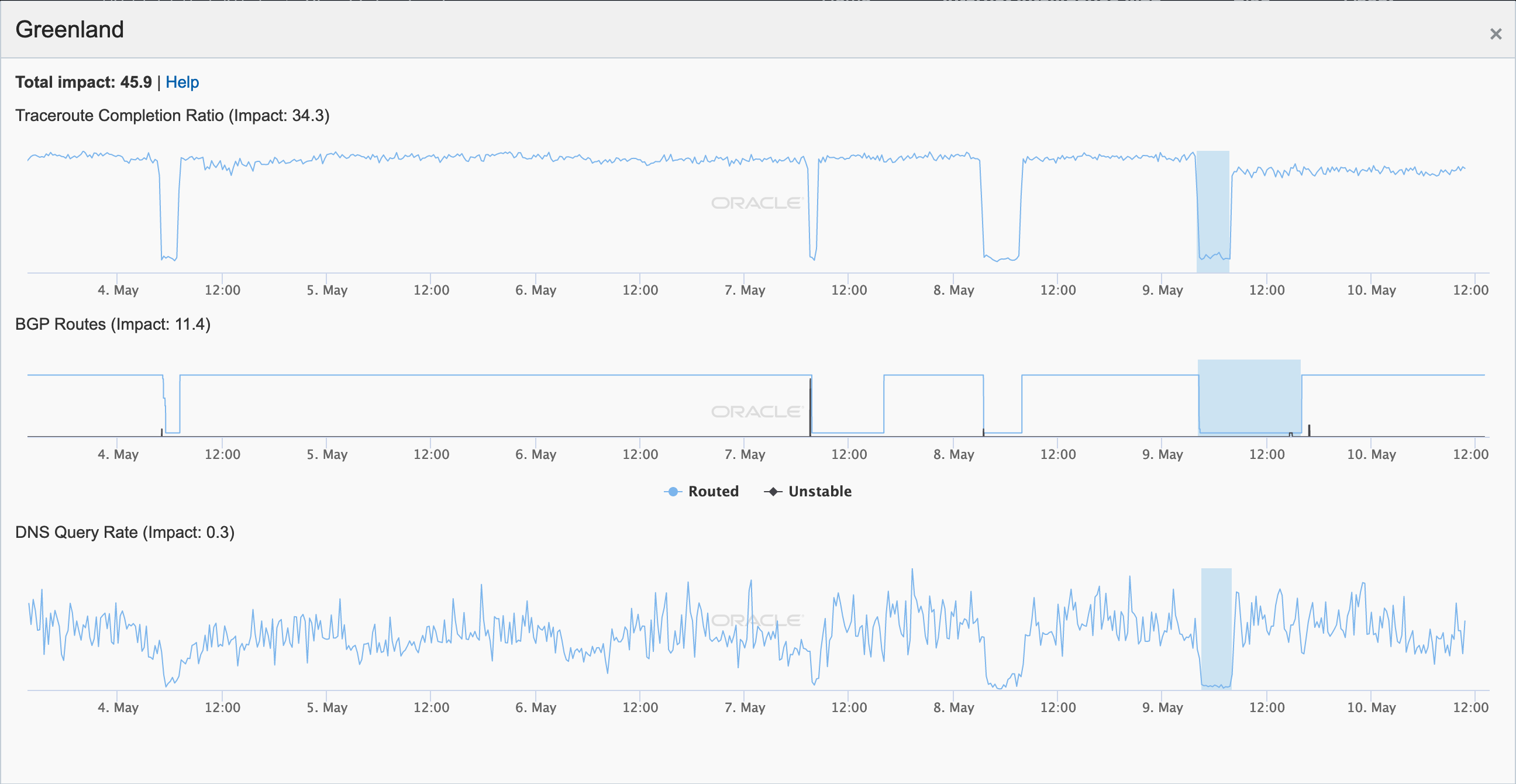
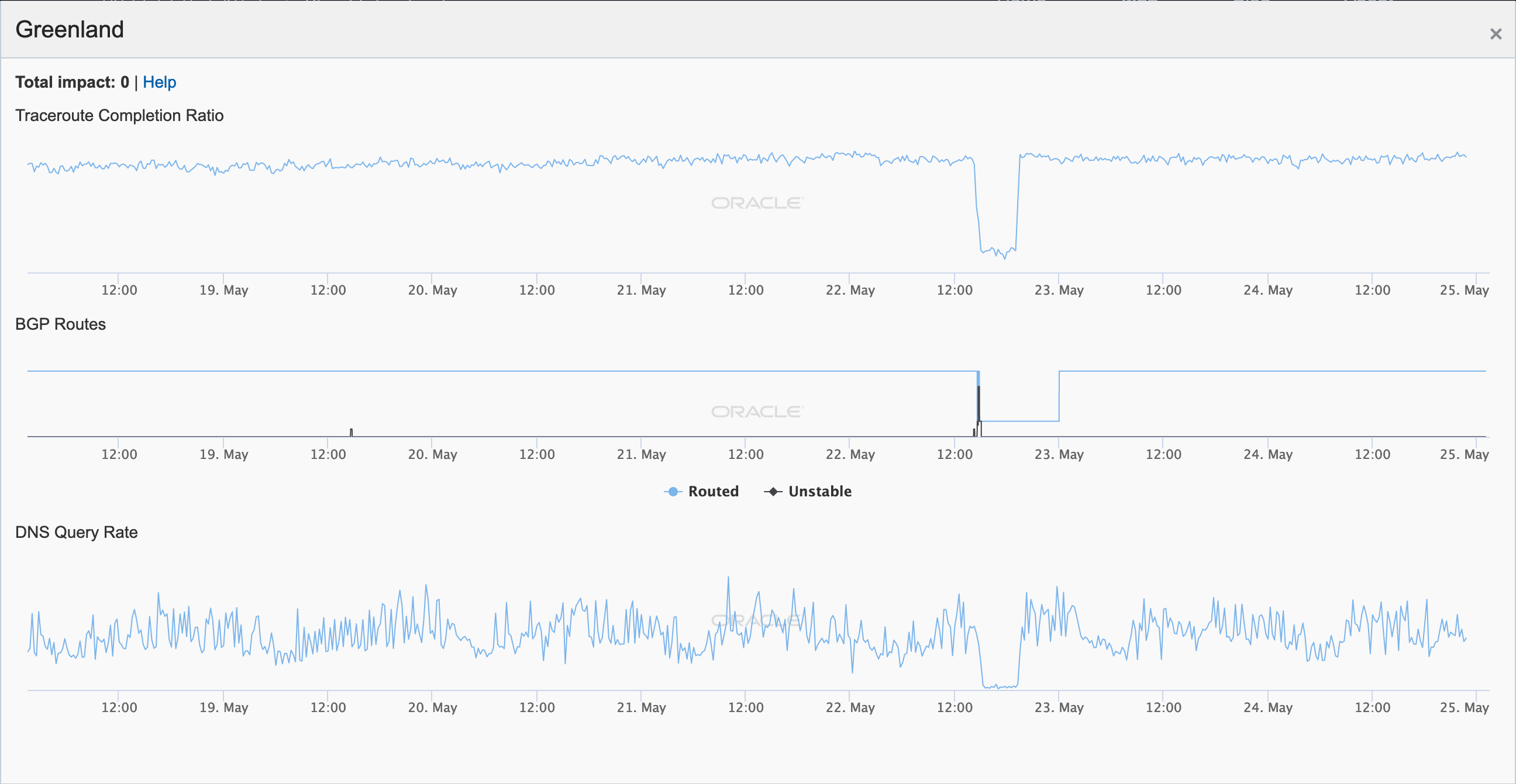
A similar disruption was also observed on May 22, as shown in the figures below. That day, TELE-POST noted that it would be postponing repair work until August due to ice conditions. It is likely that similar disruptions will continue to occur over the coming months, as the update states: “However, in the coming period, until the important repair work next to Qaqortoq has been completed, there will be an increased risk of operational disturbances, particularly of the Internet service.”
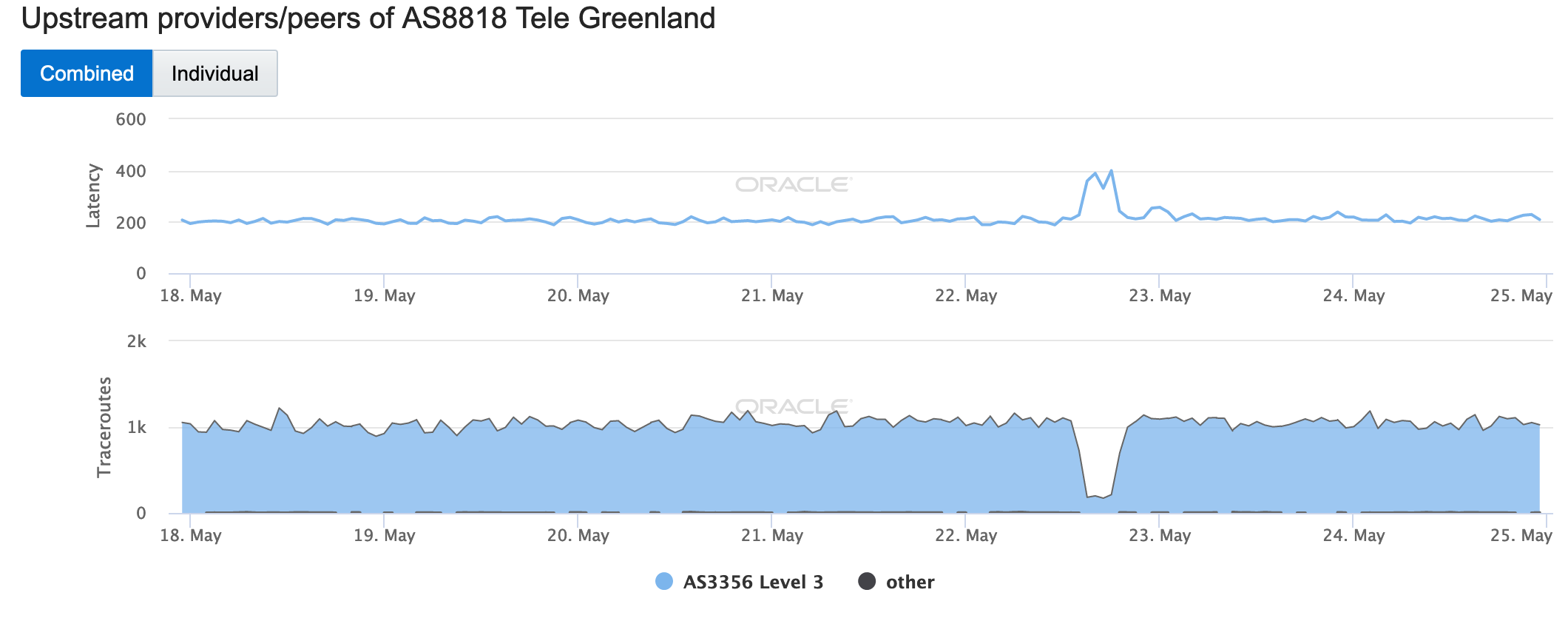
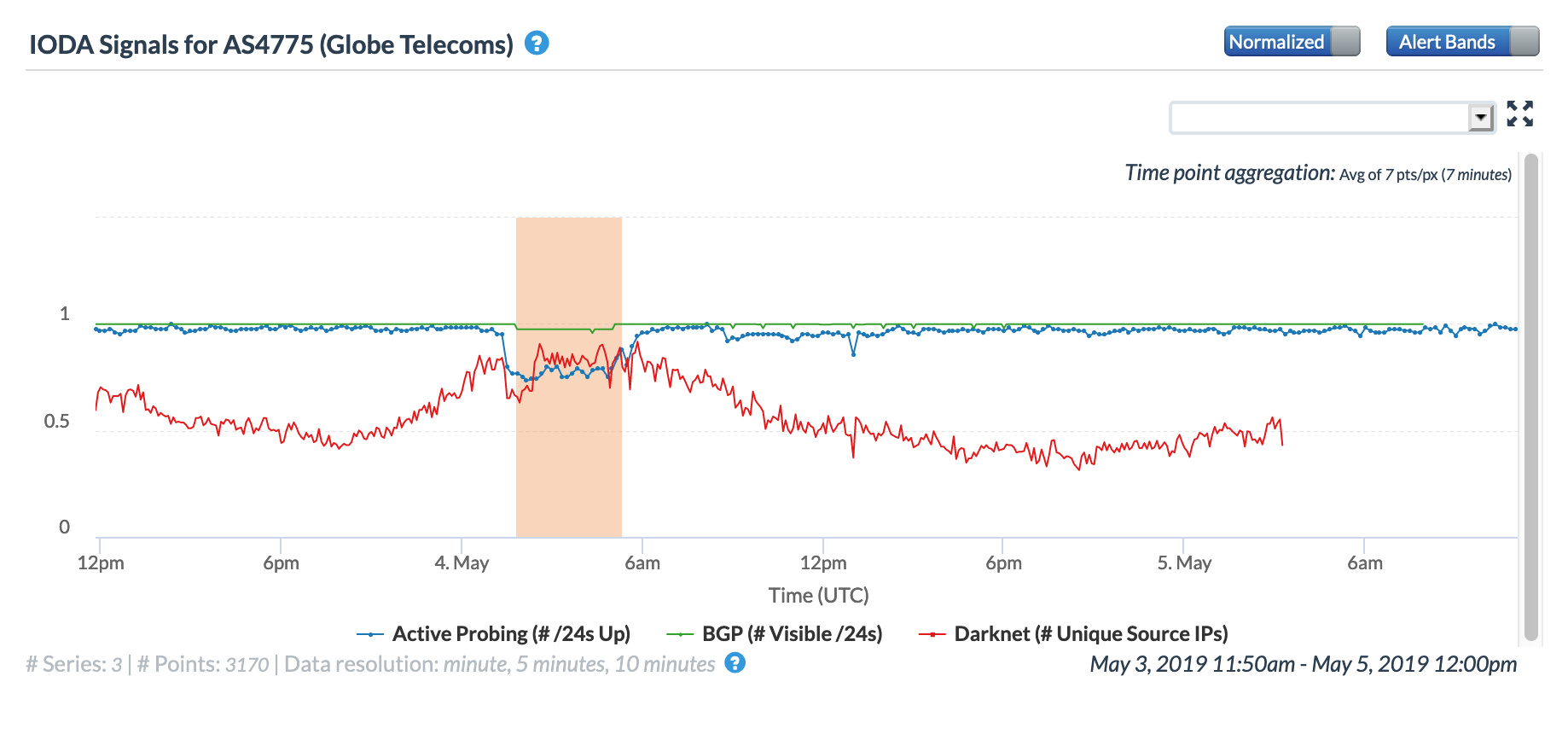
On May 4, Globe Telecom subscribers in several regions of the Philippines experienced Internet service disruptions due to damaged fiber optic cables. A submarine cable was damaged by a 5.5-magnitude earthquake, while another cable was damaged by a vehicle dragging the cable at a road crossing. The figure below shows the impact of the cable damage to connectivity for AS4775 (Globe Telecom) – a minor change was seen in BGP, while successful active probing was impacted for just over three hours; measured darknet traffic dropped briefly at the start of the event, but appeared to recover quickly.
Apparently a popular day for Internet disruptions, Haiti also experienced an issue during the afternoon of May 4, as shown in the figure below. According to a number of Twitter responses from Digicel Haiti (@DigicelHT) to user complaints, the brief disruption was related to issues with a submarine cable.
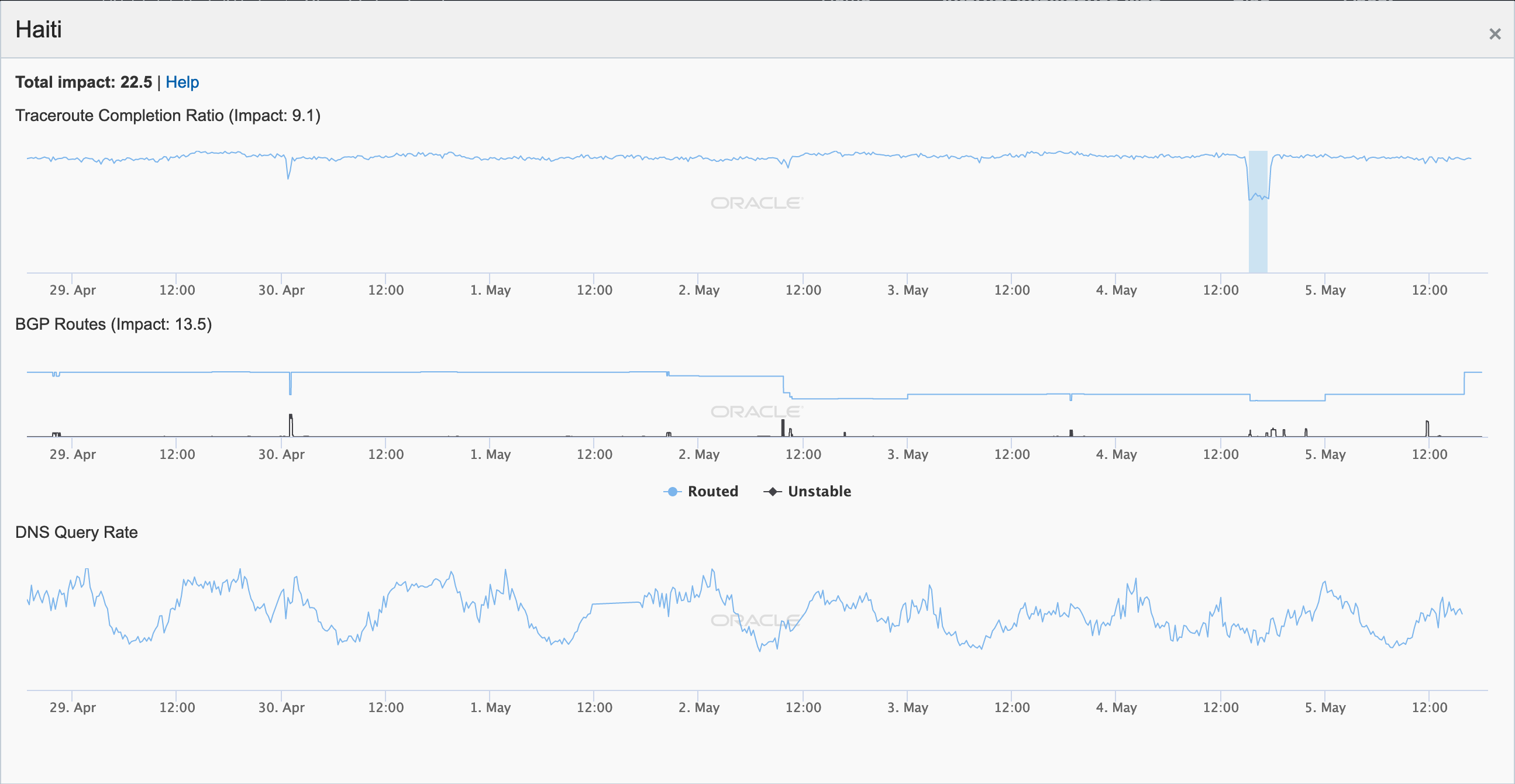
The figure below shows that connectivity to Digicel Haiti through Digicel Jamaica was disrupted. The Fibralink submarine cable connects the two countries, so it may have been the cable referenced (but not named) in the @DigicelHT Tweets.
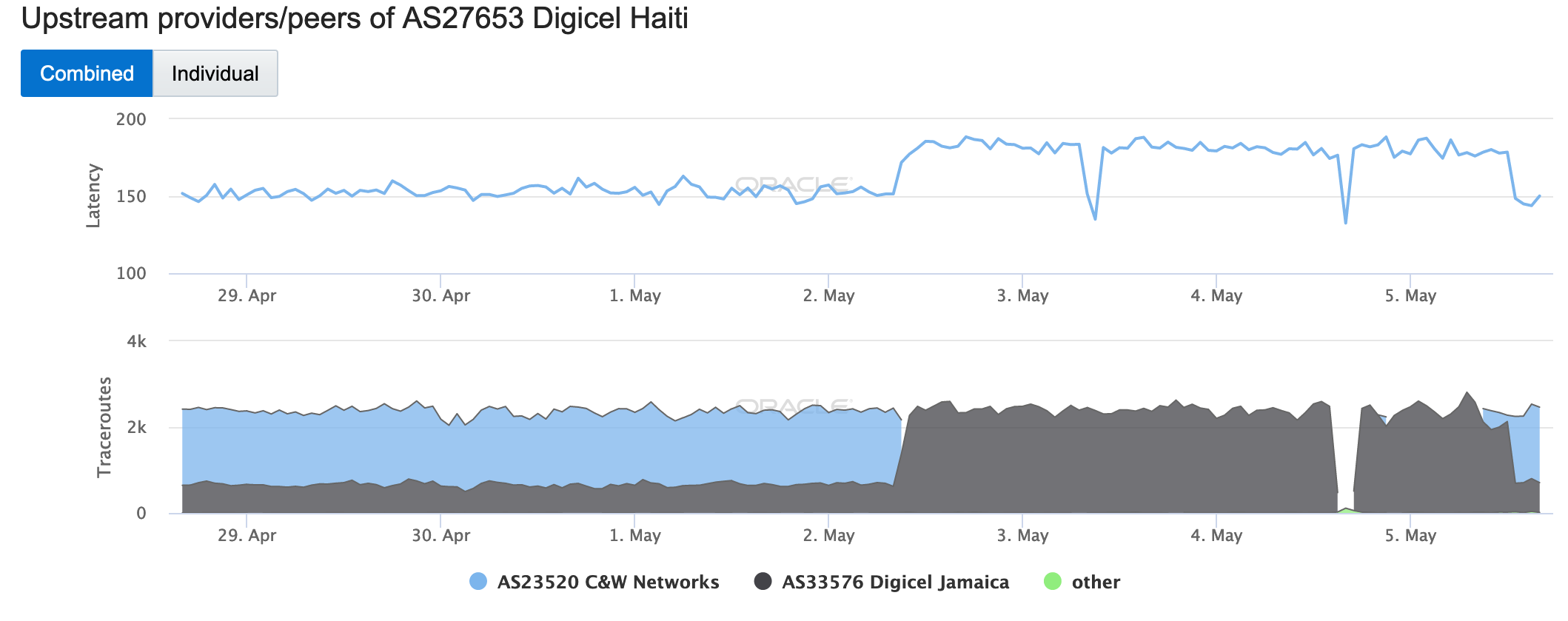
Just over two weeks later on May 19, AS15964 (Cameroon Telecommunications Network) experienced a connectivity disruption. As shown in the figure below, the number of traceroutes to endpoints in the network going through Tata dropped significantly for several hours, with Telxius and Orange picking up the slack.
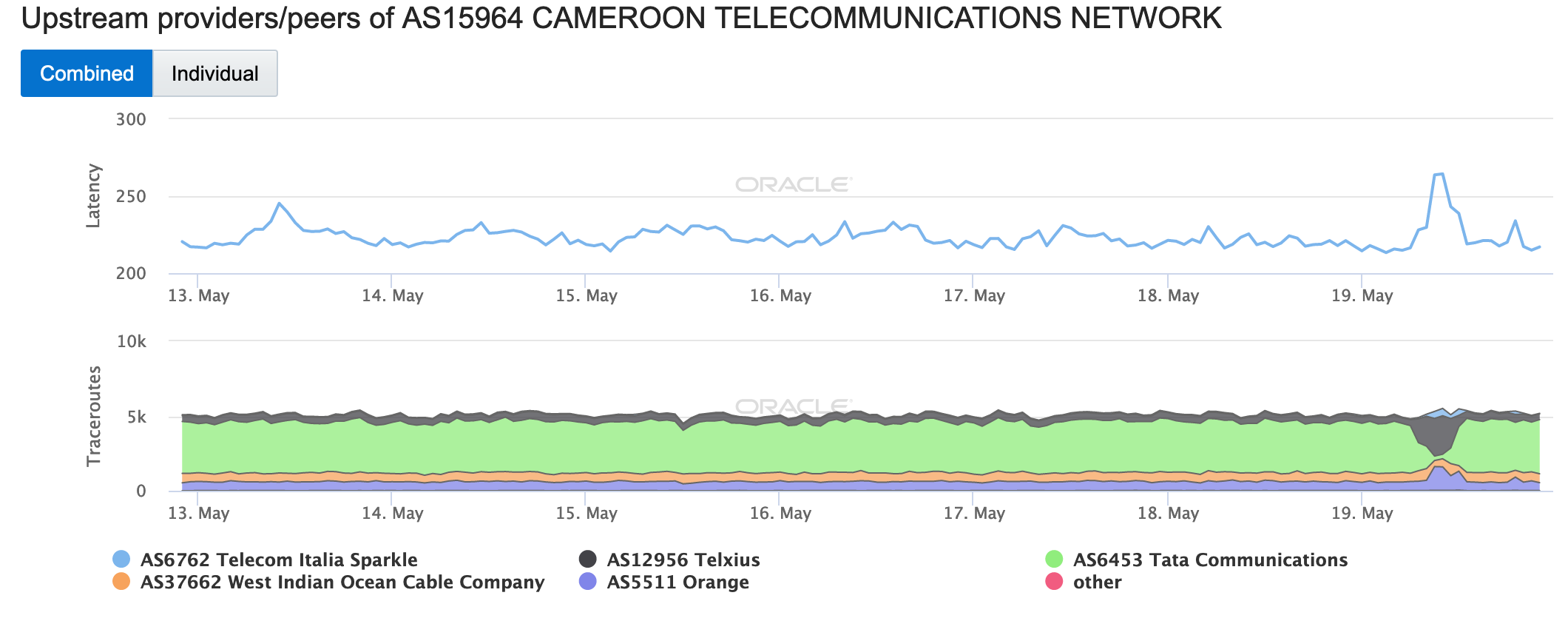
This disruption impacted downstream networks in different ways. The figures below illustrate the impact of the disruption to two of those networks – AS30992 (MTN Cameroon) and AS37620 (VIETTEL CAMEROUN SARL). The number of successful traceroutes to endpoints in MTN declined by approximately half during the disruption period, while the number of traceroutes to endpoints in VIETTEL going through Cameroon Telecommunications Network unexpectedly increased during that period, although that shift also brought a significant increase in latency.
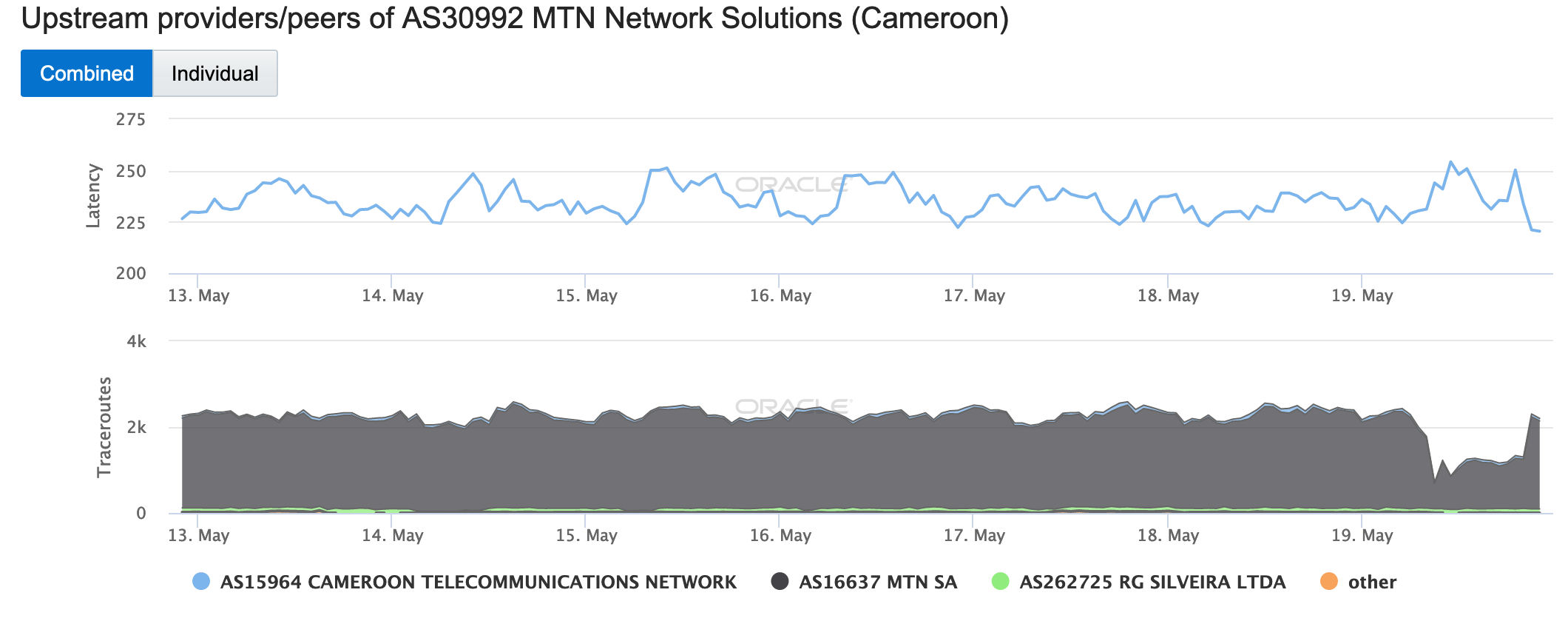
Oracle Internet Intelligence Map Traffic Shifts graph for AS30992 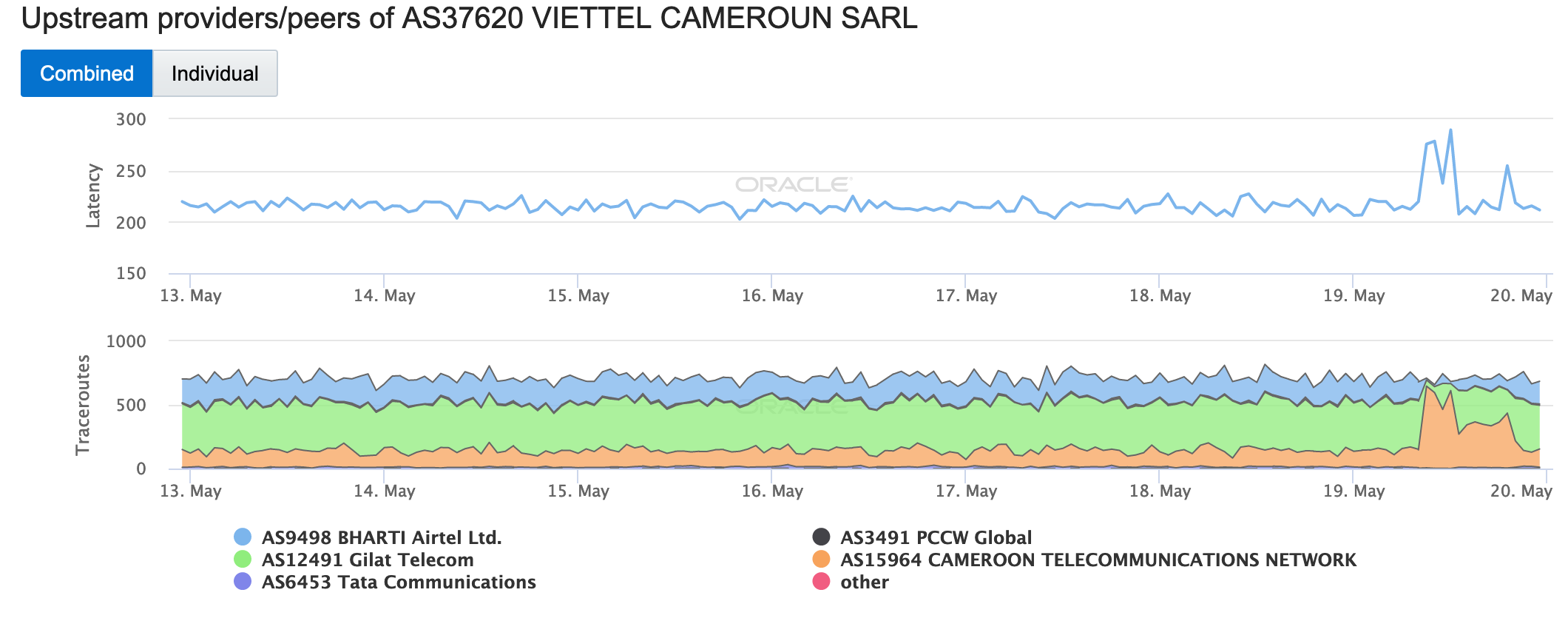
Oracle Internet Intelligence Map Traffic Shifts graph for AS37620
In a Tweet from @MTNCameroon that was subsequently deleted, the company acknowledged the apparent connectivity issues. The deleted Tweet was in response to a user complaint that included what appeared to be a screenshot of a text message that reads (via Google Translate) “Dear customer, following an incident on the optical fiber provided to us, our network is momentarily disrupted. MTN sexcuse for possible inconvenience.” This same (original) text was also Tweeted by several other users (1, 2) that same day. However, it is also worth noting that the text appears in Tweets from February 2019 and October/September/June/April 2018, so it may just be a stock customer support response from MTN Cameroon, rather than a definitive root cause.
On May 21 & 22, Malawi held elections to name a President, new members of Parliament, and local councilors. After the polls closed, Internet connectivity was disrupted across multiple providers in the country, reportedly due to damage to a cable owned by Malawi Telecommunications Limited. The figure below shows the impact to Internet connectivity for AS36969 (Malawi Telecommunications Limited) – successful active probing trended lower for several hours, and darknet activity was reduced as well.
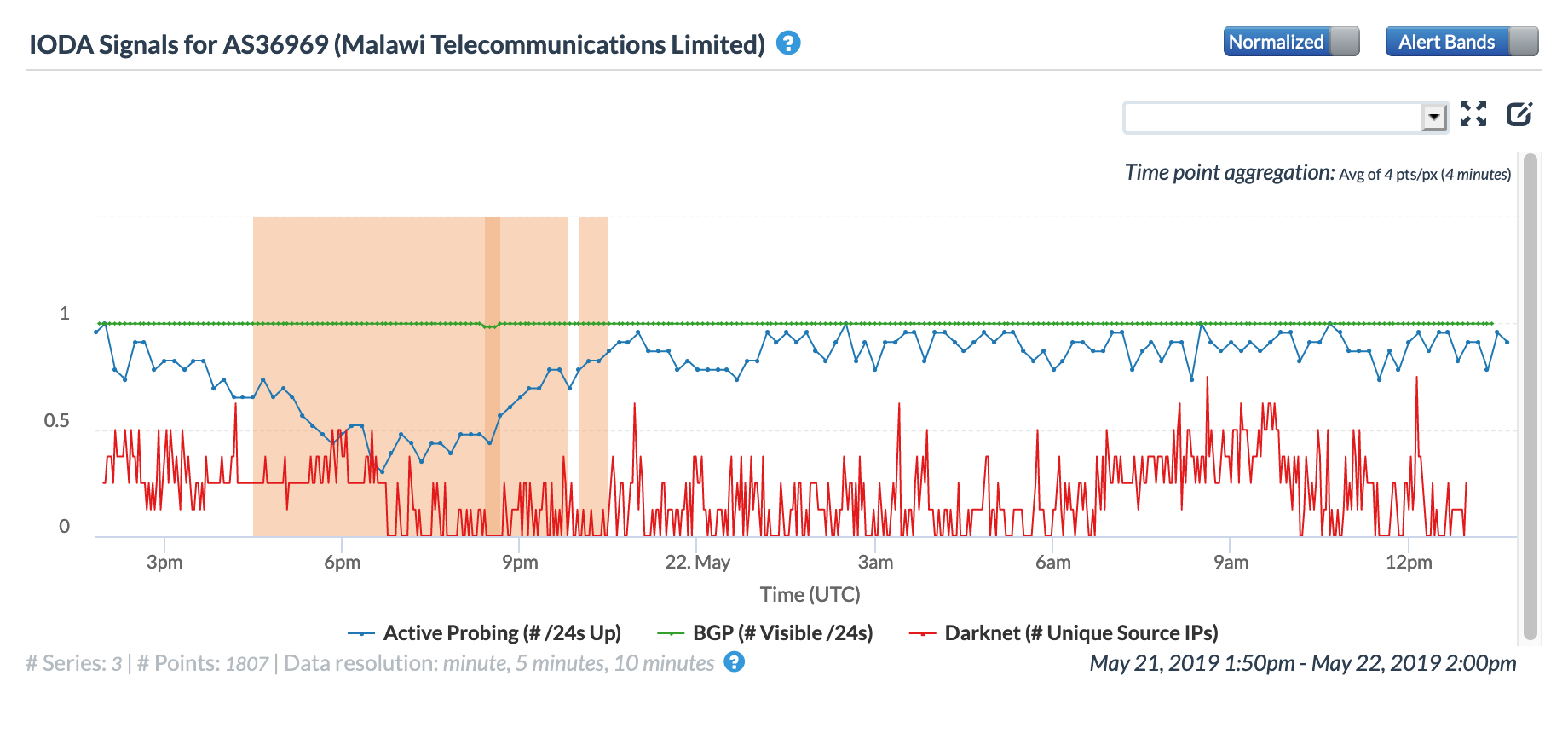
The disruption also impacted local media outlets, as seen in the Facebook post below from Mibawa TV.
Satellite Suspicions
During May 2019, several Internet disruptions were observed that appear to be related to a reliance on satellite connectivity by major telecommunications providers in the impacted countries. In each case, the observed country-level disruption is coincident with a drop in the number of completed traceroutes reaching endpoints on the providers’ networks through satellite connectivity providers. In the figures below, the disruptions in South Sudan, Solomon Islands, Kiribati, and Cook Islands appear to be related to issues with O3b, while in Eritrea, connectivity through Asia Broadcast Satellite was problematic.
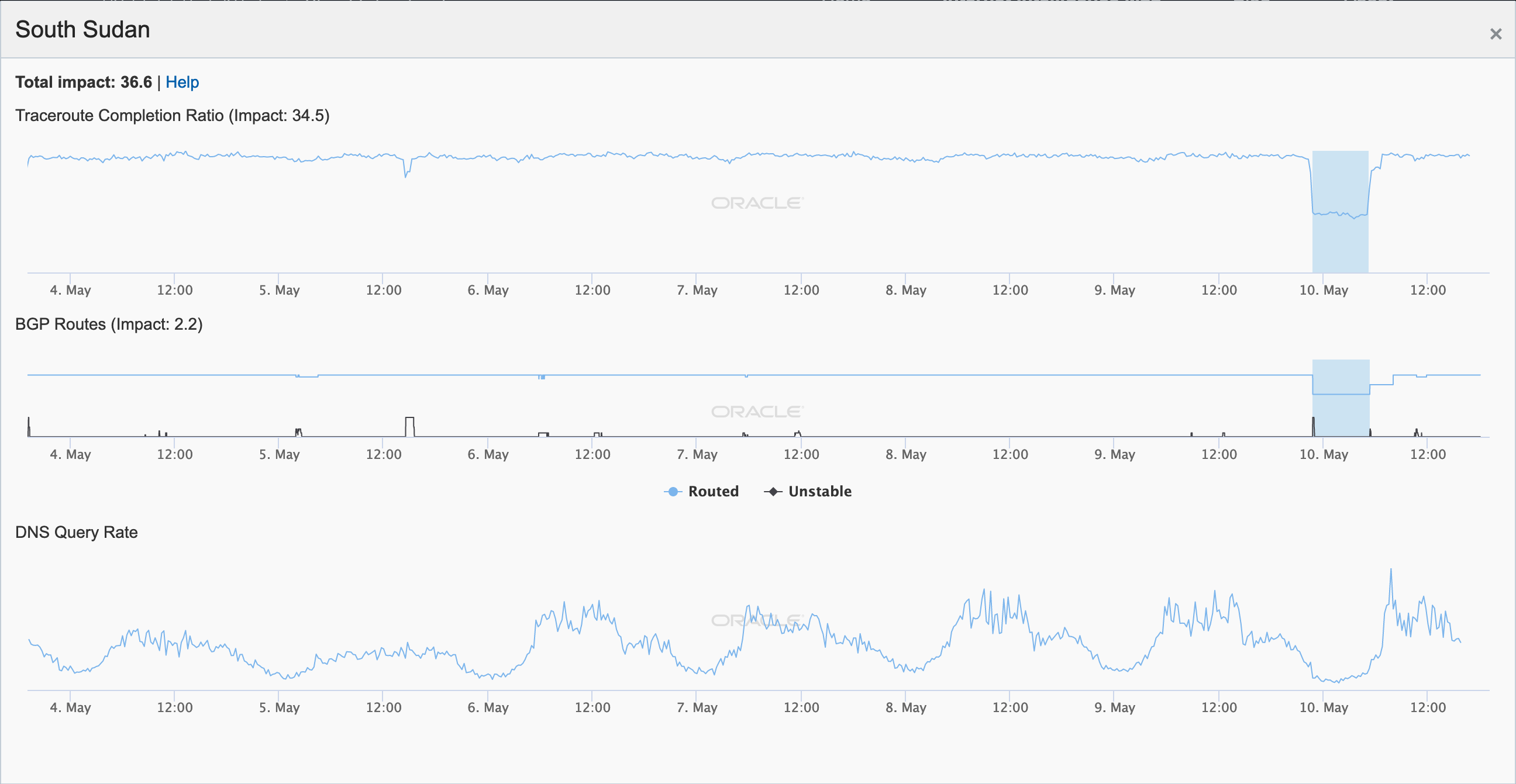
Oracle Internet Intelligence Map Country Statistics graph for South Sudan 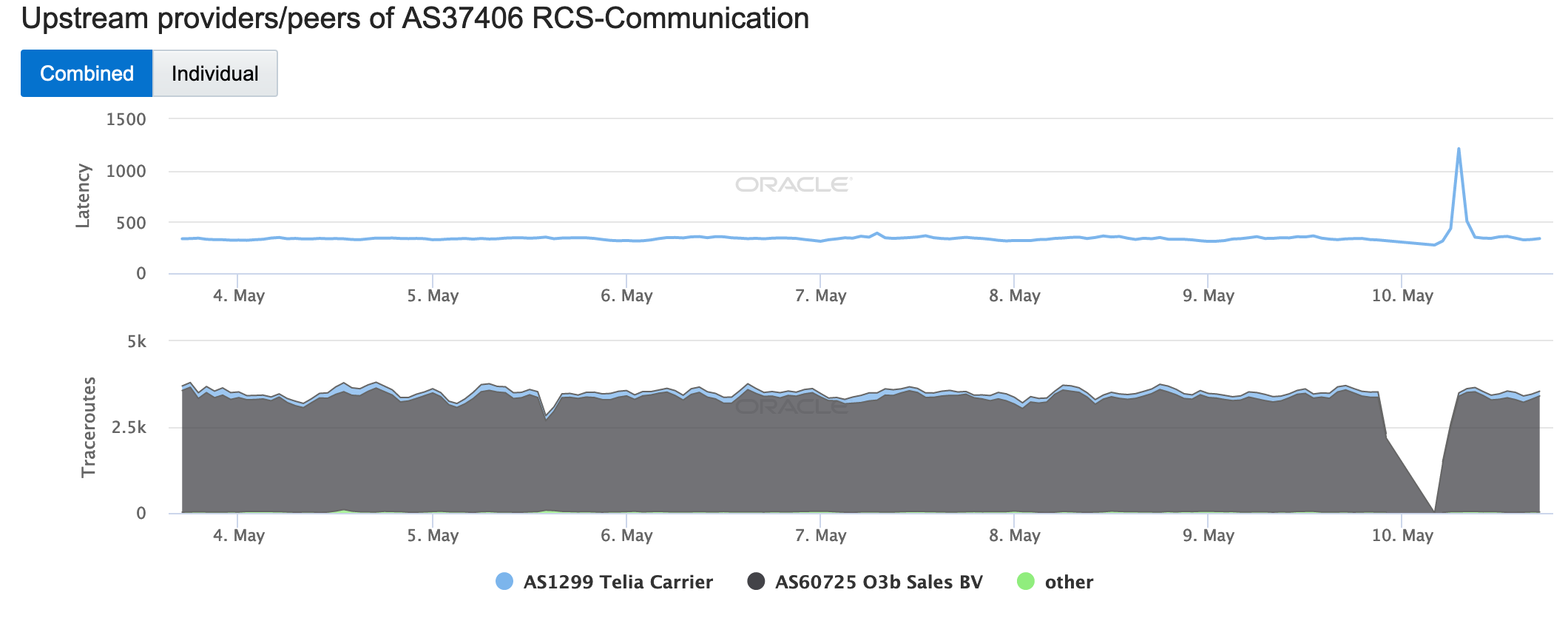
Oracle Internet Intelligence Map Traffic Shifts graph for AS37406 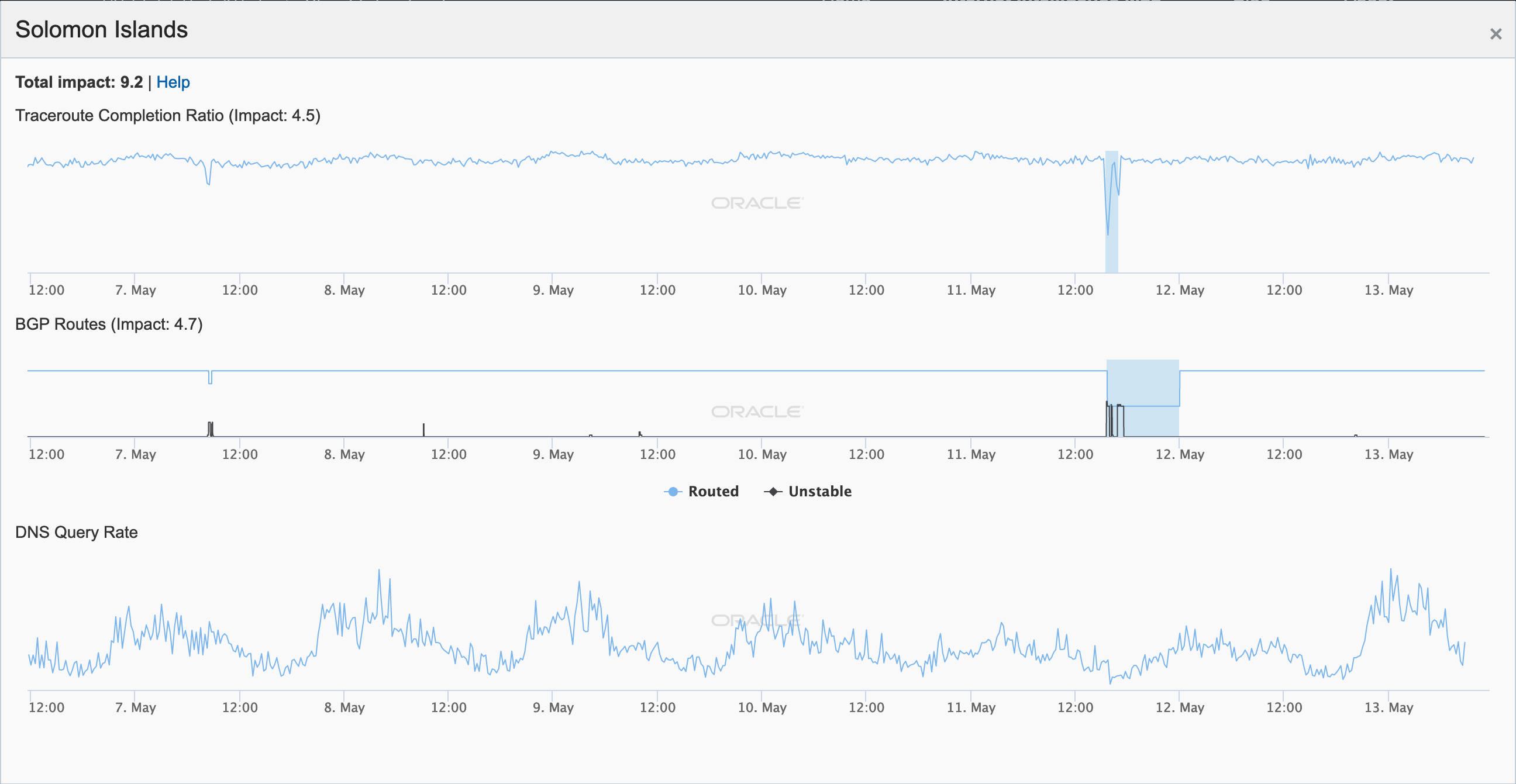
Oracle Internet Intelligence Map Country Statistics graph for Solomon Islands 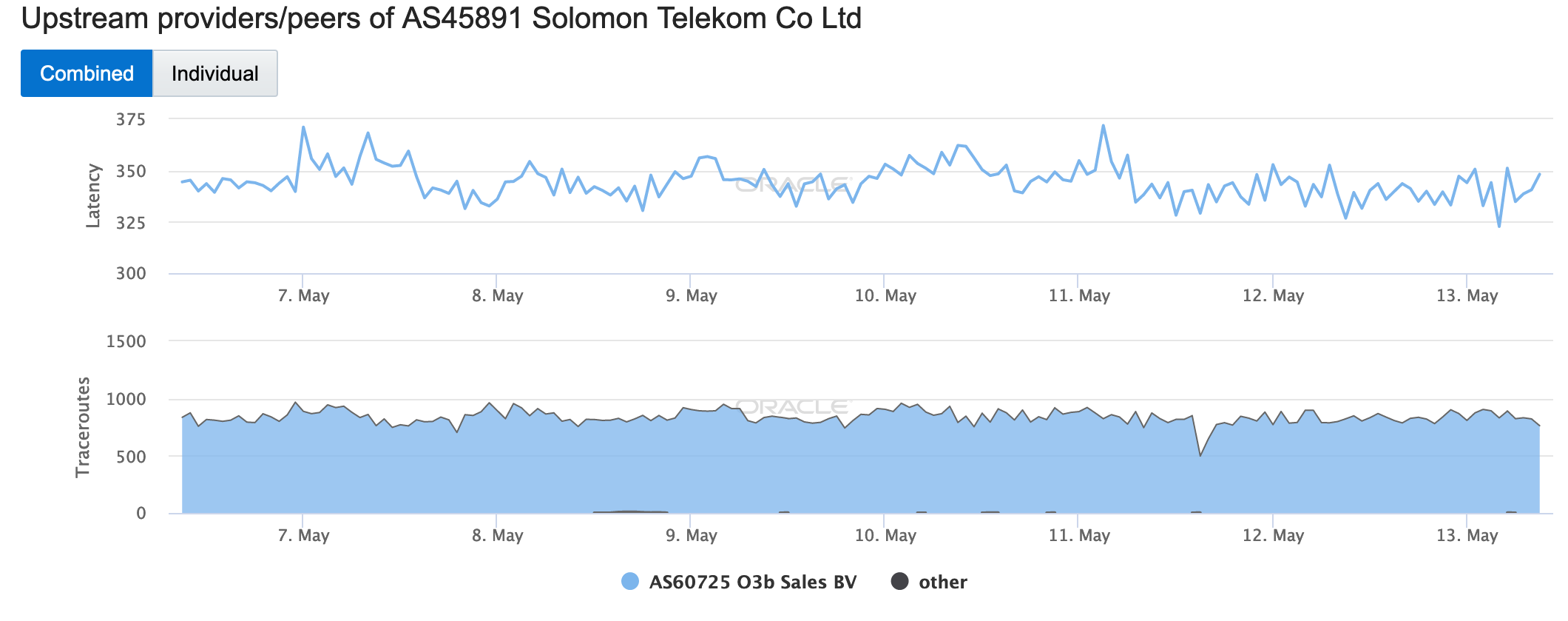
Oracle Internet Intelligence Map Traffic Shifts graph for AS45891 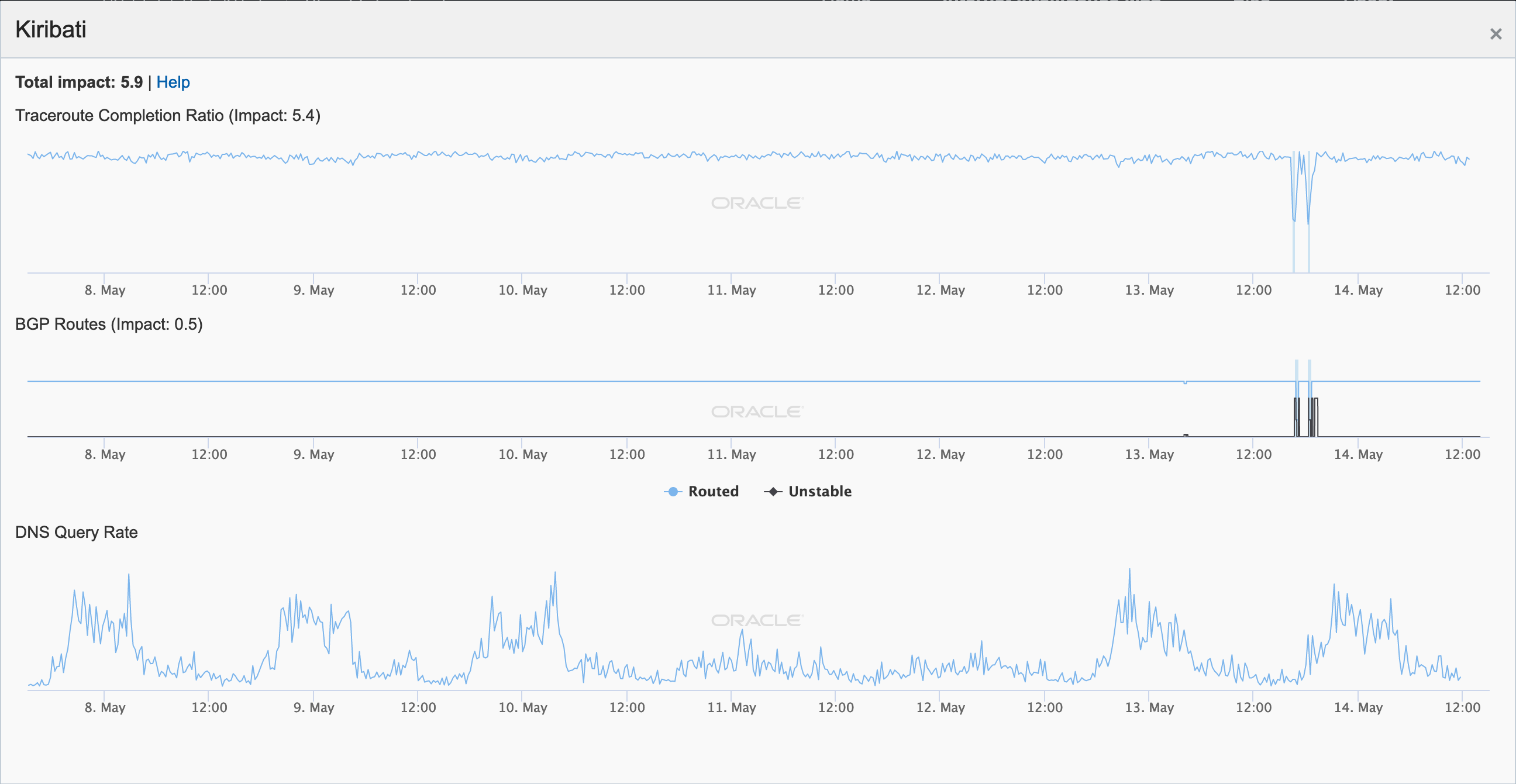
Oracle Internet Intelligence Map Country Statistics graph for Kiribati 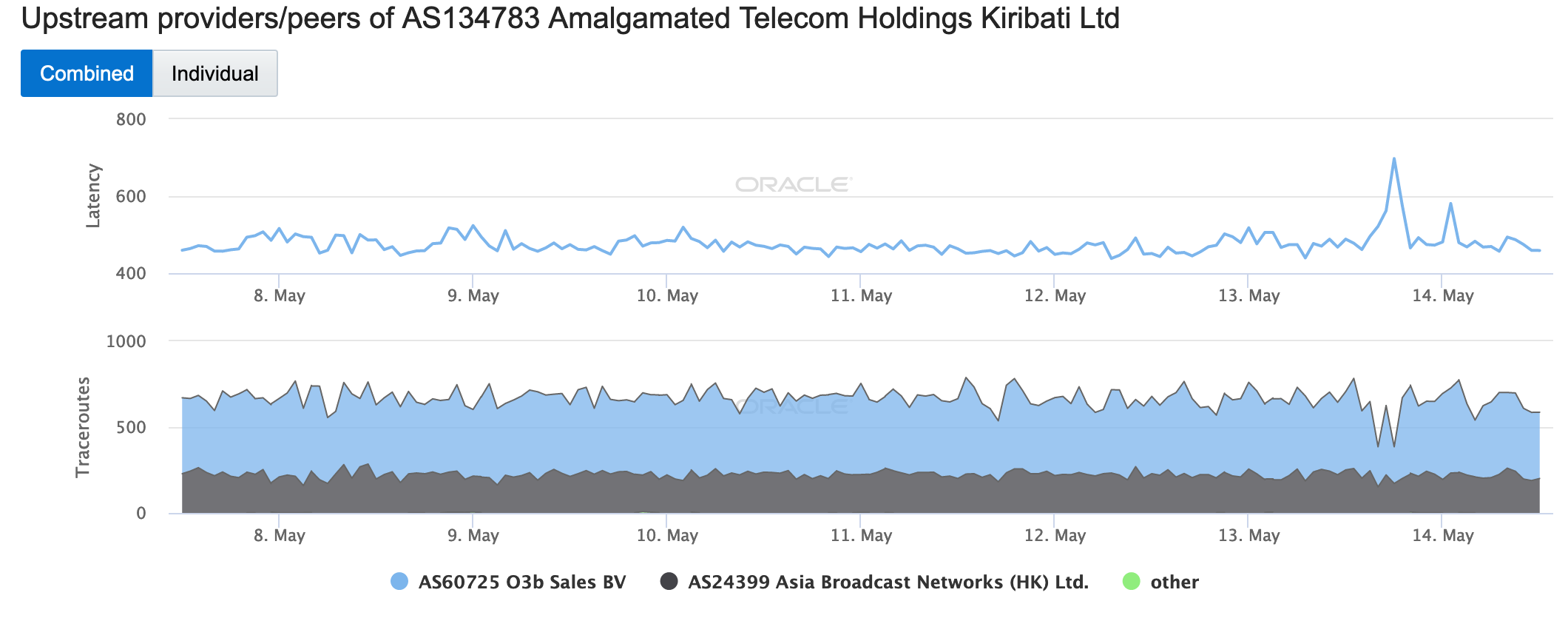
Oracle Internet Intelligence Map Traffic Shifts graph for AS134783 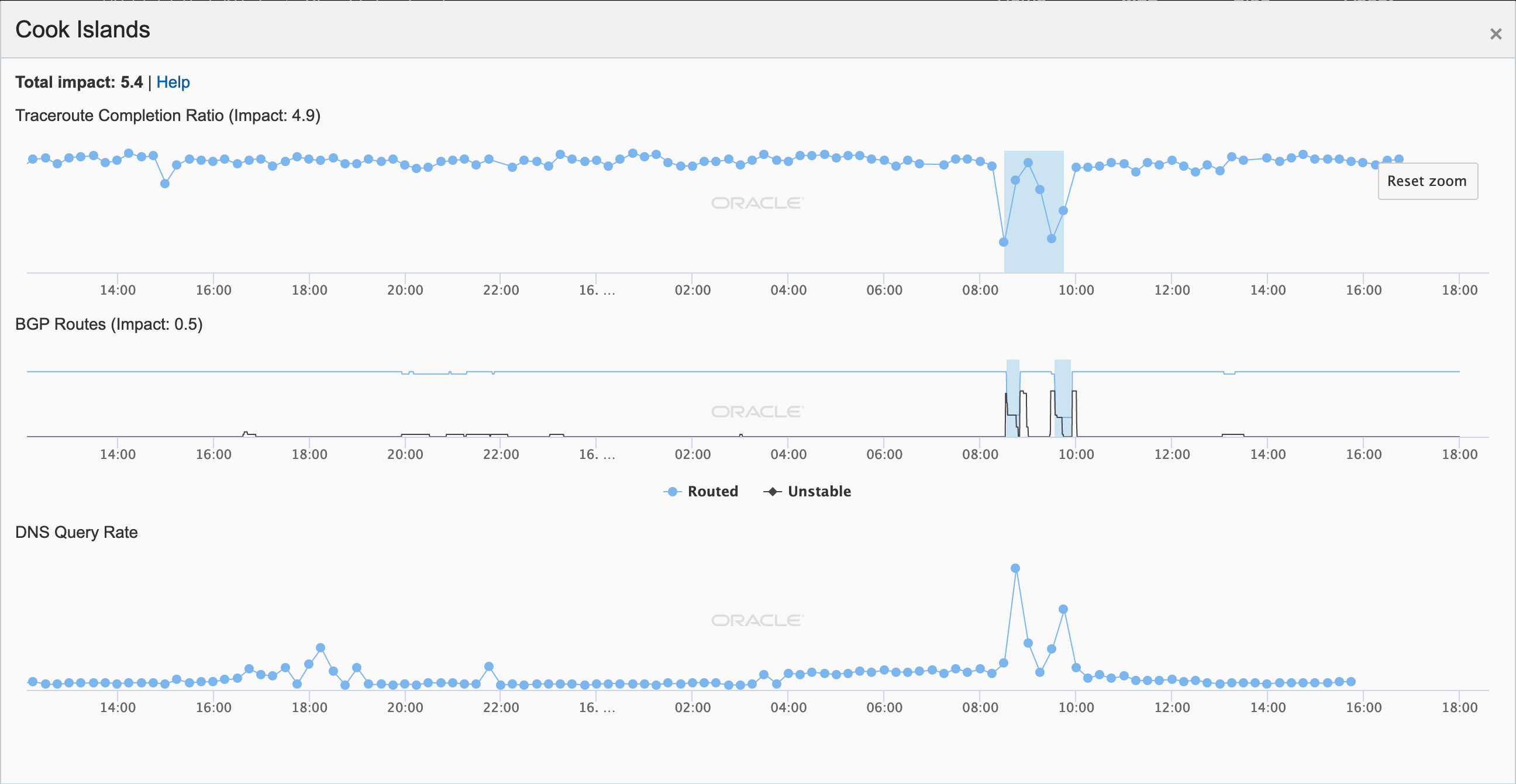
Oracle Internet Intelligence Map Country Statistics graph for Cook Islands 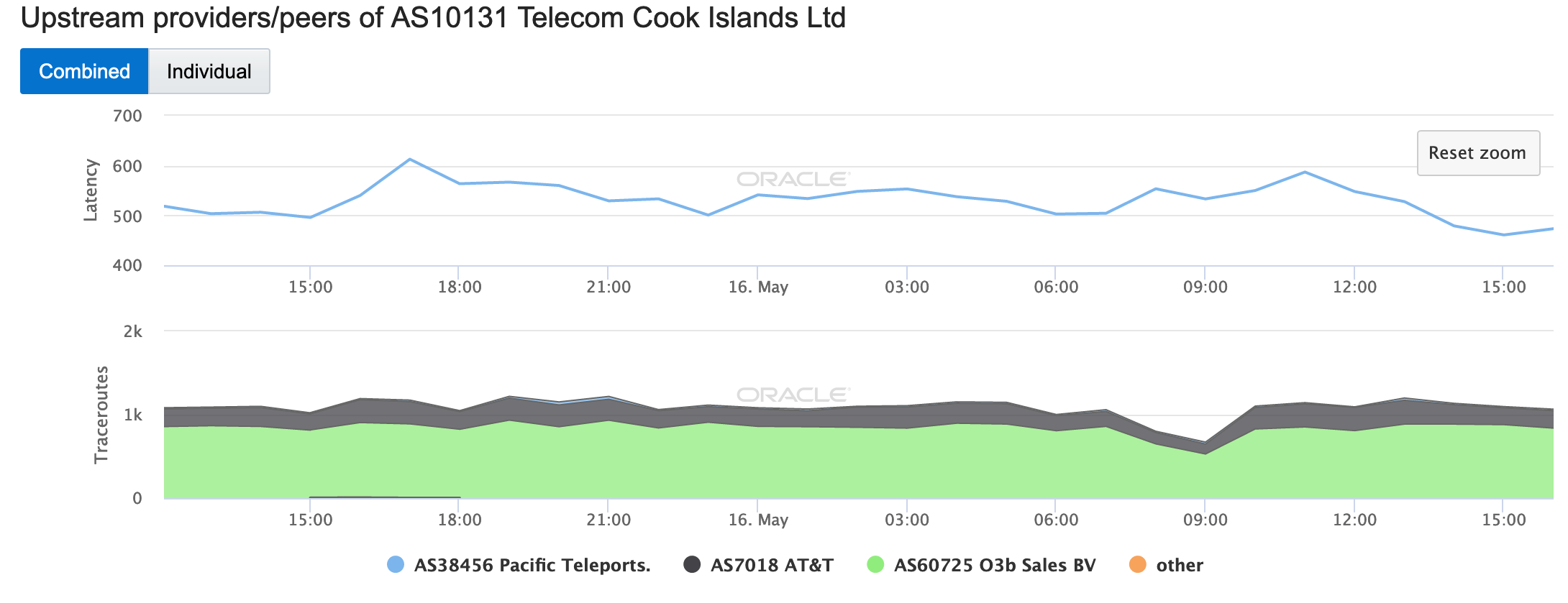
Oracle Internet Intelligence Map Traffic Shifts graph for AS10131 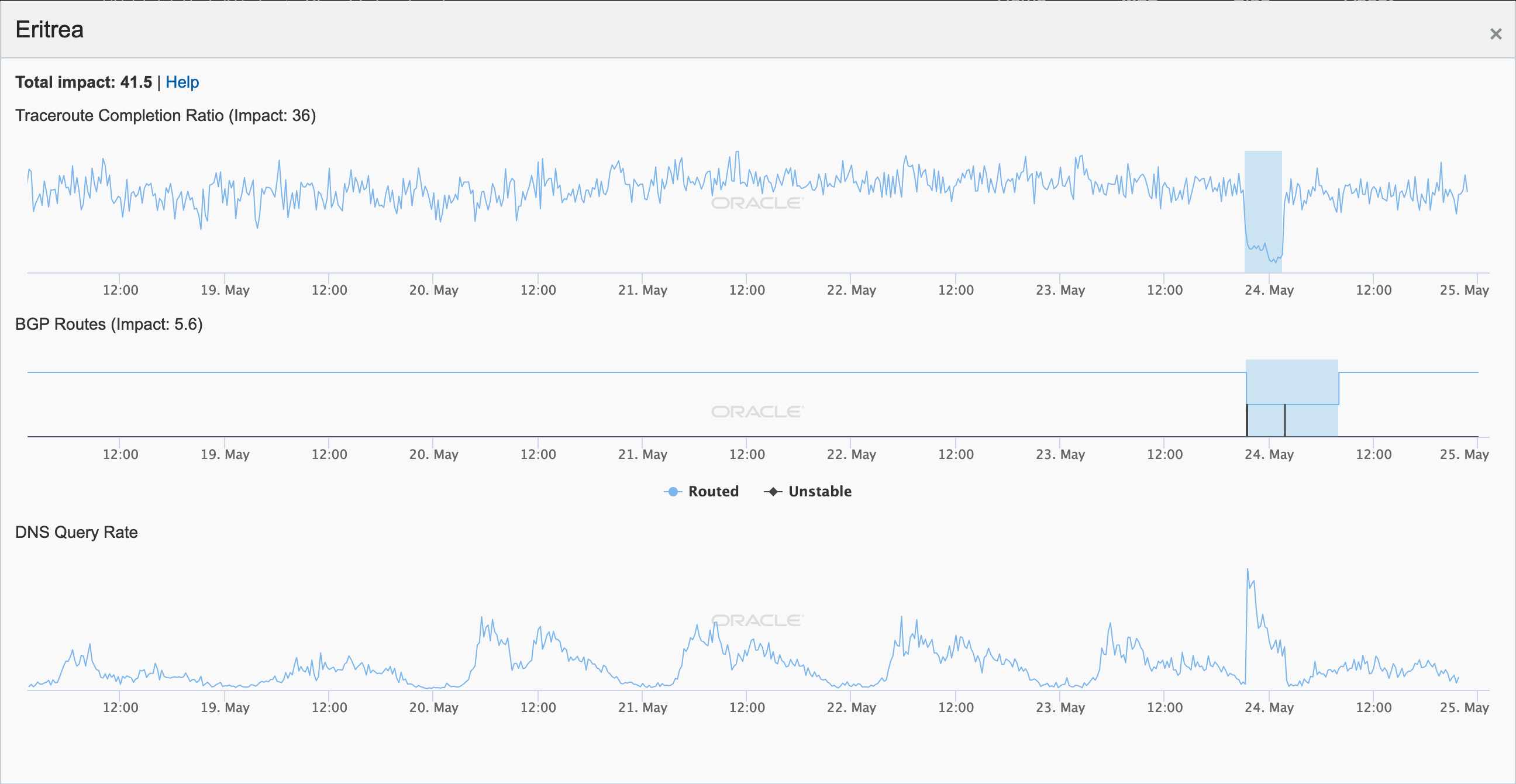
Oracle Internet Intelligence Map Country Statistics graph for Eritrea 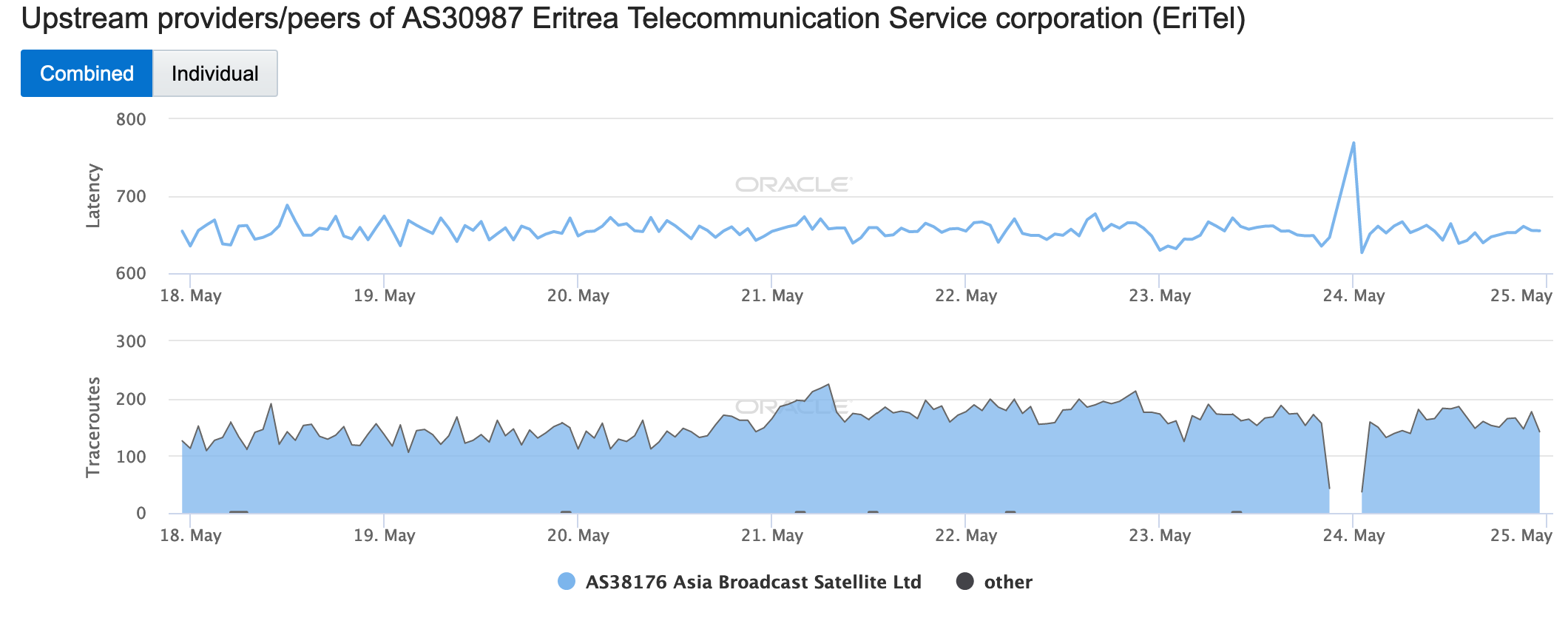
Oracle Internet Intelligence Map Traffic Shifts graph for AS30987
Wayward Weather
Damage caused by severe weather events frequently wreaks havoc on electrical and communications infrastructure. In early May, a storm in the U.S. Virgin Islands impacted Internet connectivity for users across multiple networks within the territory. Reduced levels of successful traceroute completions and active probing can be seen late in the day (UTC) on May 1 in the figures below.
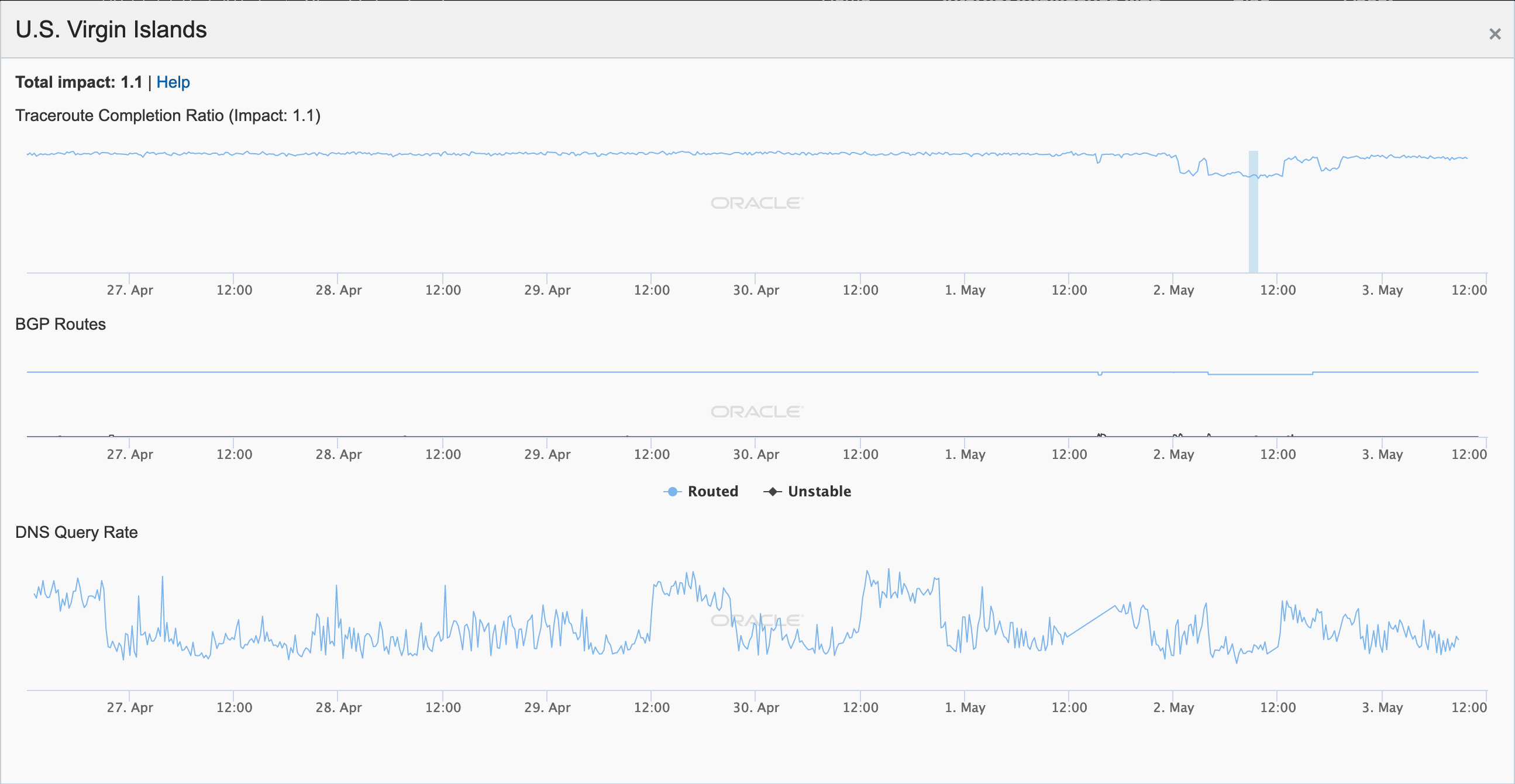
Oracle Internet Intelligence Map Country Statistics graph for U.S. Virgin Islands 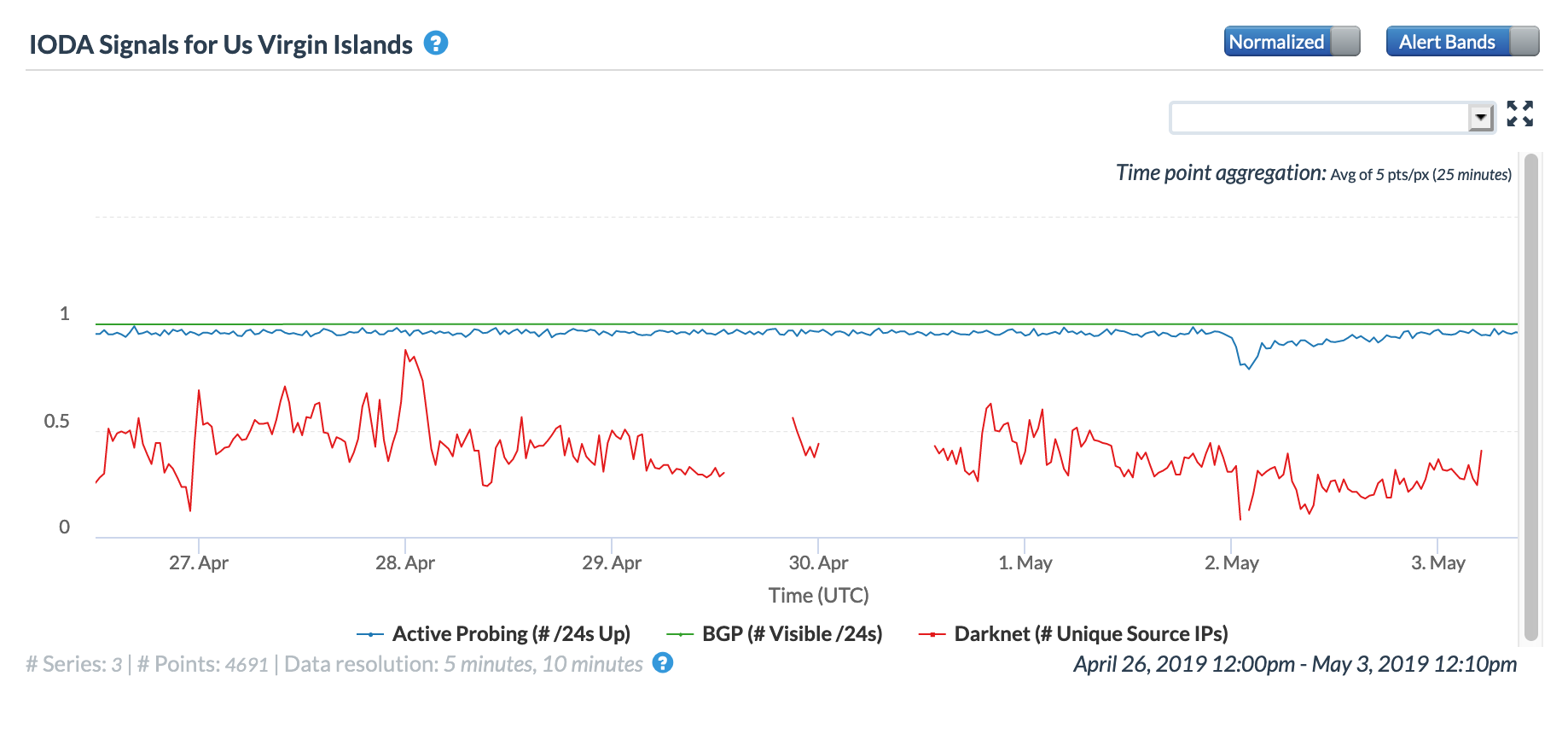
CAIDA IODA graph for U.S. Virgin Islands
These disruptions were also visible in network-level graphs for local network providers, as seen in the figures below. A Facebook thread highlighted issues with Broadband VI, and a Facebook Messenger response from a representative of Virgin Islands Next Generation Network noted “Our IT Team has indicated that there was a storm affecting the island of St. Croix on Wednesday, May 1. We were able to confirm with Broadband VI that they experienced a lightning strike. This appears to correspond with what you observed.”
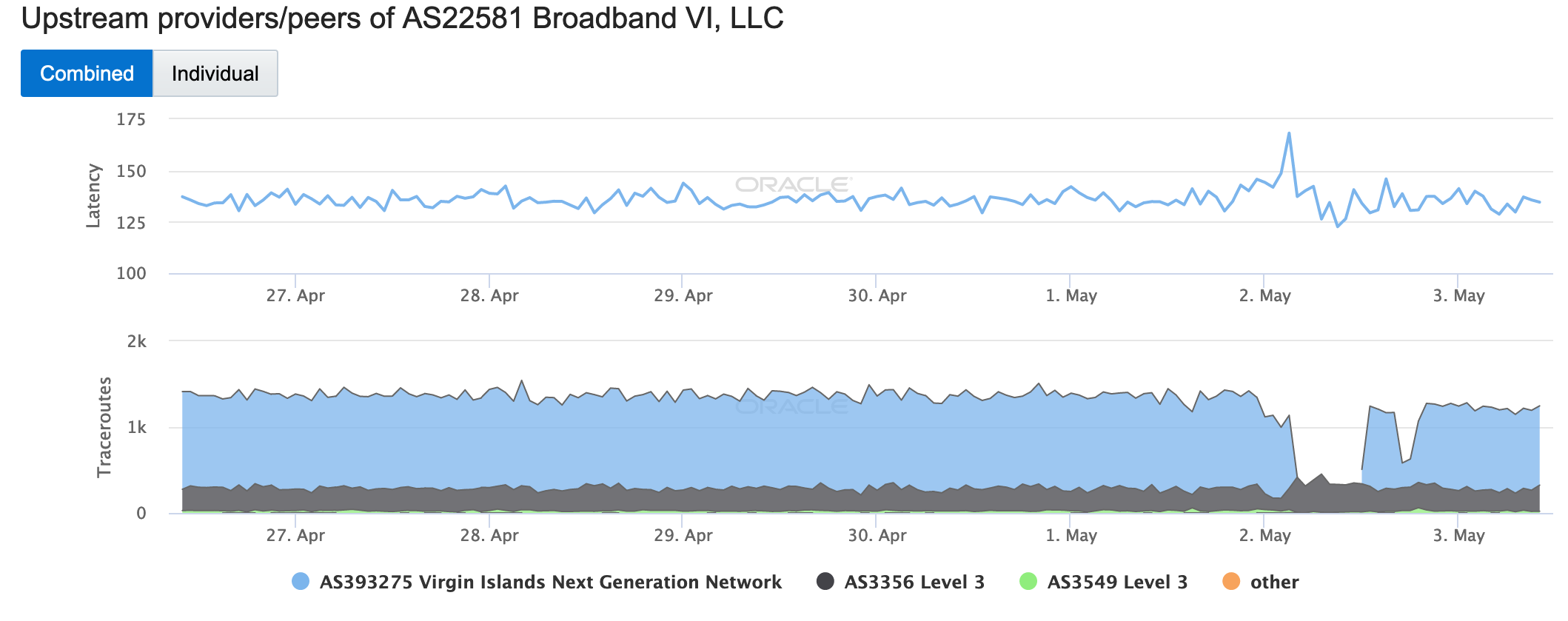
Oracle Internet Intelligence Map Traffic Shifts graph for Broadband VI 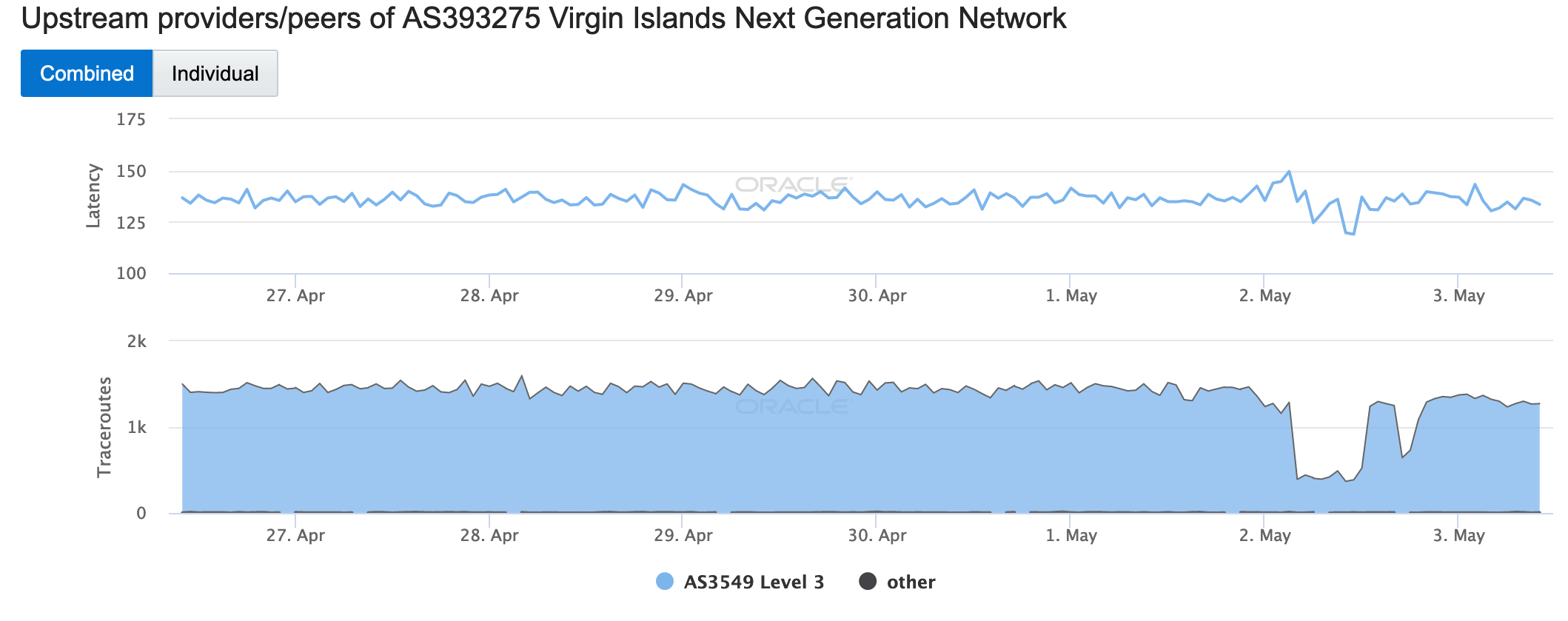
Oracle Internet Intelligence Map Traffic Shifts graph for Virgin Islands NGN
The highly localized impact of extreme weather was highlighted by CAIDA’s IODA team towards the end of the month. In the Tweet embedded below, the team shared graphs of disruptions in active probing to endpoints in two Ohio counties on May 28, with the disruption timeframes correlating with reports of a tornado in those areas.
Other Outages
In addition to the disruptions discussed above that had frequently seen (probable) underlying causes, several additional disruptions were observed in May that were significant enough to mention here as well.
On May 5, the @BGPStream Twitter feed posted 70 “outage” alerts for autonomous systems (ASNs) associated with the United States Department of Defense, all at 01:51 UTC. BGPStream maintainer Andre Toonk explained what happened in the Tweet embedded below, highlighting the risk of single-homing multiple networks behind a single provider.
Just over a week later, on May 13 a significant Internet disruption was observed in China, apparently due to an issue at China Telecom. This event was explored in more detail in a previous post: “Multi-Hour Disruption at China Telecom”.
On May 22, published reports (The Straits Times, The Independent) indicated that thousands of fiber broadband subscribers of Singapore provider M1 (MobileOne) experienced a multi-hour Internet disruption, but M1 did not say what caused the disruption. Interestingly, it occurred a day after hundreds of customers of three local providers – Singtel, StarHub and M1 – had Internet connectivity disrupted by a fiber cut at Netlink Trust, which owns Singapore’s fiber network and resells fiber connectivity to these telecommunications providers.
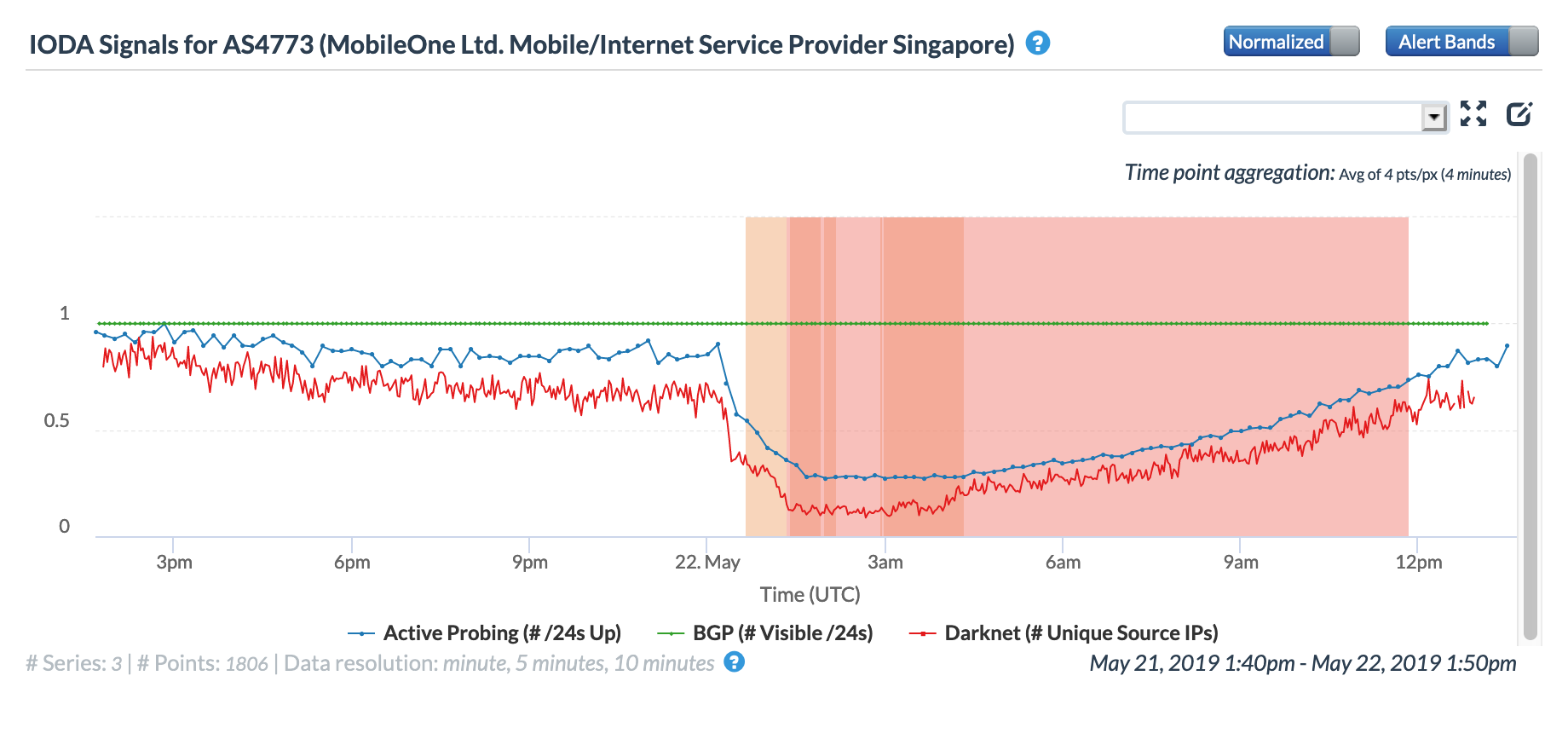
Conclusion
Physical damage to terrestrial and submarine cables has long been a cause of Internet disruptions, as has problems with satellite communications for those regions underserved with wired connectivity. The continued growth in both submarine cable buildout and satellite Internet services should help provide redundancy and resiliency, reducing the frequency and severity of large-scale Internet disruptions. However, these additional avenues of connectivity will not change the likelihood that government-directed Internet disruptions will continue to occur (probably becoming more targeted and frequent), nor will they mitigate transient disruptions impacting local areas or individual network providers.
]]> Considerable Internet
Considerable Internet  Live map and analysis
Live map and analysis

 Mapa en vivo y análisis
Mapa en vivo y análisis
 Live status
Live status 